Table of contents
- Key Takeaways
- Introduction
- What is CSPM?
- Understanding Cloud Security Posture Management and how it protects your cloud
- How does Cloud Security Posture Management work?
- Cloud Security Posture Management vs other solutions
- Limitations of Cloud Security Posture Management: The case for CNAPPs
- Choosing the right CNAPP for your Cloud Security Posture Management needs
- Conclusion
- CSPM FAQs
Key Takeaways
- Challenge: The pace of change in the cloud disrupted the traditional ways of securing infrastructure with agents.
- Cloud security posture management (CSPM) starts with a comprehensive asset inventory across your cloud native application’s cloud architecture, whether it is 100% on a single cloud service provider or across multiple providers.
- CSPM solutions continuously monitor for misconfigurations of cloud infrastructure, mismanaged secrets, vulnerabilities, overprivileged identities, and compliance gaps.
- Orca’s CSPM solution reduces time for investigation, prioritization, and validation by providing relevant context across domains (i.e. assets, policies, exposure), numerical risk scores per alert and asset factoring in context, and visualizations for attack paths.
- CSPMs provide the solid foundation for proactive cloud security hygiene and catching compliance drift when it happens.
Introduction
The cloud revolution has transformed the IT landscape, offering businesses the flexibility, scalability, and efficiency they need to thrive in today’s dynamic marketplace. Yet, as organizations migrate their data and operations to the cloud, security concerns follow closely behind. Enter Cloud Security Posture Management (CSPM), an approach designed to help businesses manage and fortify their security in the cloud era.
In this guide, we’ll explore what CSPM is, why it came to life, how it differentiates from other cloud security tools, and why it’s essential for any organization with a cloud footprint – even though it still has limitations and would need to be augmented with other solutions or a more comprehensive centralized cloud security platform.
What is CSPM?
Cloud Security Posture Management (CSPM) is a collection of security solutions that enable users to identify, control, and remediate risks and any misconfigurations in their cloud infrastructure. CSPMs can detect and remediate a variety of misconfiguration use cases, including internet-exposed virtual machines and storage buckets, use of your cloud provider’s default settings, open ports not being used by other applications in your infrastructure, and much more. CSPMs remain one of the most important and popular cloud security solutions. Gartner forecasts the market for CSPM will continue to grow, with annual revenues predicted to reach $3.32 billion globally by 2027, a more than 213% increase from 2022. Still, standalone CSPMs are increasingly being replaced by newer, more integrated offerings, such as CNAPP.
Evolution and significance in the cybersecurity landscape
In 2014, Gartner coined the name, “Cloud Security Posture Management” to describe an emerging cloud security category. As the cloud computing services of AWS, Microsoft Azure, and Google Cloud gained popularity, CSPMs emerged as a much-needed solution. Before CSPMs, organizations depended on Cloud Workload Protection Platforms (CWPP), which were sufficient to protect the early adoption of virtual machines and later also containers.
Unlike CWPPs, CSPMs enabled organizations to maintain the proper configurations of their cloud services—a new requirement to satisfy their end of the shared responsibility model with cloud service providers (CSPs). This model, which remains as necessary today, puts the onus on organizations to protect their cloud assets and services, while calling on CSPs to ensure the security of their cloud infrastructure.
CSPMs helped fulfill this obligation but didn’t erase the need for CWPPs—and subsequently, other solutions. CSPMs don’t secure or provide visibility into cloud workloads, which means that they are not able to detect vulnerabilities, malware and exposed secrets.
The risks of cloud misconfigurations
To understand the importance of CSPMs, look no further than the prevalence and impact of cloud misconfigurations. They remain a prevalent issue and risk for businesses of all sizes. Gartner predicts that six in 10 organizations will see cloud misconfiguration as a top cloud security priority by 2026. While cloud misconfigurations can arise for a number of reasons, several factors increase their likelihood. Below are some of the most common factors, though this is far from an exhaustive list:
- Lack of cloud visibility: Many organizations have limited visibility into their cloud estate. This stems from using multiple siloed tools that don’t provide holistic insights and leveraging cloud security solutions that rely on agents, only covering around 50-70% of assets due to partial deployment.
- Unaltered default values: Organizations often fail to review and regularly update default configuration values, increasing their exposure to known vulnerabilities. Examples of default values range from usernames and common ports to pre-defined (and publicly known) login credentials.
- Insufficient monitoring: Many organizations fail to integrate logging and other monitoring tools into their cloud configuration, leading to insufficient monitoring and missing critical issues before they become security incidents.
- Overprivileged identities: Users often have far too much access to a given system, greatly increasing the possibility of a breach. If an attacker manages to get hold of user credentials that are overly permissive, this can expose critical network or web services.
- Mismanaged secrets: If secrets are stored as plaintext, this significantly increases the chances of compromise, not to mention the impact and scope of a potential breach. Examples of secrets include passwords, API keys, access tokens, and more.
- Neglected cloud assets: Many cloud assets, for one reason or another, get ignored or forgotten, and aren’t updated. This leads to these assets becoming riddled with vulnerabilities, just waiting for an attacker to exploit. While a significant risk, neglected assets are also a very common reality of cloud estates. According to findings from the 2024 State of Cloud Security Report, 84% of organizations have at least one public-facing neglected asset, while 81% have public-facing neglected assets with commonly exploited open ports. This provides an open door for hackers to exploit for initial access, lateral movement, and more.
Understanding Cloud Security Posture Management and how it protects your cloud
CSPMs ‘police’ misconfigurations and ensure compliance in cloud environments. In short, they focus on the foundational and fundamental issues that can cause cloud security concerns. They monitor cloud infrastructure by regularly scanning for any violations of security policies or industry best practices. They also provide centralized visibility into the entire control plane and the ability to conduct risk assessments.
CSPMs, by promptly notifying staff about misconfigurations that could lead to operational inefficiencies or security vulnerabilities, help reduce costs, identify potential security risks, and educate teams.
The role of Cloud Security Posture Management in modern cloud security
As a vital cloud security solution, CSPMs fulfill several important functions:
- Security policy enforcement: CSPMs enforce security policies, monitor misconfigurations, and identify compliance risks.
- Multi-cloud configuration management: CSPMs centralize the visibility of the entire cloud control plane across multiple cloud service providers.
- Cloud control plane audits: Connecting via API, CSPMs allow instant access and auditing of configurations across the entire control plane of multi-cloud environments.
- Compliance reporting for cloud infrastructures: CSPMs continually perform compliance checks to help organizations maintain compliance of their cloud infrastructure.
- Threat intelligence integration: Most CSPMs ingest data from the threat tools of native cloud service providers, helping to further identify and prioritize misconfiguration risks.
How does Cloud Security Posture Management work?
Once deployed and connected to your cloud environment(s), CSPM solutions perform several necessary cloud security functions.
Cloud asset inventory
CSPM platforms provide a cloud infrastructure inventory which gives organizations visibility into all the assets that are running in the cloud. This enables the CSPM to report on risks found in your infrastructure, while also allowing your teams to then remediate and take action based on this information.
Continuous cloud compliance monitoring
CSPM solutions continuously monitor your cloud resources for compliance, which is often complex and challenging for security teams. Numerous compliance frameworks and regulations exist and vary by region, state, and/or country. CSPMs continually keep these standards updated, giving your organization the ability to identify, mitigate, and remediate risks.
Common compliance frameworks include:
- Center for Internet Security (CIS) benchmarks
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act of 1996 (HIPAA)
- ISO 27001
- PCI-DSS
- System and Organizational Controls 2 (SOC 2)
Examples of compliance risks that CSPM technology identifies include unencrypted personal identifiable information (PII) and the absence of restricted access to PII data or storage buckets.
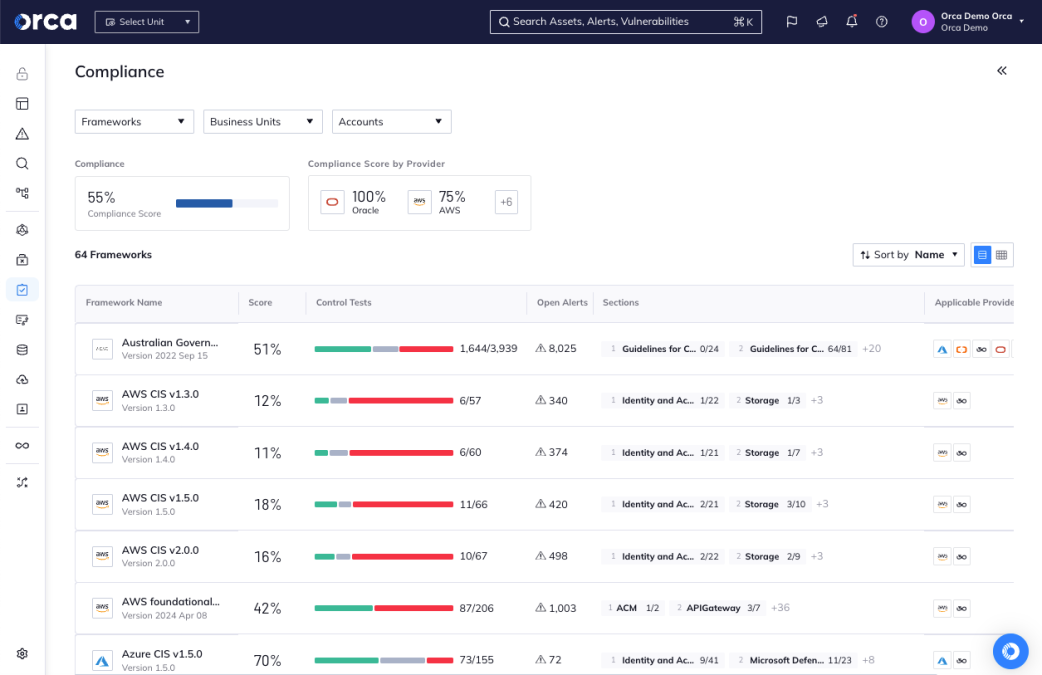
Cloud compliance standards
Additionally, CSPM platforms use predefined standards to better position your organization’s cloud security posture. They also ensure your organization can comply with mandatory standards in the event you possess any customer data that is considered PII, such as social security numbers, email addresses, protected health information (PHI), passport numbers, and more.
Policy-based definitions
CSPM solutions define and enforce policies for accessing the results, reports, and data associated with compliance standards.
Detection of cloud threats
When it comes to cloud risks, CSPM solutions identify any weaknesses that could compromise your cloud network and infrastructure. Some CSPM products prioritize alerts and categorize threats as hazardous, imminent compromise, or compromise.
Additionally, some solutions may also indicate the types of affected cloud assets according to categories, such as accounts, severless, users, and access. They display asset trends and new alerts over a period of time, which helps organizations diagnose the health of your infrastructure.
Incident response
Some CSPMs enable you to review how threats are detected, controlled, and remediated. They present a set of procedures to follow when threats are detected, and document the responsibilities for responding to and remediating such attacks.
Some CSPM platforms also integrate this information with ticketing systems (e.g., ServiceNow, Jira, etc.), alerting systems (e.g., Slack), and other notification applications that help your organization identify, respond to, mitigate, and remediate threats quickly and efficiently.
Auto-remediate cloud risks and compliance issues
After identifying risks, CSPMs offer automated and guided remediation options (some using generative AI).
They also offer automated remediation workflows that help your security teams secure their cloud infrastructure efficiently, and in some cases integrate remediation steps with ticketing and alerting systems.
Cloud Security Posture Management vs other solutions
While among the most popular cloud security solutions, Cloud Security Posture Management platforms are often used in tandem with other security tools since CSPM does not discover all risk areas, such as vulnerabilities and malware.
Below we compare CSPM to other popular cloud security products:
| CSPM | CNAPP | CWPP | CIEM | |
|---|---|---|---|---|
| Goals | Identify and remediate cloud misconfigurations and compliance issues | Via a unified platform, identify, prioritize, and remediate security risks and compliance issues across the entire cloud estate | Protect host systems and workloads | Manage access and permissions |
| Key capabilities | Misconfiguration detection, compliance reporting | Misconfiguration detection, compliance reporting,, vulnerability management, identity governance, entitlement management, API security, data security, container and Kubernetes security, AI security, Shift Left security, cloud detection and response (CDR) | Runtime protection, vulnerability management, malware detection | Identity governance, entitlement management |
| Threats covered | Misconfigurations, policy violations | Vulnerabilities, misconfigurations, malware, lateral movement, IAM risk, data risk, API risk, active breaches | Host and container vulnerabilities, malware | Excessive permissions, IAM risks |
| Best uses | Comprehensive cloud environment monitoring | Unified End-to-end cloud security | Protection of cloud workloads across environments | Access controls in multi-cloud environments |
CSPM vs. CWPP
CSPM tools cover cloud environments and any misconfigurations that could present risks to them. On the other hand, cloud workload protection platforms (CWPPs) focus on securing cloud-based workloads across virtual machines (VMs), containers, and serverless functions. They largely focus on what’s currently running on the cloud rather than their configuration
CSPMs cover the control plane (configurations), while CWPPs cover the data plane. Both CWPPs and CSPMs provide needed capabilities for effective cloud security.
CSPM vs. CIEM
While CSPM solutions provide essential visibility into misconfigurations, cloud infrastructure entitlement management (CIEM) solutions manage access rights and permissions for your cloud resources. CIEMs remain critical for building a strong security strategy based on the principle of least privilege (PoLP). CIEM solutions offer several major advantages, including scalable entitlements visibility, compliance assurance, and more.
CIEM and CSPM solutions are complementary and both are necessary for cloud security.
CSPMs vs. CNAPPs
CSPM platforms lack the functionality of CWPP and CIEM. On the other hand, cloud-native application protection platforms (CNAPPs) offer all these capabilities in one platform, along with API security, container and Kubernetes security, Shift Left security, and more.
Since Gartner first named the CNAPP category in 2020, the platform is now a popular alternative to using a standalone CSPM tool and other disparate cloud security solutions. CNAPPs tend to produce cost advantages, enhanced user experiences, improved efficacy, and more compared to other cloud security products. According to Gartner, 75% of new CSPM purchases will come from CNAPP offerings by 2025.
Limitations of Cloud Security Posture Management: The case for CNAPPs
While a necessary cloud security tool, Cloud Security Posture Management solutions have key limitations that prevent comprehensive cloud security, including:
- No insight into workloads: CSPM solutions don’t cover workloads. For example, they can’t detect vulnerable web servers or infected workloads, which requires a CNAPP or CWPP solution.
- Ineffective alert prioritization: CSPM platforms only prioritize alerts based on factors in the control plane, not the data plane. As a result, this limited view prevents alerts from accounting for all contextual factors that make risks more or less severe.
- No lateral movement risk detection: Attackers often use an initial breach as the starting point for moving laterally in a cloud environment toward their intended target. CSPM tools can’t identify which keys could allow hackers access to other assets, leaving critical attack vectors unidentified and exposed.
- Identity and permissions management: CSPMs tools don’t manage cloud access controls, permissions, and entitlements. As a result, organizations lack the functionality to address excessive permissions and apply the principle of least privilege (PoLP) to cloud resources.
A true CNAPP combines the capabilities of CSPM with CWPP, CIEM, Data Security Posture Management (DSPM), Kubernetes and container security, API security, and more. CNAPPs provide comprehensive risk coverage, centralized management, risk prioritization, and holistic insight into risk context.
Choosing the right CNAPP for your Cloud Security Posture Management needs
The emergence of CNAPPs offers cloud capabilities and coverage that extend far beyond traditional Cloud Security Posture Management tools. That explains why most organizations are now looking to CNAPPs for their cloud security needs. Yet it also calls for acknowledging that the capabilities and benefits of CNAPPs vary significantly depending on the vendor. To ensure you choose the best solution, look for the following characteristics or features needed for effective CSPM:
Comprehensive
Look for solutions that leverage a significant number of configuration controls across multiple categories, including authentication, logging and monitoring, data protection, network configurations, Kubernetes configurations, and system integrity.
For example, Orca’s Cloud Security Platform uses more than 2,500 configuration controls across more than 10 categories.
Also favor solutions that alert you to the full range of security policy violations, including misconfigured S3 buckets, KMS keys, Elasticsearch and RDS databases, Google storage buckets, and much more.
Unified
Look for solutions that offer a single pane of glass for all your CSPM and other cloud security needs. Solutions that call for using multiple interfaces or siloed tools result in inefficiencies, a poor user experience, and blind spots in your cloud coverage. This is often the case when, instead of building a purpose-built cloud platform, vendors simply stitch together acquired tools and offer them as one ‘unified’ platform.
Context-aware
Many CNAPPs alert you to issues but fail to prioritize the most critical risks demanding your immediate attention. The result is a barrage of warning signals that lead to alert fatigue and force your team to manually decipher between the most pressing action items and issues that can be remediated later. For this reason, look for solutions that prioritize alerts accurately.
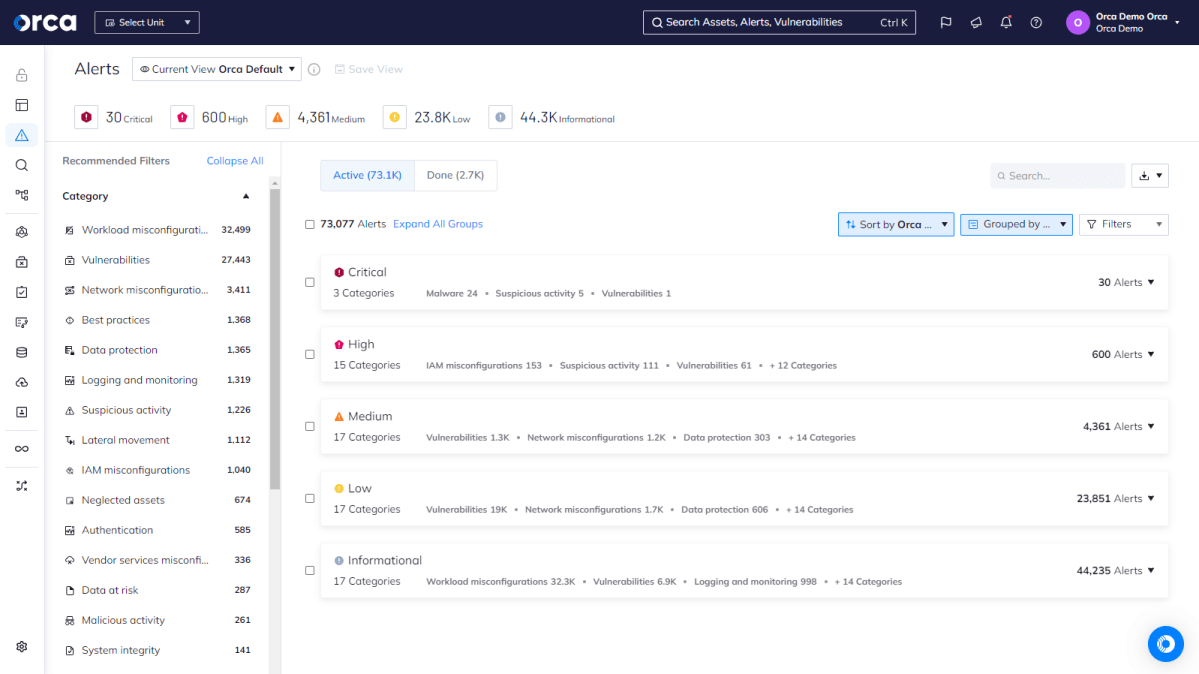
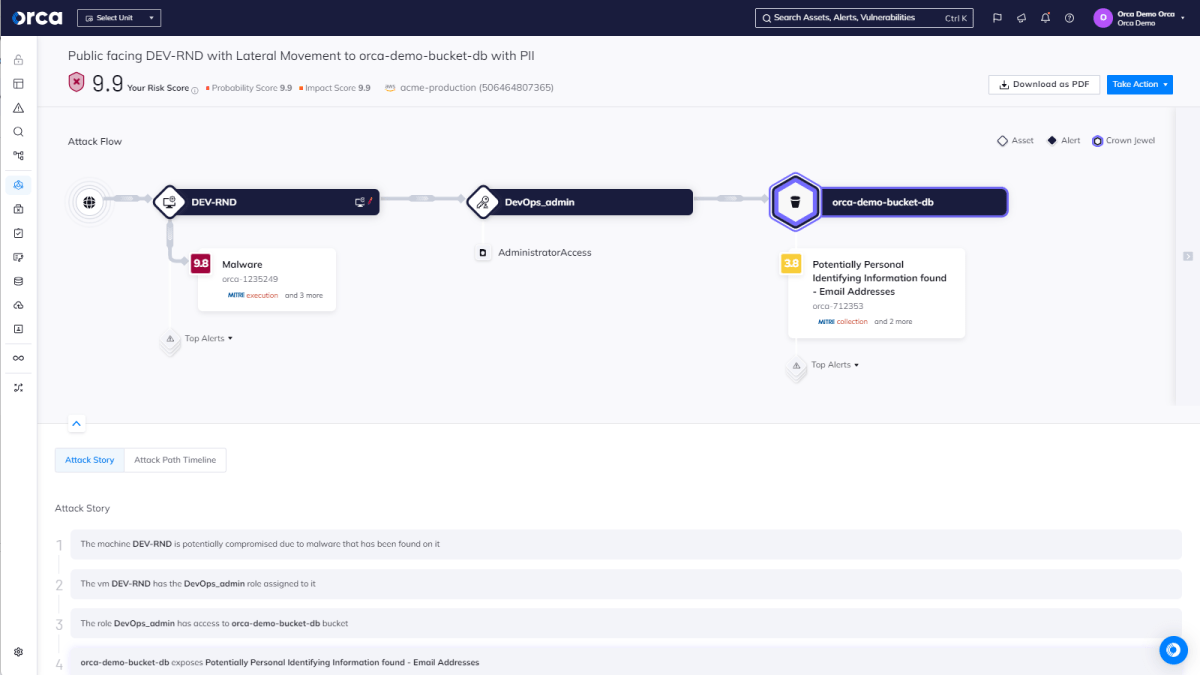
Attack Path Analysis
Along with contextualizing alerts, an optimal CNAPP diagnoses the interconnected risks between cloud assets and identifies potential attack paths that hackers could exploit to endanger your crown jewels. These solutions then prioritize these vulnerabilities so you can concentrate on the paths that matter most. Look for solutions that offer this capability.
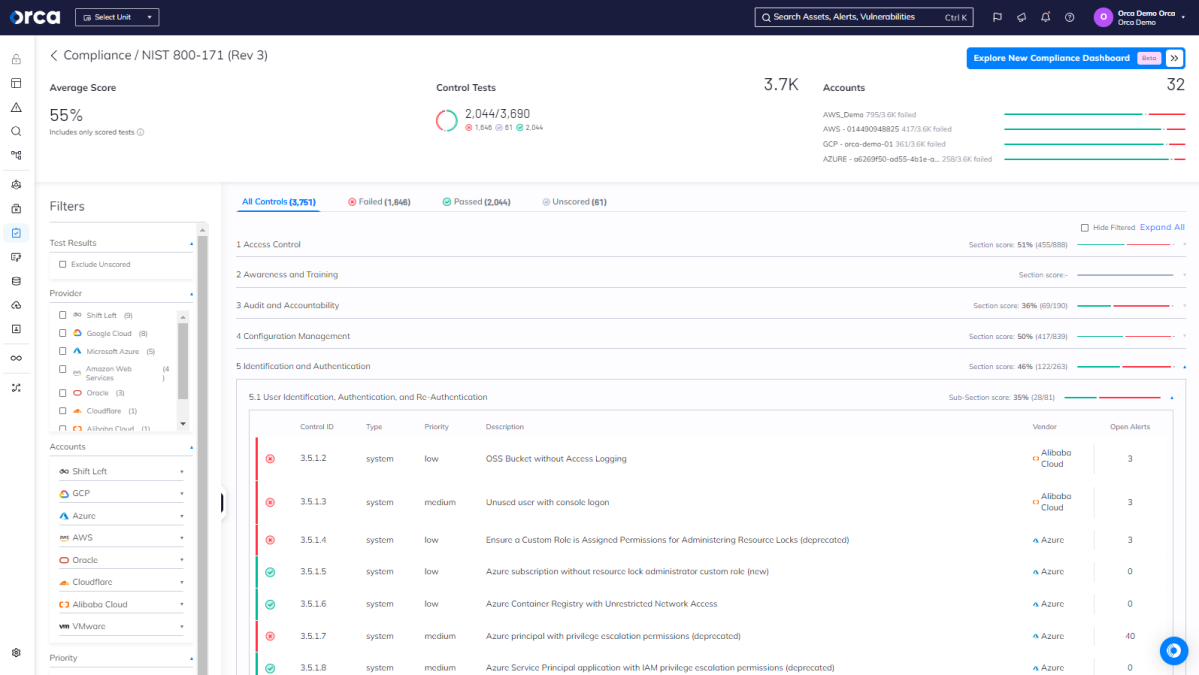
Compliance
An important function of CSPM is ensuring that your cloud assets adhere to compliance frameworks and industry standards. Look for CNAPPs that automatically check your cloud configurations, policies, and workloads against all major frameworks and present your compliance status in one unified view. Some of the more advanced CNAPPs allow you to combine and customize multiple frameworks from an extensive library that also includes industry benchmarks for external and internal reporting.
Enhanced Querying
Learning a query language or manually creating queries for every search scenario can slow down your teams. Look for CNAPP solutions that simplify search and make it more efficient for all use cases, Cloud Security Posture Management included. This entails offering AI-driven search, and out-of-the-box system queries and a query builder that tests and validates rules and displays available attributes and commands.
Because queries inevitably result in remediation needs, also look for solutions that integrate with common ticketing and developer tools, such as Jira, ServiceNow, PagerDuty, Slack, etc. This enables you to infuse security into existing workflows and tools.
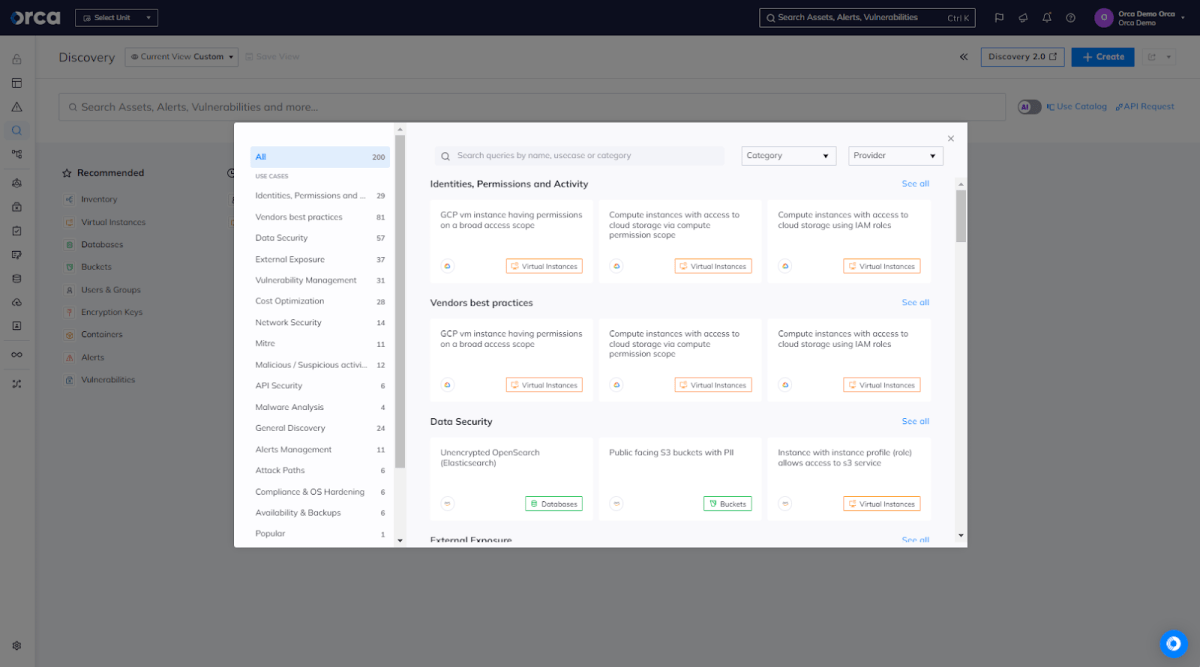
AI-driven search and remediation
AI presents significant opportunities to automate and accelerate critical tasks for security and cloud teams. That explains why some CNAPP solutions leverage it to enhance cloud-security search and remediation.
For search, this offers users the ability to ask questions in plain English or their language of choice, eliminating the need to learn a special query language or have familiarity with cloud terminology.
Additionally, favor solutions that offer AI-driven remediation to generate step-by-step instructions for resolving issues, accelerating response time. In both use cases, organizations should prioritize solutions that provide transparency around AI outputs for validation and also allow the option to choose between different AI services offered by their CSP.
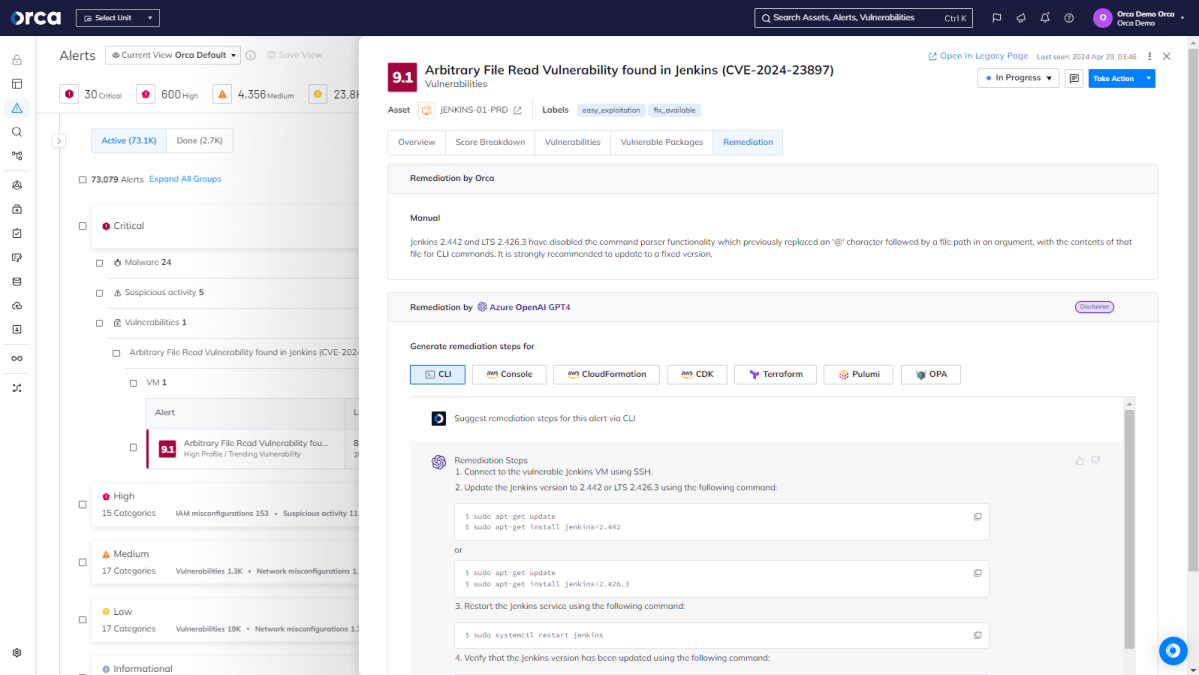
Conclusion
CSPMs are a critical component of any robust and comprehensive cloud security stack. They enable organizations to identify, control, and remediate risks and any misconfigurations in their cloud infrastructure. This remains necessary for organizations to thrive in the cloud.
While the past called for adopting standalone CSPM solutions, CNAPPs now extend their capabilities. CNAPPs consolidate multiple cloud security solutions into one platform, providing better integration, visibility, functionality, usability, and cost efficiency than siloed CSPM solutions. This explains why institutions like Gartner expect the CNAPP market to largely replace traditional CSPM offerings.
Learn more about the Orca Cloud Security Platform
The Orca Cloud Security Platform offers a true agentless-first CNAPP that identifies, prioritizes, and remediates security risks and compliance issues for AWS, Azure, Google Cloud, Kubernetes, Alibaba Cloud, and Oracle Cloud.
Orca’s solution consolidates cloud configuration, workload, identity & entitlement security, multi-cloud compliance, vulnerability management, and more in a single platform. Leveraging a Unified Data Model, Orca contextualizes risks and recognizes when seemingly unrelated issues can create dangerous attack paths. This enables Orca to prioritize risks effectively, reduce alert fatigue, and ensure your teams can focus on the most critical and important tasks.
After a quick setup (usually less than 30 mins), Orca provides deep and wide visibility into all cloud assets and helps organizations continually improve their cloud security posture. Schedule a demo with one of our experts to see how the Orca Cloud Security Platform can uplevel your cloud security.
CSPM FAQs
Are CSPM and CNAPP the same?
No. CSPMs secure cloud environments by addressing any misconfigurations in them. While CNAPPs also provide this functionality, they bring additional capabilities, including those offered by CWPPs, CIEMs, DSPM, API security, container and Kubernetes security, and other solutions. CSPMs require organizations to acquire additional cloud security solutions for complete coverage.
Alternatively, organizations choose CNAPP solutions as a unified and comprehensive cloud security solution. Gartner finds that 75% of new CSPM solutions by 2025 will be through CNAPP offerings.
Why do cloud misconfigurations happen?
Cloud misconfigurations happen for several reasons. Unrestricted access controls, unreviewed default values, mismanaged secrets, insufficient logging and monitoring are among the common causes of cloud misconfigurations.
What is a CSPM tool?
Gartner first coined the term “Cloud Security Posture Management (CSPM)” in 2014, signaling the emergence of a new breed of cloud security. CSPMs enable security teams to identify, control, and remediate misconfigurations in their cloud infrastructure. For example, CSPMs can detect and remediate open ports that are not in use, storage buckets and virtual machines exposed to the internet, unchanged default configuration values, and more.
While the sale of standalone CSPM tools continues to grow, Gartner forecasts that organizations will increasingly acquire CSPM capabilities through CNAPP, an all-in-one alternative solution to traditional, standalone CSPM platforms.
What roles generally use a CSPM tool?
Security practitioners and teams rely on CSPM tools to identify and remediate misconfigurations that put their cloud environments at risk. While other roles are impacted by the use of CSPMs, security personnel remain the primary users of the technology.
Who needs CSPM?
Any organization that relies on cloud computing needs a dedicated CSPM solution, which they can acquire by procuring a standalone CSPM tool or a CNAPP, which includes CSPM capabilities along with more comprehensive cloud security capabilities.
CSPMs detect misconfigurations that exist in the control plane, and as a result, play a necessary role in maintaining a strong security posture.
Table of contents
- Key Takeaways
- Introduction
- What is CSPM?
- Understanding Cloud Security Posture Management and how it protects your cloud
- How does Cloud Security Posture Management work?
- Cloud Security Posture Management vs other solutions
- Limitations of Cloud Security Posture Management: The case for CNAPPs
- Choosing the right CNAPP for your Cloud Security Posture Management needs
- Conclusion
- CSPM FAQs







