Infrastructure-as-Code (Iac) has revolutionized the development of cloud applications, enabling developers to automate and scale the laborious effort of manually configuring servers and infrastructure components. With IaC, developers can quickly and repeatedly provision cloud infrastructure through code, greatly enhancing the speed, consistency, and reliability of their work.
Yet without the proper security measures, IaC can open Pandora’s box. A simple mistake in an IaC artifact can quickly propagate into hundreds or thousands of misconfigurations when reused for future projects. That illustrates the importance of IaC security, the area of cloud security focused on detecting IaC issues early in the software development lifecycle (SDLC).
In this post, we examine the key capabilities of Orca’s IaC Security and how it bolsters your software supply chain security.
Advanced IaC scanning to prevent issues before they happen
Security teams tend to lack visibility into and control over development environments and IaC artifacts. This creates a significant blindspot in cloud security, especially considering the self-service nature of IaC, where developers can easily create new templates or provision infrastructure on demand. As a result, artifacts that contain errors, misconfigurations, or risky dependencies often go unchecked and make it into production, where they quickly mature into security risks. Meanwhile, security teams must react and respond to these issues, rather than preventing them from occurring.
The Orca Cloud Security Platform empowers security teams with the insight and capabilities to fully secure IaC across development environments, and this starts with advanced IaC scanning. Orca provides comprehensive and advanced scanning for IaC artifacts as soon as developers check them into repositories. Orca validates code for a wide range of IaC frameworks, including Ansible, Terraform, AWS Cloud Formation, Azure Resource Manager, Google Deployment Manager, Pulumi, and Kubernetes, to name a few.
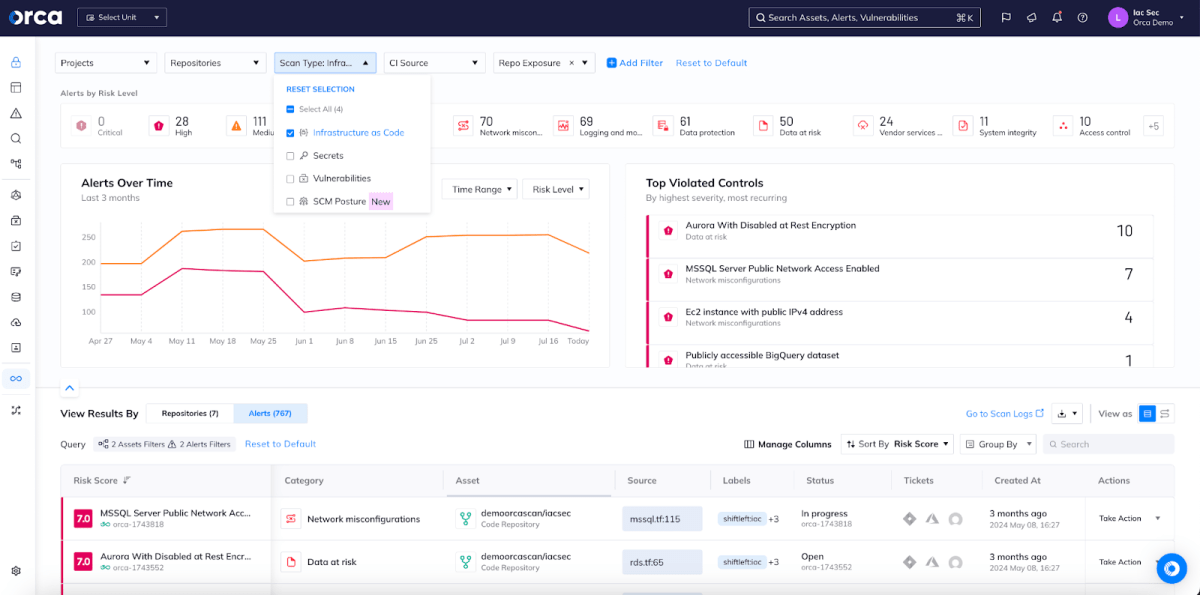
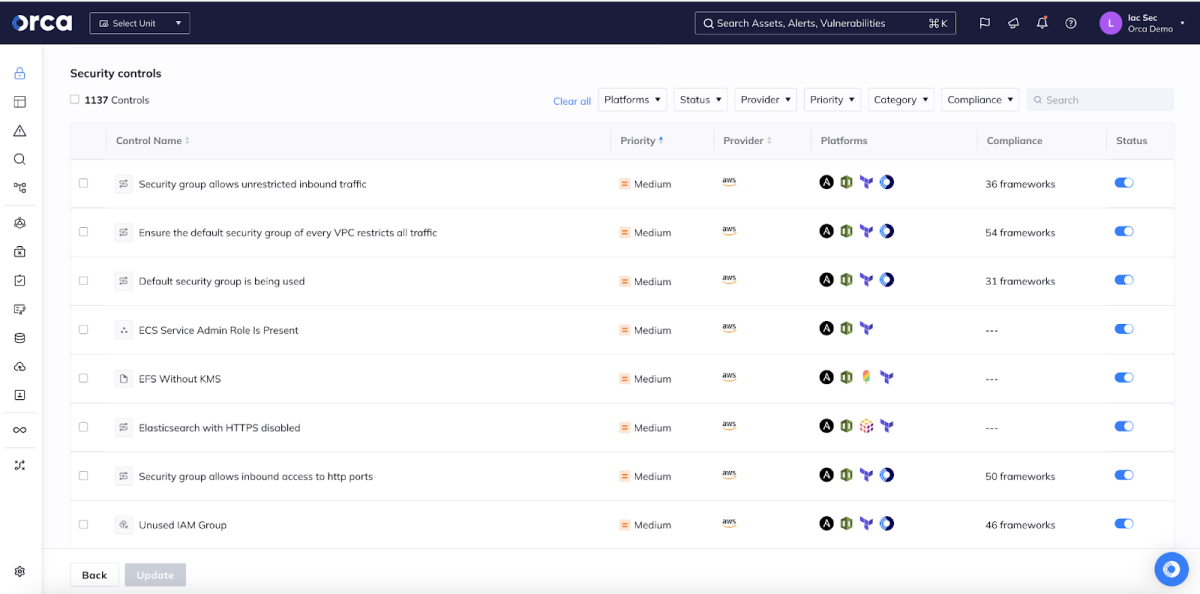
Orca also allows you to tailor IaC scanning to your organization’s unique needs, focusing on any issues of concern. You can define policies for specific risks in your IaC artifacts by assigning relevant security controls, which include more than 1,100 covering a wide variety of use cases. Orca makes it easy to quickly search and filter controls by keyword, IaC platform, risk level, or compliance framework.
Along with setting your controls for the policy, you can also define the enforcement rules if an IaC scan uncovers security issues. These include the conditions and action for the policy. Conditions may include a specific threshold for unacceptable risk or an event such as a push request to a source code repository. Actions may include blocking a risky build or notifying developers of a risk but allowing them to proceed with their work.
For example, you can choose to block a build whenever Orca detects an S3 bucket set to allow a delete action for all principals, which could leak private information to the Internet or allow unauthorized data tampering or deletion.
Orca allows you to apply your defined policies to any source code repository or to your CI/CD pipelines at build time. This augments Orca’s detection of all issues deployed by the code. For this purpose, you can use Orca’s GitHub App, GitLab App, or Orca CLI, our lightweight command-line interface. Once integrated, IaC scanning runs on every push request for the defined policies, analyzing any new additions or changes to the repository for issues or violations.
Seamless and enhanced developer experience
While your security teams gain visibility into IaC code and can address identified issues from the Orca platform, your developers get a seamless workflow for addressing issues within their existing tools and workflows. Any time they make changes to an IaC file that results in a security issue, they will get notified of the risk, where it exists, and how to address it.
As long as your repositories support SARIF (Static Analysis Results Interchange Format), your developers immediately see the results of a failed scan on the Security tab of the relevant repository. This brings security and development into one cohesive and unified workflow, allowing developers to fix all issues in one pass.
Additionally, Orca offers two-way integrations with popular ticketing systems including Jira and ServiceNow. This enables security teams to create a Jira ticket from the Orca Platform, assign it to the appropriate developer, monitor its status, and verify its resolution—without ever logging into Jira. Meanwhile, developers never need to login to Orca, eliminating the need for them to switch to another application and minimizing friction between teams.
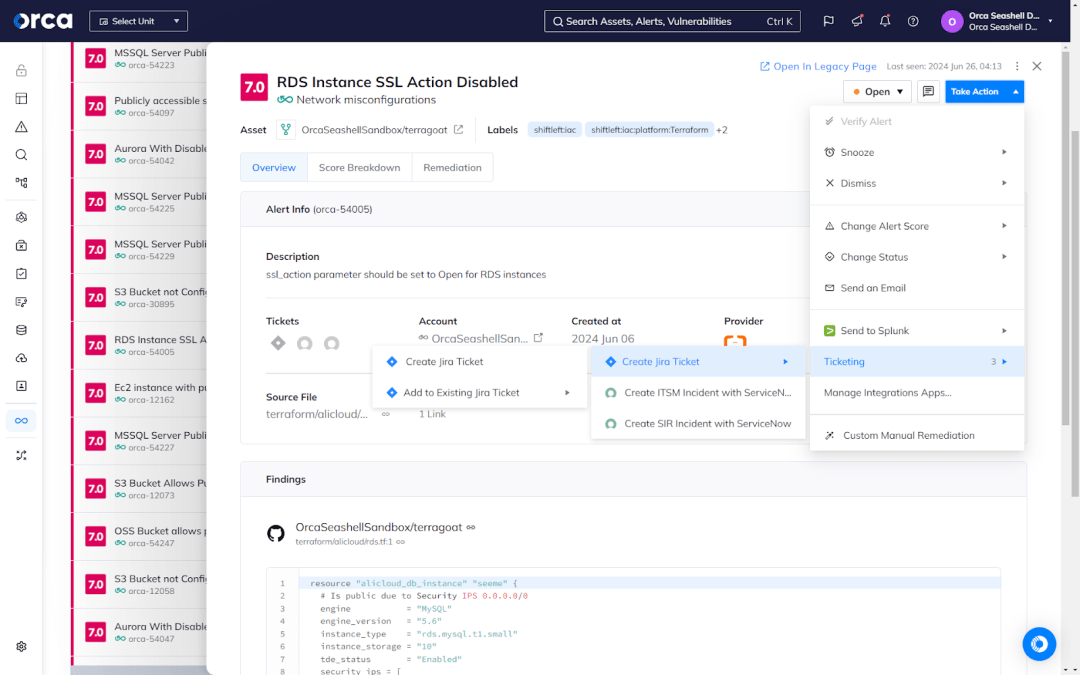
Cloud-to-dev remediation
In its 2023 Market Guide for Cloud-Native Application Protection Platforms (CNAPP), Gartner® emphasized the importance of technology that can associate a production risk with the developer and issue that produced it. The Orca Cloud Security Platform became the first CNAPP to offer this capability, which enables security teams to easily trace risks from cloud infrastructure back to the underlying IaC code in Git repositories.
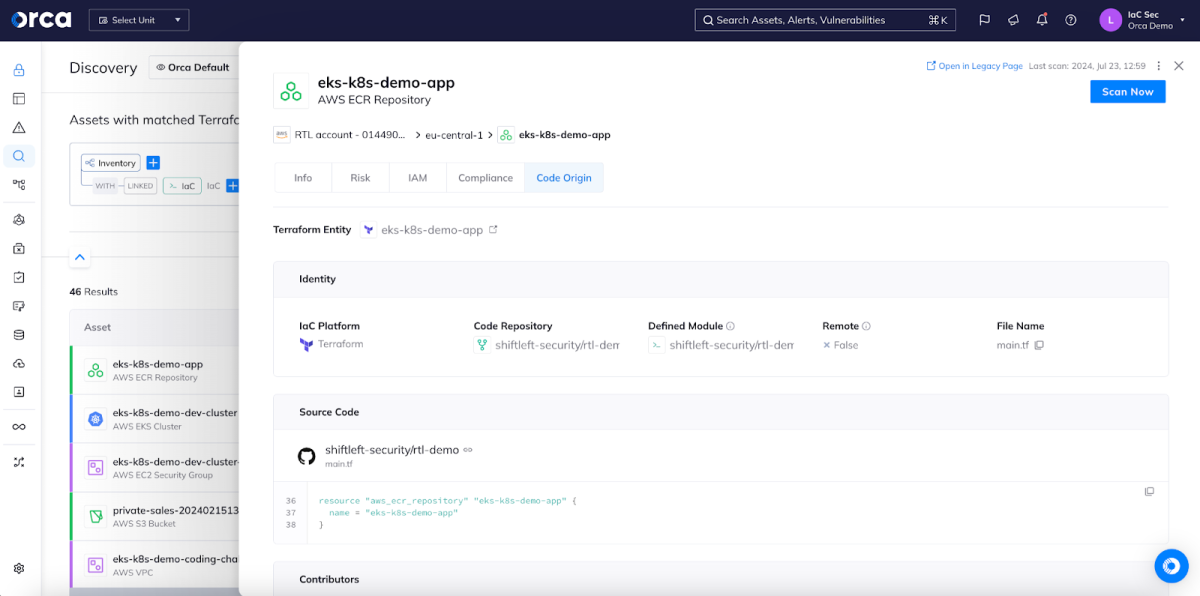
Orca’s Cloud to Dev capabilities pinpoint the origin of every IaC issue, showing you the individual, location, and time of the error. This enables your security team to address the source of the problem, saving considerable time, effort, and capacity in the future.
IaC Security: A necessary aspect of Shift Left Security
IaC is an essential innovation to modern cloud development, enabling developers to quickly and consistently provision cloud infrastructure through code. Despite its enormous benefits, IaC can also create and scale significant security risks if left unchecked.
This underscores the importance and need for IaC Security as part of Shift Left Security. It enables your teams to prevent security risks from reaching and multiplying in your live environment, when they are most time-consuming and costly to address.
About the Orca Cloud Security Platform
The Orca Cloud Security Platform identifies, prioritizes, and remediates security risks and compliance issues across the multi-cloud environments of AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. Leveraging its SideScanning™ technology, Orca offers an agentless-first approach that provides full coverage and comprehensive risk detection of your cloud estate.
Orca detects vulnerabilities, misconfigurations, malware, lateral movement, API risks, sensitive data risks, AI risks, overly permissive identities, and more. Unlike other solutions that loosely integrate multiple point solutions or require agents, Orca delivers comprehensive cloud security in a unified platform.
Learn more
Ready to see Orca’s IaC Security in action or discover more about our capabilities? Book your personalized 1:1 demo today. We’ll show you how Orca helps you catch vulnerabilities and misconfigurations early in the SDLC and prevent them from reaching production.