Table of contents
- What is Code Security?
- What threats does Code Security protect against?
- What are the types of Code Security?
- Benefits of Code Security
- How can you implement Code Security?
- Code Security best practices
- Tools and technologies for Code Security
- What are the challenges of implementing Code Security?
- How does Orca help you deploy Code Security?
- FAQs
According to the Orca 2024 State of Cloud Security Report, 62% of organizations have severe vulnerabilities in code repositories. These vulnerabilities exist in code that could imminently be pushed to production environments, potentially causing data breaches and system compromises. According to the 2024 Verizon Data Breach Investigations Report, breaches caused by vulnerabilities have increased threefold year-over-year, highlighting the prevalence of this risk and importance of properly securing it.
Many organizations race to unveil new innovations without properly securing the application they build and deploy. A staggering 75% of developers feel they need more time to tackle security problems in their code, based on a new Secure Software Development Education 2024 Survey by the Linux Foundation. This highlights a major imbalance between development and security, one that Code Security helps to address early in the software development lifecycle (SLDC).
An essential part of application security, Code Security helps neutralize security risks at the earliest, most efficient, and least disruptive stage of the application lifecycle.
In this guide, we explore the discipline of Code Security, defining what it entails, why it matters, and how to effectively adopt it for your organization.
What is Code Security?
Code Security refers to a set of solutions and practices designed to protect software and applications from potential vulnerabilities, threats, and malicious attacks. It aims to ensure your code remains free of vulnerabilities and other issues that can create a security risk.
At its core, Code Security involves implementing various techniques and best practices to safeguard your software throughout its lifecycle. This spans the development, build, and deployment phases, and continues after applications go live. Code Security serves as a key aspect of application security before and after runtime.
The benefits of Code Security are numerous and far-reaching. By prioritizing code security, you not only protect your software—you safeguard your user data, preserve your reputation, and avoid the consequences of serious security incidents.
What threats does Code Security protect against?
Code Security aims to neutralize vulnerabilities in applications before they make it into production and get deployed to a live environment. Below are a few of the prevalent threats Code Security protects against:
Injection attacks
Injection attacks occur when attackers sneak malicious code into your application, often through user input fields. Common types include SQL injection and cross-site scripting (XSS), both of which can lead to severe system compromises, data breaches, and more.
Notably, attackers used SQL injection attacks to facilitate Facebook’s 2021 data breach, in which they exploited a vulnerability to scrape personal data from over 530 million accounts. Inadequate input validation allowed malicious SQL queries to access the database. This incident emphasizes the critical need for secure coding practices, such as input sanitization and parameterized queries, to prevent such vulnerabilities.
Supply chain attacks
Supply chain attacks pose a serious threat by targeting the software supply chain, often exploiting third-party libraries that many applications rely on. An infamous example is the SolarWinds attack in 2021, where hackers inserted malicious code into the company’s software updates, affecting more than 18,000 customers, including major corporations and government agencies. This breach highlighted vulnerabilities in the code-signing process, allowing attackers to modify the source code without detection.
This incident serves as a crucial reminder of the dangers associated with third-party code and the importance of strong security measures throughout the development lifecycle.
Vulnerability exploitation
Poor coding practices can expose severe vulnerabilities. The Log4j vulnerability, also known as Log4Shell, was a significant flaw in the Apache Log4j logging library that allowed attackers to execute arbitrary code on vulnerable servers. According to some estimates, the zero-day vulnerability was the primary reason that vulnerability exploitation increased 34% year-over-year in 2021. This vulnerability has been exploited in numerous attacks worldwide and remains a prevalent risk for some organizations.
The incident underscores the need for rigorous code reviews and adherence to secure coding standards to identify and fix such flaws before they are exploited.
What are the types of Code Security?
Code security involves several important practices that ensure the security and integrity of application code. This includes the following:
Infrastructure as Code (IaC) Security
Infrastructure as Code (IaC) allows developers to quickly and repeatedly provision cloud infrastructure through code, greatly enhancing the speed, consistency, and reliability of their work. Yet a simple mistake in an IaC artifact can quickly propagate into hundreds or thousands of misconfigurations when reused for future projects. IaC Security scans relevant artifacts and enforces policies that catch issues early in the SLDC.
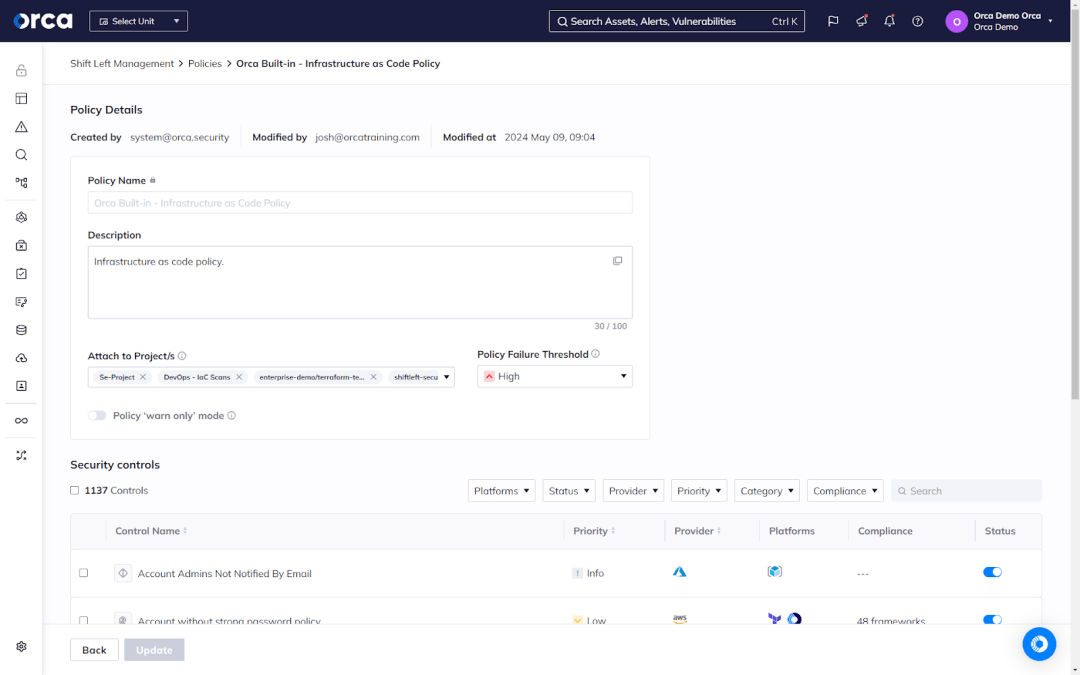
Source code vulnerability scanning
Open-source and third-party software components offer organizations a head start on their development projects. Yet these components commonly contain security risks and licensing requirements. Source code vulnerability scanning involves analyzing code for these vulnerabilities and addressing them before they reach production.
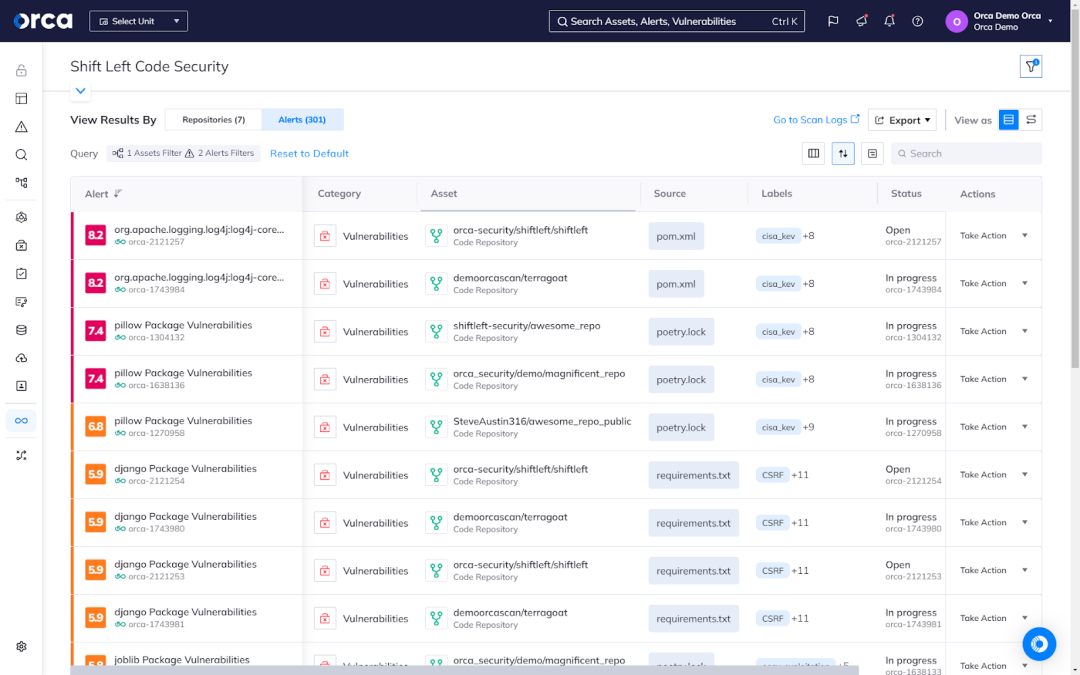
Secrets detection
Orca’s 2023 Honeypotting in the Cloud Report found that it takes only 2 minutes for attackers to discover an exposed secret in a GitHub repository before exploiting it. This highlights the importance of secrets detection, which scans code repositories for exposed secrets across the entire software development lifecycle (SDLC).
To illustrate, the Orca Cloud Security Platform offers secrets detection that utilizes comprehensive scanning, which happens whenever developers push new changes or create pull requests. The Orca GitLab App and GitHub App scan all code modifications, including side branches, and generate real-time alerts for any exposed secrets. Orca also examines your entire Git history for potential secrets. After each scan, Orca assesses the risk level of any detected secrets by analyzing multiple factors dynamically, including visibility of your repository, if a secret exists in your history or a test file, when the secret was first disclosed, and more.

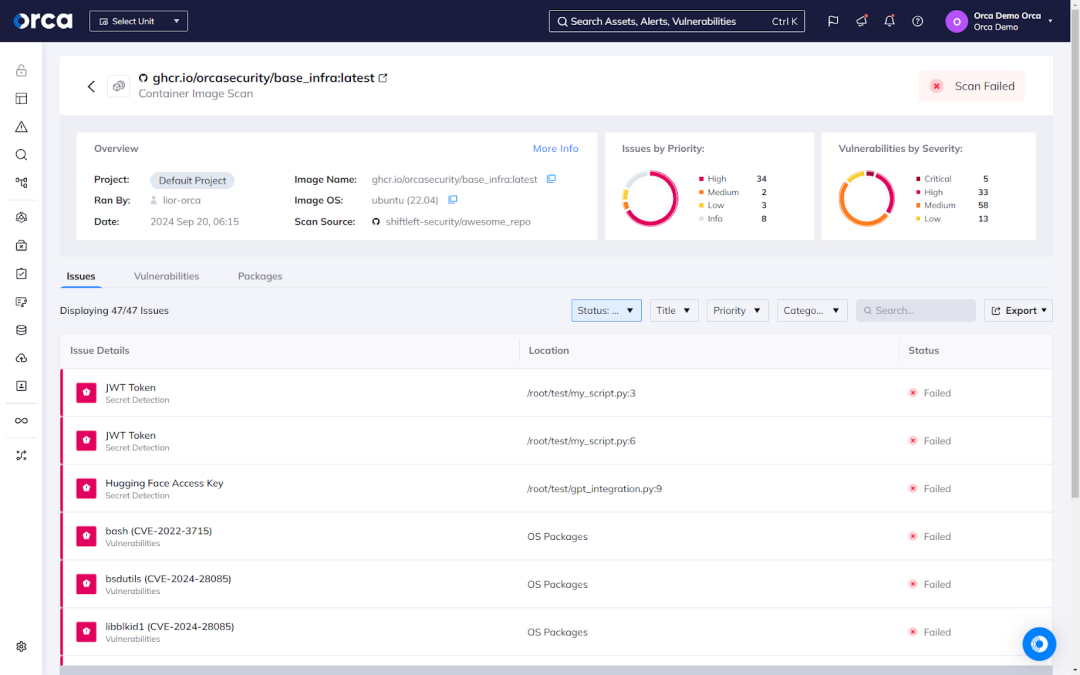
Container image scanning
Container images provide the blueprint for containers running in a live environment. When vulnerabilities or misconfigurations exist in those images, they become security risks if not detected and addressed before reaching production. Container image scanning analyzes these images against security policies, detects those with vulnerabilities and misconfigurations, and prevents them from reaching the build and deploy phases of the SDLC.
Cloud-to-Dev Security: Cloud-to-Dev capabilities trace risks in a runtime (live) environment to their code origins, such as an IaC artifact. These capabilities reveal the location, time, and owners and contributors of issues in code, enabling security teams to work with developers to neutralize the source of runtime risks and prevent future vulnerabilities.
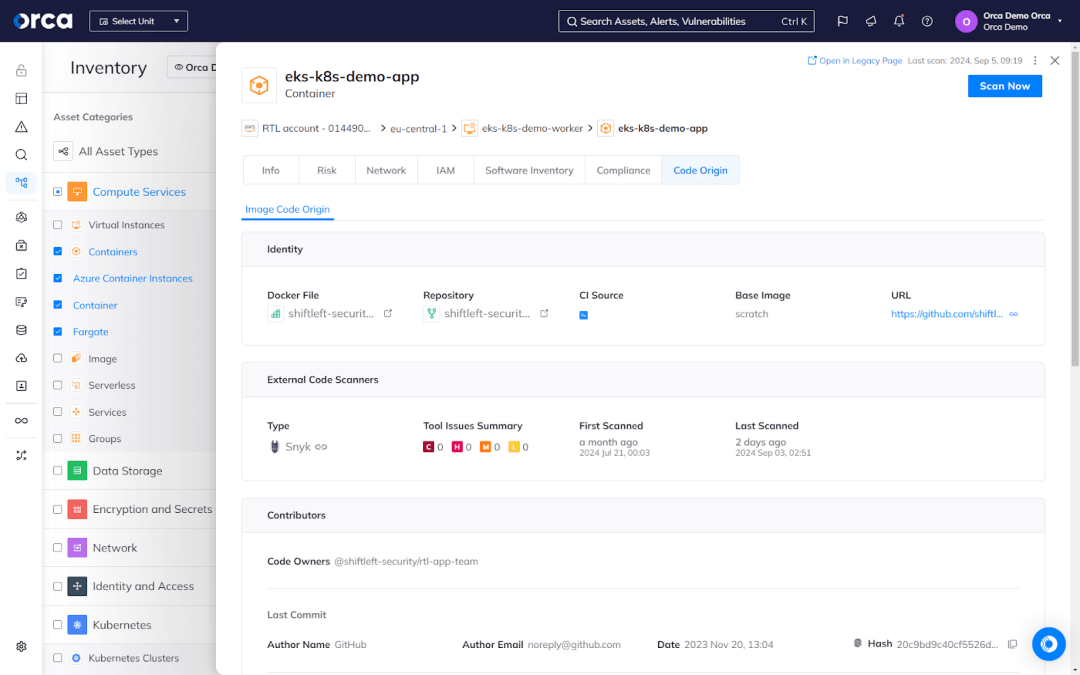
Benefits of Code Security
Implementing Code Security offers numerous advantages that can significantly enhance your software development process and protect your organization. Let’s explore the key benefits of Code Security and why you need it.
Protect your digital assets
When you prioritize Code Security, you safeguard your most valuable digital assets. By identifying and addressing vulnerabilities early in the development cycle, you can prevent potential breaches that could compromise sensitive data or intellectual property. This proactive approach to security helps maintain your company’s reputation and customer trust.
Streamline development and reduce costs
Contrary to popular belief, Code Security doesn’t slow down development. Instead, it accelerates it by catching issues at the easiest, most efficient, and least costly stage. Addressing issues in development boosts productivity and saves time in terms of cross-functional coordination, investigation, remediation, and more.
Improve runtime security
Code Security improves security by catching vulnerabilities early in the SDLC. Yet it also gives back time and capacity to busy security teams. This allows them to focus more attention on the most critical risks to your business and reduce their Mean Time to Resolution (MTTR).
Meet compliance requirements
Compliance is an organization’s authority to operate, which explains why it remains a top objective among most executives. Code Security helps organizations meet compliance standards by mitigating the misconfigurations and vulnerabilities that organizations must eventually address or could lead to a violation.
How can you implement Code Security?
Implementing Code Security requires several important activities and tools. Below, we detail the key steps and components involved:
1. Integrate security into your development process
To effectively implement Code Security, you need to make it an integral part of your development lifecycle. This means incorporating security checks and best practices from the very beginning of your project. By doing so, you’ll catch potential issues early on, saving time and resources in the long run.
2. Educate your team
One of the most important steps in implementing code security is ensuring that your entire development team understands its importance. Provide regular training sessions on security best practices, common vulnerabilities, and how to identify and mitigate potential threats to Code Security.
3. Utilize automated tools
Leverage automated security tools to scan your code for vulnerabilities, perform static and dynamic analysis, and identify potential security risks. These tools can help you catch issues in areas such as open-source dependencies, and can significantly speed up the security testing process.
4. Implement secure coding practices
Encourage your developers to follow secure coding guidelines and best practices. These may include input validation, proper error handling, secure authentication and authorization, and encryption of sensitive data both in transit and at rest.
By consistently applying these practices, you greatly reduce the risk of introducing vulnerabilities into your codebase.
Code Security best practices
Embrace the Shift Left approach
Shifting security left is one the most effective Code Security best practices. This means integrating security measures early in the SDLC as opposed to after an application is built and ready to deploy. By addressing potential vulnerabilities from the start, you save time and resources in the long run.
Leverage a Unified Shift Left Security Solution
A Shift Left Security solution accomplishes what its name implies: it helps organizations shift security left. Generally, the solution offers the ability to program and tailor security policies for IaC artifacts, container images, source code vulnerabilities, and other risks to code security.
The solution also scans for each of these risks, automatically detects when policy violations occur, and triggers an enforcement action, such as blocking a risky build in progress or notifying the developer and allowing the build to proceed. A Shift Left Security solution implements guardrails for developers, automating security in the development process while also boosting developer productivity.
Some advanced Shift Left Security solutions even offer Cloud-to-Dev capabilities, enabling security teams to trace runtime risks to their code origins. This allows security personnel to work with developers to address a flawed IaC artifact that may be producing thousands of vulnerabilities in the runtime environment.
Implement secure coding standards
Establish and enforce secure coding standards across your development team. These guidelines should address common threats to Code Security, such as input validation, proper error handling, and secure data storage. By following these standards, you significantly reduce the risk of introducing vulnerabilities into your codebase.
Tools and technologies for Code Security
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) tools analyze your source code without executing it, identifying vulnerabilities early in the development process. These tools are invaluable for catching common coding errors and security flaws before they make it into production.
Dynamic Application Security Testing (DAST)
Unlike SAST, Dynamic Application Security Testing (DAST) tools test your application while it’s running, simulating real-world attacks. This approach helps uncover runtime vulnerabilities that static analysis might miss, making it a crucial component of Code Security.
Software Composition Analysis (SCA)
As open-source components become increasingly prevalent in software development, Software Composition Analysis (SCA) tools have become essential. These tools scan your codebase for open-source vulnerabilities, helping you manage the risks associated with third-party libraries and dependencies. SCA focuses on identifying security risks and licensing requirements in open-source and third-party components, enabling organizations to address potential issues proactively.
By integrating SCA into your development process, you can enhance code security and ensure compliance with licensing standards. This practice is particularly important during the pre-deployment phase of the SDLC, where safeguarding your code is crucial. Ultimately, SCA allows you to leverage the benefits of open-source software while minimizing risks, ensuring that every component in your project contributes positively to your overall security posture.
Interactive Application Security Testing (IAST)
Interactive Application Security Testing (IAST) combines the strengths of both SAST and DAST, providing real-time security feedback during the testing phase. This technology offers a more comprehensive view of your application’s security posture.
What are the challenges of implementing Code Security?
Implementing Code Security presents several important challenges. Organizations often encounter several obstacles when trying to adopt Code Security and integrate it into their development processes. Below are some of the most common challenges that organizations face:
- Resistance from development teams: In many organizations, friction and tensions exist between security and development teams. The latter often sees the former as an impediment to their most important responsibility: shipping out code fast to meet tight deadlines. That helps explain why developers may resist the prospect of incorporating more security checks in the SDLC. Overcoming this resistance requires clear and intentional communication and education, especially about the benefits of shifting security left and how it aids developers’ responsibilities, workflows, and workloads.
- Limited resources and budget: Implementing Code Security often requires additional security tools, licensing fees, and training. This may discourage organizations with budgeting constraints. Fortunately, some advanced security platforms offer Code Security as part of a unified offering, as well as intuitive interfaces and features that minimize the need for training. Regardless of the budgeting constraints, Code Security can generate a significant return on investment when implemented properly.
- Integration complexities: Integrating Code Security tools into existing development workflows requires changes to existing workflows and processes. This calls for clear communication and training, and it may temporarily decrease productivity.
- Balancing security and speed: Investor expectations, rising competition, and financial performance all incentivize organizations to accelerate their speed of development. While important, this emphasis on shipping new products and features quickly should not come at the expense of security. Organizations must find the right balance between development and security and stay disciplined about sustaining it.
How does Orca help you deploy Code Security?
The Orca Cloud Security Platform is a true Cloud-Native Application Protection Platform (CNAPP) that helps organizations to effectively secure their applications across their entire lifecycle. Featuring a Shift Left Security solution, Orca Platform provides fully integrated Code Security and Source Code Management Posture Management (SCM-PM) to prevent vulnerabilities and other security risks from reaching production environments.
For Code Security, Orca offers IaC Security, secrets detection, Software Composition Analysis (SCA), and container image scanning. Orca enables you to set customizable security policies for each of these areas, and choose whether to block a risky build or allow it to proceed with a developer notification.
The Orca Platform also provides Cloud-to-Dev capabilities that trace runtime risks to their code origins. Orca links production misconfigurations or vulnerabilities to the source code repository where the risk originated, even down to the exact line of problematic code. This greatly reduces the Mean Time to Resolution (MTTR) for security teams, saving them from time-consuming investigations to track down the source artifacts and owners.
Orca also offers a bi-directional integration with Snyk to further enhance application security across the application lifecycle. The integration enhances collaboration between cloud security and application security teams, giving them visibility into different phases of the application lifecycle and access to shared intelligence for better coordination with development and DevOps teams.
Discover the Orca Cloud Security Platform
The Orca Cloud Security Platform is an agentless-first CNAPP that addresses security and compliance challenges across major cloud providers like AWS, Azure, Google Cloud, Oracle Cloud, and others. It offers a comprehensive suite of features, including API Security, Cloud Security Posture Management (CSPM), Cloud Workload Protection (CWPP), and more, all powered by its unique SideScanning™ Technology for thorough risk detection across your cloud environment.
Orca integrates insights into a Unified Data Model, which allows it to contextualize and prioritize risks effectively. This enables the platform to identify critical attack paths arising from interconnected security risks, ensuring that your security measures are both proactive and informed.
Getting started is simple—just a quick 30-minute onboarding session is required. Schedule a demo with one of our experts today to see how Orca can elevate your cloud security and help you better manage your risks.
FAQs
Why do you need Code security?
Code Security is essential to protecting applications throughout their lifecycle. It helps prevent, mitigate, and remediate vulnerabilities, misconfigurations, and other security risks. Code Security helps organizations avoid security incidents or data breaches, which can lead to financial, reputational, regulatory, or legal consequences.
What is the difference between Code Security and Shift Left Security?
While closely related, Code Security and Shift Left Security are distinct concepts. Code Security refers to practices designed to protect code from vulnerabilities. Shift Left Security encompasses Code Security measures and incorporates them early into the SDLC, while also providing Source Code Management Posture Management (SCM-PM) capabilities. SCM-PM aims to ensure SCM platforms are properly configured, as misconfigurations can present security risks to applications.
Does Code Security slow down development?
No. A common misconception is that Code Security hinders development speed. In reality, when implemented correctly, it can result in productivity and efficiency gains. By catching and fixing vulnerabilities early, developers avoid addressing issues during their most difficult and time-consuming stage. Additionally, advanced Code Security solutions integrate seamlessly with developers’ existing tools and workflows, minimizing disruption. The benefits of Code Security far outweigh any initial slowdown.
Table of contents
- What is Code Security?
- What threats does Code Security protect against?
- What are the types of Code Security?
- Benefits of Code Security
- How can you implement Code Security?
- Code Security best practices
- Tools and technologies for Code Security
- What are the challenges of implementing Code Security?
- How does Orca help you deploy Code Security?
- FAQs






