API Security has risen to the top of the priorities list for CISOs and security teams. As misconfigured APIs have increasingly been a primary attack vector in cyber attacks in recent months, the need to strengthen API security efforts is of critical importance. Insecure APIs potentially provide cybercriminals with a direct line to access personally identifiable information (PII) and other sensitive information, making it essential to know which APIs you have and whether they are exposed.
Gartner writes* that “API security challenges have emerged as a top concern for most software engineering leaders, as unmanaged and unsecured APIs create vulnerabilities that could accelerate multimillion dollar security incidents.”
Agentless Technology Brings More Comprehensive Visibility
In October 2022, Orca released the industry’s first fully agentless API Security capabilities, a primary component of our comprehensive Cloud Security Platform, to help organizations identify, prioritize, and address API-related misconfigurations and security risks across their multi-cloud environment.
As opposed to agent-based or network-based approaches that only provide partial insight into the APIs on the servers that they reach, Orca leverages its patented SideScanning™ technology and comprehensive insights into cloud workloads and configurations as well as dynamic public endpoint scanning to provide security teams with a full and continuously updated inventory of APIs, their security posture and drift status.
We are excited to share our latest API security capabilities that provide organizations with the following benefits:
- An expanded inventory of web and API assets: Have an extensive view of the API attack surface with a continuously up-to-date inventory.
- Posture Management: Greater understanding of where web and API entities are exposed.
- API Risk Prioritization: Clarity of where to prioritize efforts to mitigate risks as strategically as possible.
Let’s look at each of these capabilities in depth.
API Inventory with Expanded Coverage
API Security needs to start with full insight into which APIs are running in the cloud environment. Orca’s ‘API Security View’ dashboard provides cloud and application security teams with an overview of all high-level API data and alerts. We’ve increased and improved the insights you’ll find on this page.
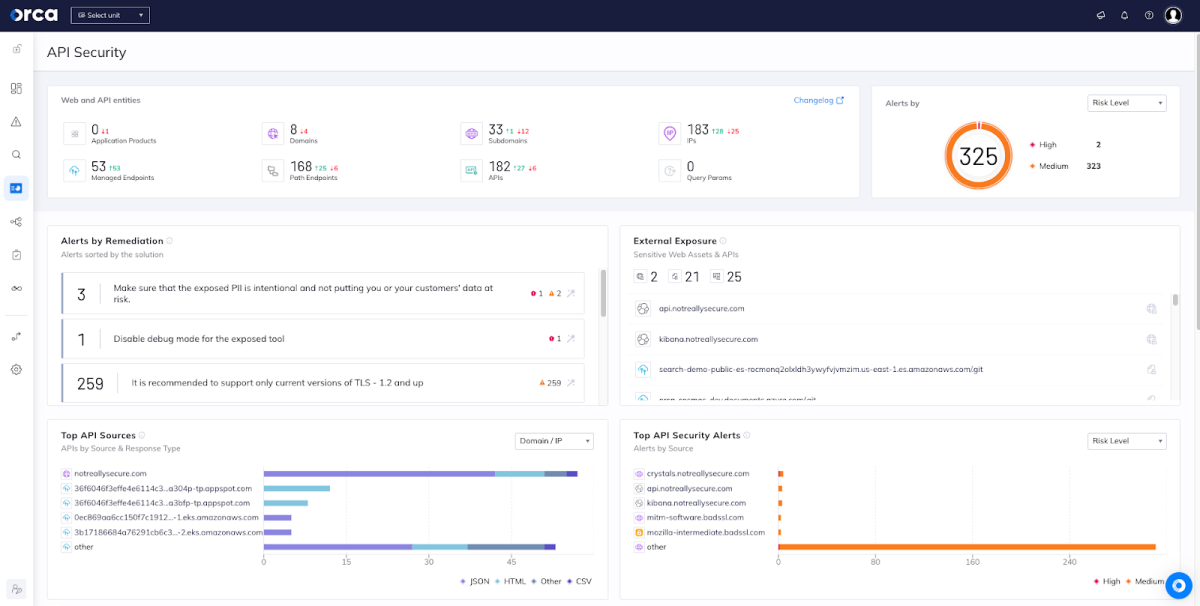
Detect Risks on Amazon API Gateway Endpoints and Serverless APIs
We expanded our coverage of managed and unmanaged API endpoints, including discovering and identifying associated security risks on both Amazon API Gateway endpoints and serverless APIs. Unlike API security tools that are network-based or rely on agents, Orca’s agentless approach provides easy onboarding for these services, without the need for tedious manual processes.
Amazon API Gateway is a fully managed AWS service for creating, publishing, maintaining, monitoring, and securing REST, HTTP, and WebSocket APIs at any scale. Developers can use it for building serverless applications, integrating with legacy applications, or proxying HTTP requests directly to other AWS services. Orca is able to extract and analyze data from access logs to discover and analyze all of API Gateway assets.
A serverless architecture is a way for organizations to build and run applications and services without having to manage the underlying infrastructure. Applications still run on servers, but the responsibility for server management rests with the cloud provider, utilizing a pay-for-when-you-use-it model. This reduces the cost of DevOps and enables developers to focus on their product without being limited by server capacity. All of the three largest cloud providers have services for serverless computing: AWS Lambda, Azure Functions, and Google Cloud Functions.
However, the challenge for security teams is that these services are very decentralized. There is a lack of visibility into the cloud vendor-managed infrastructure to see which APIs exist. You cannot install an agent on the operating system, nor can you enforce a gateway for traffic to go through to monitor API endpoints. Additionally, as serverless infrastructure is spun up and down based on application usage, shadow APIs—implemented without security team knowledge or visibility—are a major concern.
Due to Orca’s agentless access to both cloud infrastructure and workloads, and the unique way in which we stitch these data sources together into a holistic, comprehensive view of the API estate, we are able to help teams easily track and analyze their managed and unmanaged API assets, including applications, domains, subdomains, path groups, users, IPs, and API endpoints—including from serverless functions.
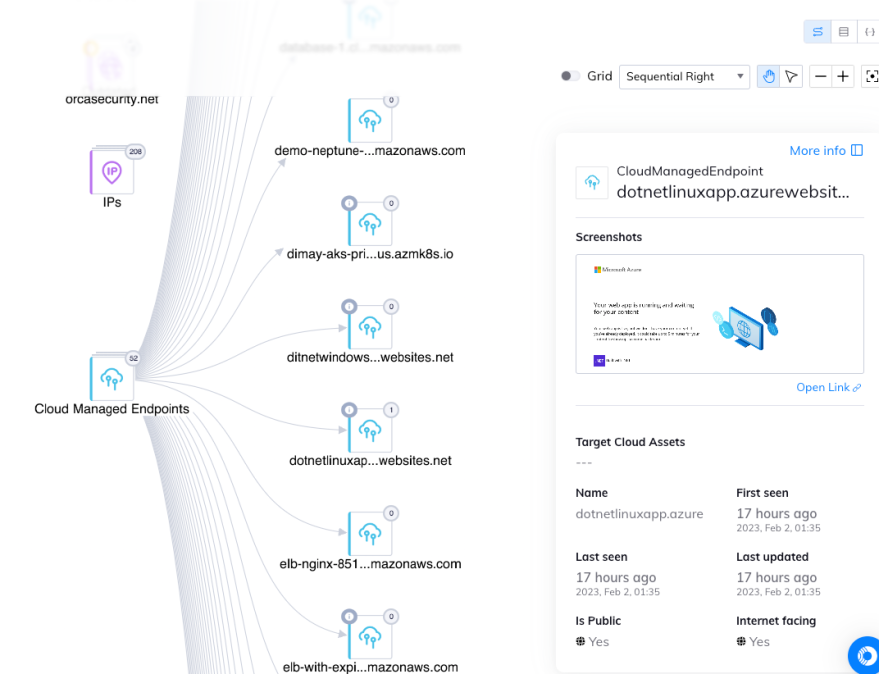
Track IPs and Cloud Managed Endpoints in Graphs
IPs and cloud managed endpoints are now shown using our new API Security graph visualization. The interactive graphs help users gain a complete picture of the relationships between cloud entities and risks that can often impact multiple entities.
With these insights, security teams can be one step ahead of attackers and understand which risks should be strategically remediated to achieve the greatest reduction in the attack surface.
API Risk Prioritization with Enhanced Evidence of Exposure
Orca has added several new and improved capabilities to simplify API risk prioritization and compliance, including the ability to prioritize according to remediation actions, and to view more extensive evidence of when an API is exposed.
These capabilities enable teams to identify and prioritize risks and accelerate mitigation actions with valuable context-based data such as the location of PII, API public exposure, and more.
View Remediation Guidance to Resolve the Most Alerts
Orca’s new Alerts by Remediation widget allows you to view web and API alerts organized by the alert remediations.
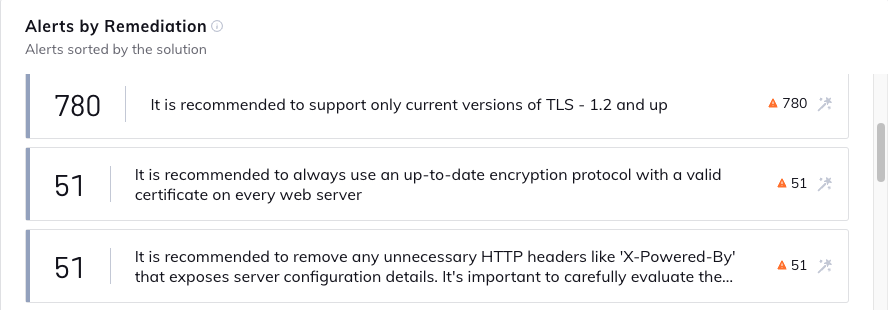
While we often think of risk prioritization as meaning just that—identifying and listing the most prevalent risks themselves—Orca also allows you to view risks by suggested remediations for those risks. This makes API Security alerts more actionable, so you can prioritize not just risks, but which remediations would bring the most immediate benefit to your overall API security posture, by resolving a bulk of alerts.
Let’s take the example (in the above screenshot) of 51 alerts having the same remediation suggestion of “It is recommended to always use an up-to-date encryption protocol with a valid certificate on every web server.” These alerts include when a subdomain or IP server is serving unencrypted public content, making it susceptible to data leakage via Man in the Middle attacks, or as MITRE calls them Adversary in the Middle attacks.
By clicking on the “magic wand” icon to the right of the remediation suggestion, you will see that Orca provides a detailed and clear list of steps needed for effective remediation.
Expanded API Security External Exposure Widget
Orca has improved the External Exposure widget to cover additional use cases, including subdomains with sensitive data, endpoints with PII, and endpoints with sensitive files. Beyond just a list of the exposed entities, these are groups of web and API endpoints with sensitive data and external exposure, to help focus the security team’s attention on the entities that pose the most significant risk so they can take preventive steps.
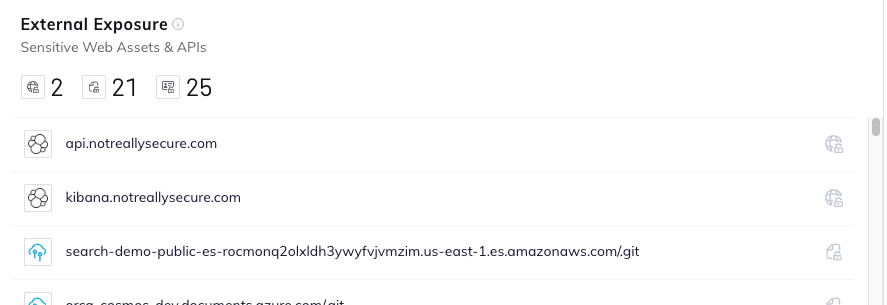
Exposure Data on Attack Vectors to Analyze and Address
From the asset inventory section of the Orca platform, you can now view exposure information links and previews on both the attack vector view and the asset QuickView. As seen in the example below, this includes public and private IP addresses, DNS server information, and more evidence of how the django VM is at risk.
Notice the screenshot of the publicly-exposed API—which can serve as strong proof of the fact that the API is exposed—as well as the JSON response preview. This information helps to increase understanding of the API exposure risk so teams can share data and react accordingly.

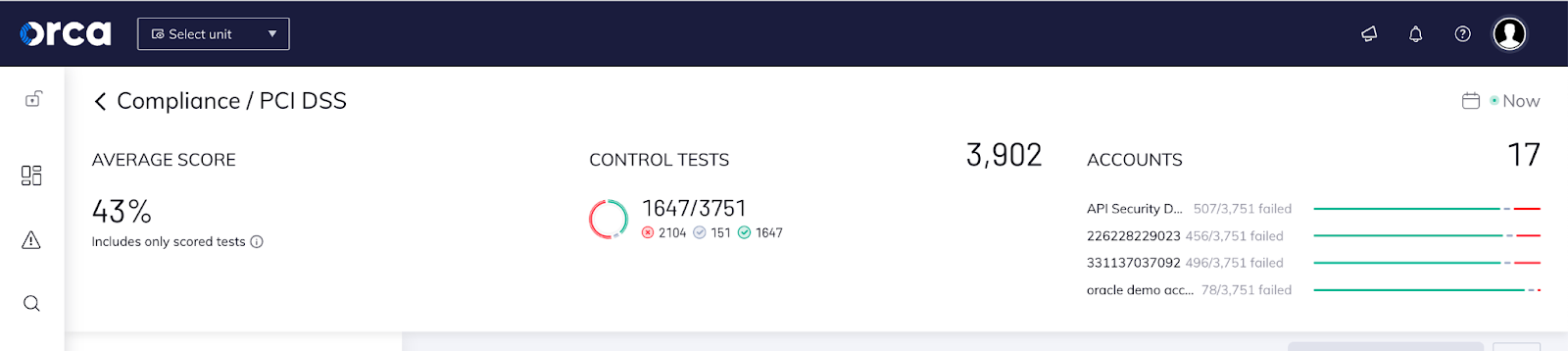
Stronger PCI-DSS Compliance to Stay Ahead of Audits
Orca now displays many web and API security controls within the PCI-DSS compliance framework. This strengthens compliance checks for PCI-DSS and helps compliance teams stay ahead of audits and adhere to PCI-DSS with linked-alerts provided by Orca.
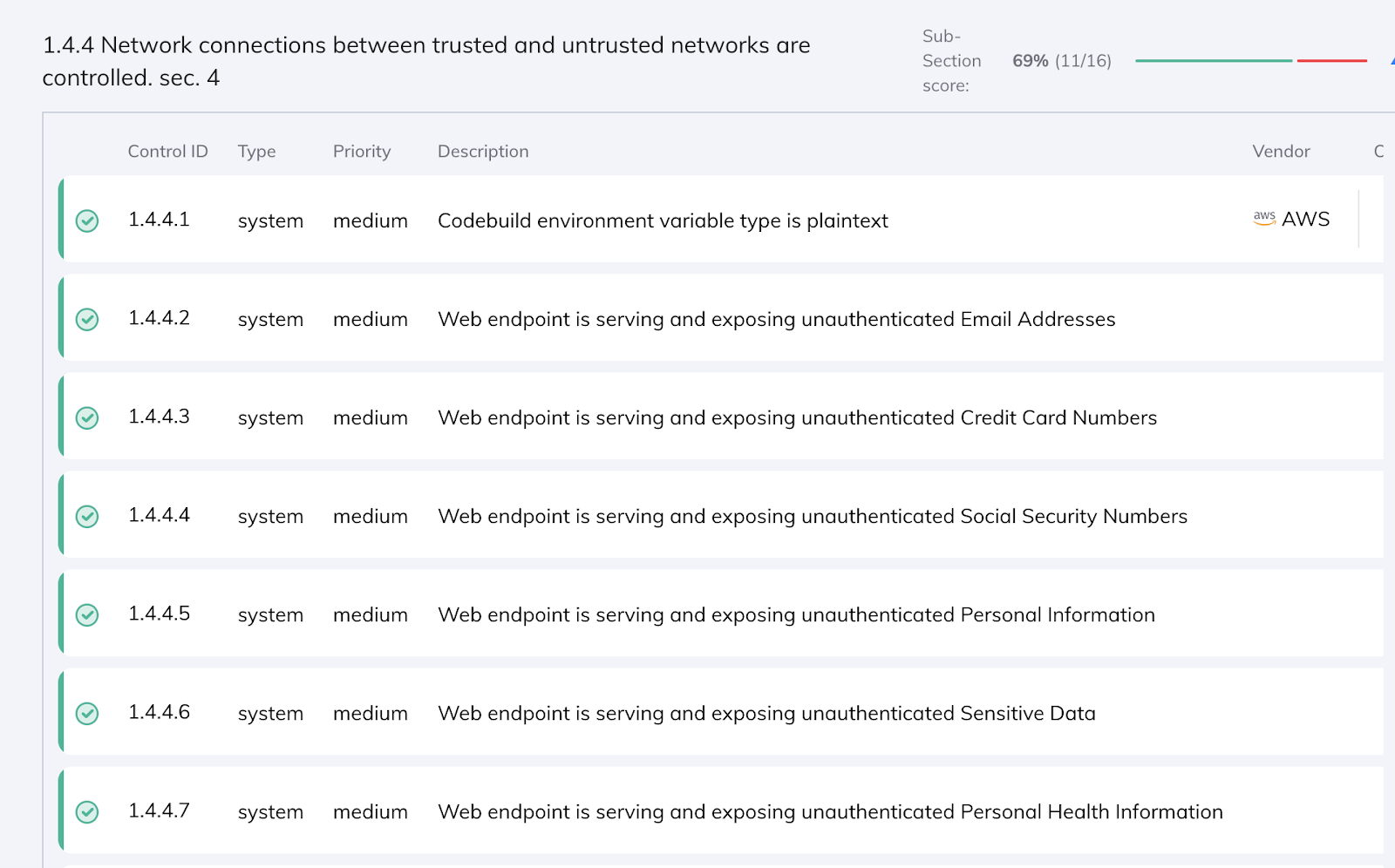
New Swagger View for API Drift Detection and Cross-team Collaboration
Orca’s API drift detection capabilities includes a summary of the newly added and removed applications, domains, subdomains, API paths, and API operations on those paths— in the last specified number of days. You can also see a changelog for the full list of changes, including a search bar to easily search for a particular web or API entity.
But it goes beyond that. For easy comparison to your API schemas, you can now view your web and API inventory in a Swagger/Open API view on the API security view page. Based on specification data collected and analyzed in each API endpoint and related domains and subdomains, Orca generates a Swagger documentation view that can be used to easily compare intended API policy vs. current usage. This helps security teams communicate with their engineering and DevOps teams to ensure that both documentation is updated, as well as facilitate a further understanding of API changes and related risks.
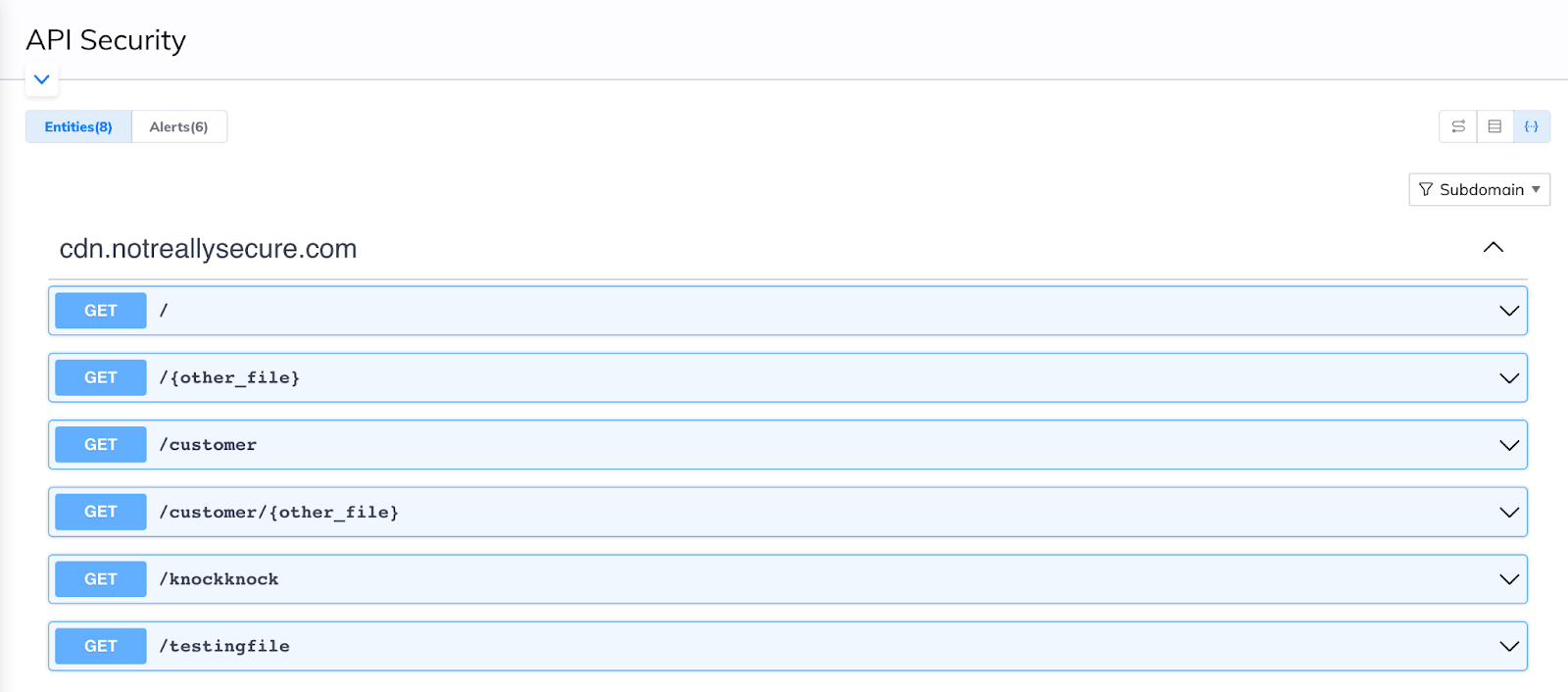
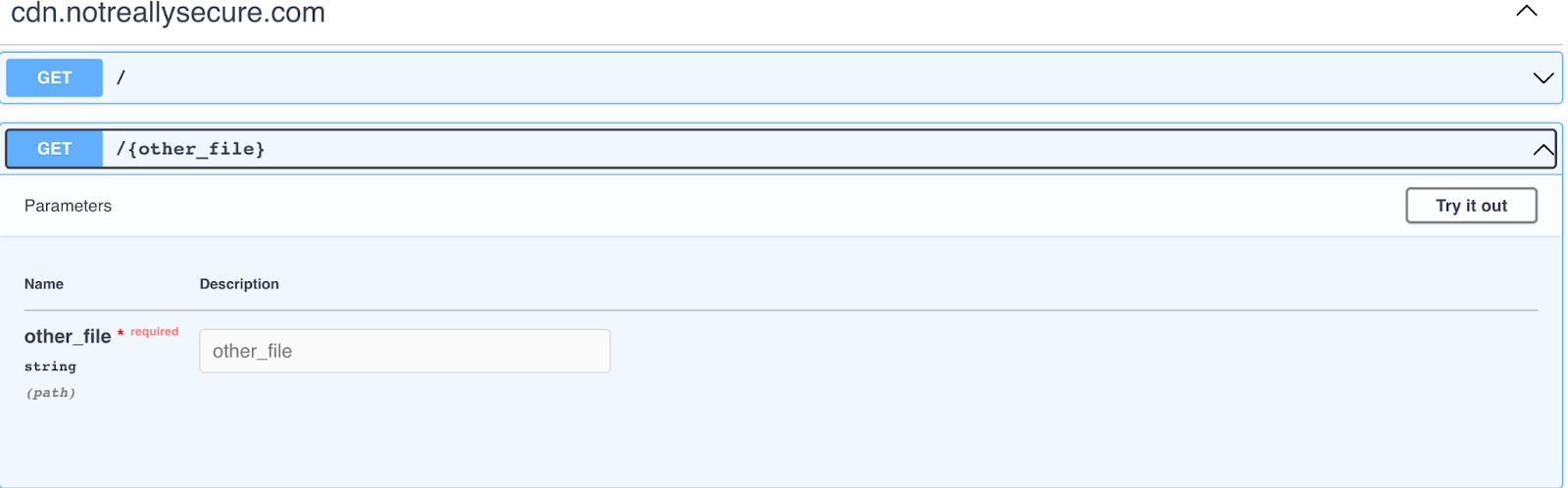
Learn more about Orca Security’s API Security Capabilities
Interested in learning more about Orca’s API Security capabilities? Watch this short explainer video, or view our on-demand webinar Securing APIs in Cloud Native Applications Best Practices.
Ready to try it out in your own cloud environment? Sign up for a Free Risk Assessment to see how quickly and easily the Orca Cloud Security Platform can help you identify and address API risks. Or, request a demo today.
*The link is for Gartner clients – Gartner, Predicts 2022: APIs Demand Improved Security and Management, 06 December 2021, Shameen Pillai Et Al. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.)