In June 2022, the Cybersecurity and Infrastructure Security Agency (CISA) released the Cloud Security Reference Architecture with co-authors United States Digital Service and Federal Risk and Authorization Management Program (FedRAMP). The publication is intended to provide guidance on migrating to a cloud native ecosystem. Perhaps most importantly, this publication serves as a guide for accelerating the speed of cloud adoption for the Federal Government while setting the table to have security built in rather than bolted on. This is relevant when considering the recent announcements by the CIA and FBI that cyber threats pose the ‘biggest long-term threat to economic and national security’. In a previous blog post, Orca Security provided an overview and valuable insights into the guidance provided by CISA, US Digital Service, and FedRAMP in “Understanding CISA’s Cloud Security Technical Reference Architecture”. There are other important and relevant pieces to this publication addressing shared services, cloud migration strategies, and Cloud Security Posture Management (CSPM), that will be discussed below.
Shared Services Layer and the Shared Responsibility Model
One of the more robust sections in CISA’s Cloud Reference Security Architecture publication revolves around the Shared Services Layer. This section includes descriptions on cloud service models, FedRAMP roles and responsibilities and special security considerations required by FedRAMP on continuous monitoring, incident response and the authorization boundary. A key pillar in the Shared Services Layer is understanding the shared security responsibilities of the differing cloud services offerings. The graphic below displays where these responsibilities reside and who’s responsible.
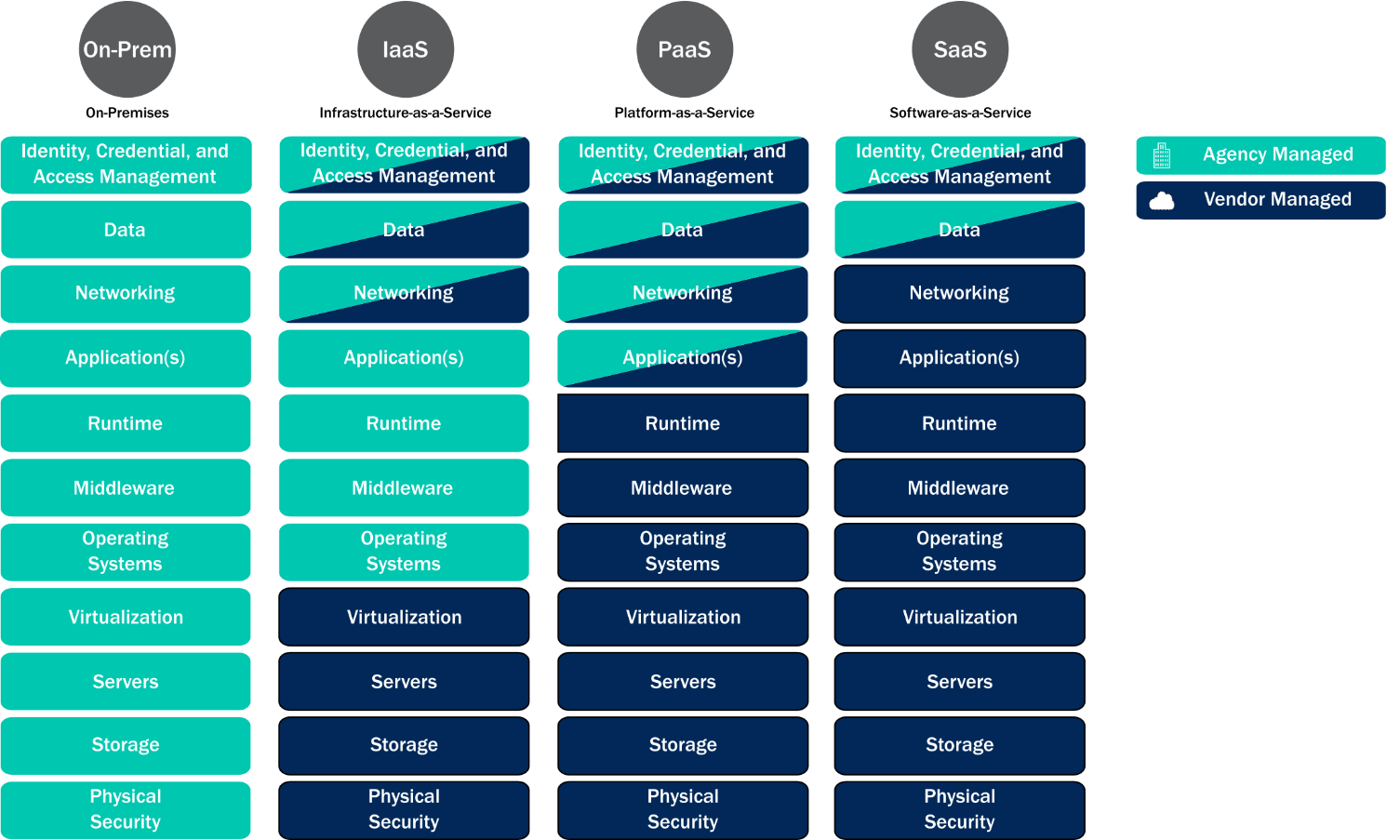
It’s important to note that Software as a Service (SaaS) vendors carry much of the responsibility for security of their environment and the services they’re providing. When consuming SaaS services, organizations and agencies should ensure that they understand where their responsibilities end and Cloud Service Provider (CSP) responsibilities begin. Another interesting topic in this section is sub-agency service consumption of the SaaS service and how that sub-agency can inherit the security controls included in the SaaS offering, but are still responsible for ensuring alignment with incident response, log management, identity and access controls, and configuration management. This last part is similar to if the sub-agency were procuring the CSP service itself.
Multi-Cloud Usage and Government Security
Another core component to this section centers on multi-cloud. The fundamental point here is that an agency or organization consuming multi-cloud services should take steps to enable a holistic view of security across this type of ecosystem. This type of holistic view enables the enterprise to maintain a coherent security posture, allowing for consistent response to vulnerabilities and events that may pose risk to their security posture. This approach also ensures that organizations and agencies are in alignment with the OMB Memorandum (M)-21-31 for log management.1 This is a very important part of the Shared Services Layer and is centered on the concept of continuous monitoring, a critical component of FedRAMP and maintaining FedRAMP authorization.
1 “Improving the Federal Government’s Investigative and Remediation Capabilities
Related to Cybersecurity Incidents,” Office of Management and Budget, (2021), https://www.whitehouse.gov/wp- content/uploads/2021/08/M-21-31-Improving-the-Federal-Governments-Investigative-and-Remediation- Capabilities-Related-to-Cybersecurity-Incidents.pdf.
Considerations for Migrating to the Cloud
The Cloud Migration section of this publication also deserves attention as it addresses several considerations agencies and organizations should take when moving or expanding their cloud estate. For example, when an organization or agency designs software for their cloud, they should be including security as “far left” as reasonable in their Software Development Lifecycle. This means they should empower their DevOps and DevSecOps teams with the tooling and support to create environments and architectures that are scalable, replicable, and secure in accordance with policy or regulatory requirements (think zero trust).
Additional consideration is given to making sure that the agency or organization undergoing a migration understands the required change in approach from managing on-premises infrastructure to a cloud ecosystem. This includes aspects such as automated security testing, enforcing least privilege access, and centralizing common cloud services (i.e. security services). Centralizing services should be given additional attention as it assists the agency or organization in reducing complexity and resource consumption. The reduction in complexity stems from having a consistent experience or view across the ecosystem allowing for streamlined management and security posture performance. Resource consumption efficiencies relate to simplifying procurement (consistent with a homogeneous ecosystem), system maintenance, and compliance requirements. One other important part of this section is its focus on people and ensuring that proper support and training are provided to those tasked with managing and maintaining the cloud ecosystem.
Implementation of Cloud Security Posture Management (CSPM)
The final section of this publication discusses Cloud Security Posture Management, or CSPM. The publication defines CSPM as ‘a continuous process of monitoring a cloud environment by identifying, alerting on, and mitigating cloud vulnerabilities; reducing risk; and improving cloud security’. This is accomplished through a number of typical security approaches like adapting policies and standards to support the cloud ecosystem, improving identity, credential, and access management (ICAM), infrastructure and application protections, and incident response and recovery procedures. One interesting call out is on data protection, in that the agency or organization should engage with the CSP to understand and determine how the data will be managed and protected. This is important when considering issues like data leakage and data loss and how the agency or organization determines what data should be protected, how it will be protected and who controls access and sharing of that data.
The other special call out is on zero trust and Executive Order 14028 encouraging agencies and organizations to adopt a zero trust architecture as practical for their risk posture and threat landscape. One resource to help develop a strategy can be found in CISA’s Zero Trust Maturity Model. Moreover, CSPM solutions assist with the main security elements, including continuous monitoring and alerting on activities within access logs which help to prevent and identify vulnerable configurations that could result in a breach or loss of data. When viewed holistically, CSPM solutions deliver visibility across the cloud ecosystem, enabling the agency or organization to properly manage its cloud estate in accordance with the CISA Technical Cloud Security Reference Architecture publication, FedRAMP requirements and other associated regulatory and compliance needs.
Final Guidance on the CISA Cloud Security Reference Architecture
For government organizations, it can be overwhelming to implement security while adhering to regulatory requirements and best practices, especially if cloud adoption and migration are underway. Experts at Orca Security would love to help and empower your team to manage cloud risks in accordance with regulatory and compliance frameworks. With capabilities such as Shift Left Security, Cloud Security Posture Management (CSPM) and more, Orca is a Cloud Native Application Protection Platform purpose-built to identify security issues in code repositories and assess against control frameworks like FedRAMP, NIST SP800-53, and HIPAA for your multi-cloud estate.
Looking for a government cloud security solution? Navigate the complexities of government cloud security and compliance effortlessly with the Orca Cloud Security Platform. Learn more about our comprehensive suite of security services built for the government cloud and empower your organization to safeguard sensitive data and meet regulatory requirements with confidence.
Sign up for a free trial or watch an on-demand demo today to learn more!
Further Reading
For further insights and in-depth discussions on cloud security and beyond, consider exploring the following blogs from Orca:







