Table of contents
Key Takeaways
- Challenge: Identifying and remediating flaws in IT systems and infrastructure, particularly for cloud-native applications, has skyrocketed in volume and complexity since cloud adoption hit mainstream.
- Prioritization of risk is more important than ever for vulnerability management programs just because of the sheer number of findings security scanners generate today across domains like application security, network security, and cloud security.
- Attack path analysis, risk scoring, and AI-driven remediation are three ways Orca helps vulnerability management teams understand granular context, prioritize risk effectively, and tackle remediation to proactively secure cloud native applications.
Introduction
With the continued growth in cloud application development, organizations must now contend with an ever-increasing number of vulnerabilities in their cloud environments. 2023 saw more than 29,000 new vulnerabilities added to the National Vulnerability Database (NVD), a record since the National Institute of Security Technology (NIST) first established the NVD in 2005. Meanwhile, the 2024 Verizon Data Breach Investigation Report finds that vulnerability exploitation increased by 180% year over year, representing a top cause of data breaches.
These figures highlight the importance and challenge of vulnerability management, the discipline of cloud security devoted to identifying, prioritizing, and remediating vulnerabilities to minimize the potential for exploitation by threat actors.
In this guide, we dive deep into vulnerability management, revealing what it entails, why it’s important, and best practices you can apply to your organization.
What is Vulnerability Management?
A branch of cybersecurity, vulnerability management focuses on identifying, evaluating, and remediating flaws in an organization’s IT systems and infrastructure. A vulnerability is a security weakness in delivered code that can contribute to a security incident.
In cloud environments, vulnerability management programs aim to equip security teams with visibility into and control over services and applications, so they can correct issues efficiently and effectively.
The primary goal of vulnerability management is to effectively manage the risks associated with the technical flaws across an organization’s attack surface. It aims to identify and resolve the most critical vulnerabilities, while diagnosing which vulnerabilities represent an acceptable risk. The challenge of vulnerability management is deciphering which vulnerabilities pose the greatest risk, so organizations can deploy resources most effectively.
Generally, vulnerability management programs focus on the following activities:
- Detecting vulnerabilities by scanning for quantity and type
- Assessing the extent to which any identified risk is susceptible to danger
- Prioritizing remediation to address the most serious issues first
- Confirming remediation by re-scanning and reporting on completed issues
Several standards help organizations prioritize how to remediate and mitigate vulnerabilities discovered in their environments. This includes the Common Vulnerability and Exposures Systems (CVE), developed by MITRE, which publishes a confirmed list of vulnerabilities and exposures. It also includes NIST’s NVD, which presents CVE data along with additional intelligence such as the severity of exploited vulnerabilities and availability of patches.
Additionally, organizations turn to the Known Exploited Vulnerabilities (KVE) Catalog, published and maintained by the Cybersecurity Infrastructure and Security Agency (CISA). KVE tracks and reports the vulnerabilities that attackers have exploited in the wild and remains a key source of intelligence since being established in 2021.
Also, vulnerability management solutions rely on the Common Vulnerability Scoring System (CVSS), which establishes the severity of a particular vulnerability. CVSS remains an important source of intelligence for vulnerability scanners. Security teams use CVSS scores to prioritize their remediation and mitigation efforts.In recent years, advanced vulnerability solutions have adopted the Exploit Prediction Scoring System (EPSS) as a more reliable measure for prioritizing risks. Unlike CVSS scores, EPSS scores take into account the likelihood of attackers exploiting a vulnerability. Attackers may not be likely to exploit a vulnerability, even if deemed critical and exploitable.
Vulnerability management vs. penetration testing
Vulnerability management focuses on identifying and helping fix security weaknesses across your cloud environments. It covers risks such as exposures, unapplied patches, vulnerable software versions, and gaps in network coverage, while also recommending remediation steps for security teams.
Penetration testing, on the other hand, attempts to exploit any flaws using a trained expert. This individual attacks weaknesses and determines the degree to which they can gain unauthorized access within a system. In this way, penetration testing takes vulnerability management a step further by acting on the findings of a vulnerability scan. Because it depends on human intervention, it’s also limited in scope, time-consuming, expensive, and less reliable compared to vulnerability management.
Some modern and advanced vulnerability management solutions offer a similar benefit to penetration tests. They run an attack path analysis that identifies and prioritizes the interconnected risks that hackers can exploit to endanger high-value assets within a cloud environment. Unlike a penetration test, however, the process is automated and continual, with new analyses performed daily or more frequently to provide ongoing value.
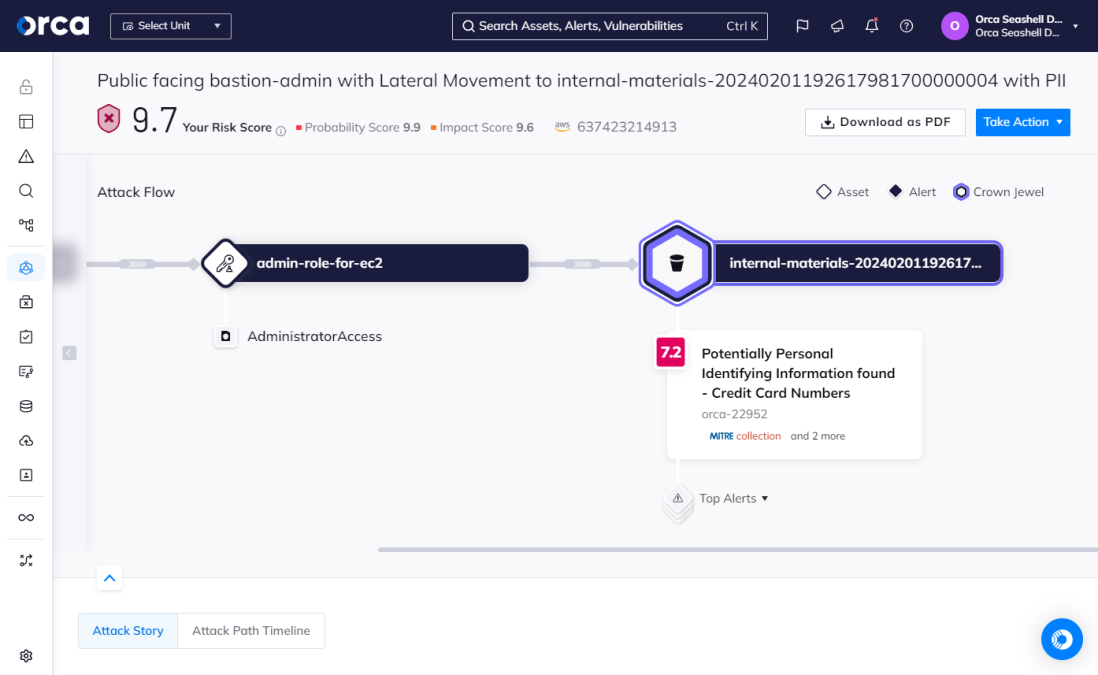
For example, the Orca Cloud Security Platform automatically identifies attack paths and prioritizes them based on severity, exploitability and potential business impact. This goes beyond what traditional VM solutions provide by considering the full context of risks in an environment and analyzing them holistically, rather than evaluating them in isolation.
Both vulnerability management and penetration testing are required for compliance with ISO 27001—an international standard for information security—and are generally used for other frameworks that don’t explicitly mandate it (e.g., HIPAA, PCI-DSS, SOC 2, etc.).
The vulnerability management process
The vulnerability management process involves a series of ongoing activities listed below.
1. Asset inventory and classification
In this phase, organizations catalog all networking components within the cloud environment, including workloads, virtual machines, containers, serverless functions, managed and unmanaged databases, applications (sanctioned and non-sanctioned), and more.
Security teams then assess cloud assets for vulnerabilities using multiple tools and methods. This may include vulnerability scanners or more comprehensive solutions such as cloud-native application protection platforms (CNAPPs). It may also involve penetration testing.
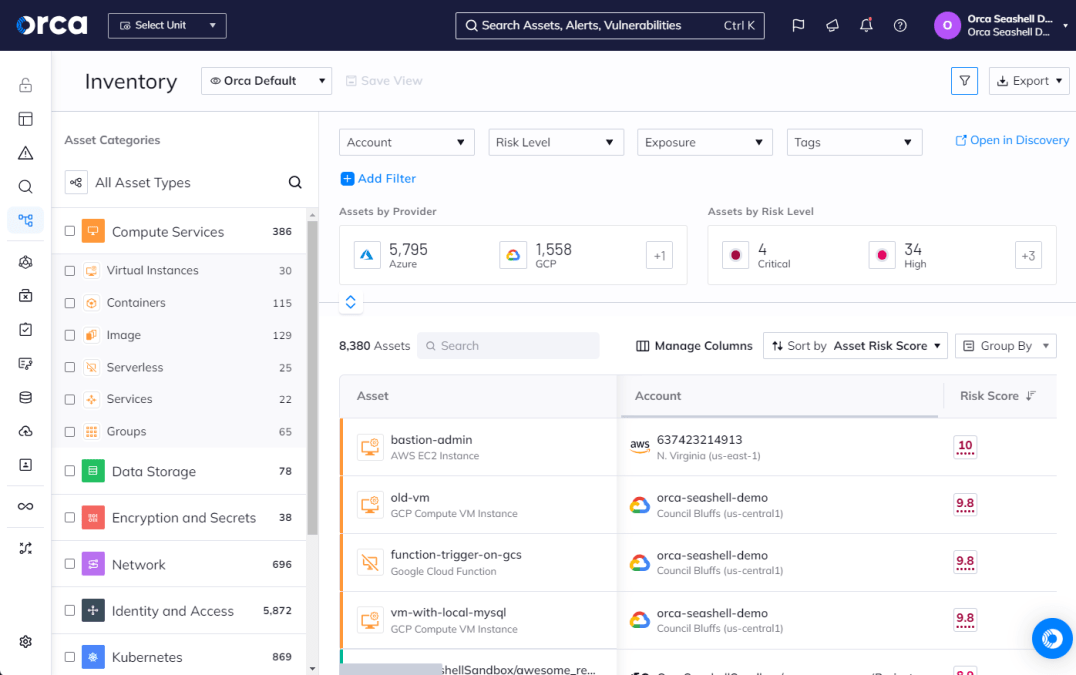
Depending on the approach used, vulnerability assessments may occur at regular intervals or continuously. For example, the Orca Cloud Security Platform, a CNAPP, scans multi-cloud environments continuously to maintain a real-time cloud inventory.
2. Vulnerability prioritization and risk assessment
After identifying all cloud vulnerabilities, organizations assess their risk level and prioritize them based on severity. This process focuses on the vulnerabilities that present the greatest risk first before turning to less severe issues.
To determine the risk level of a vulnerability, several criteria are important:
- Exposure: Is the vulnerability found on an asset that is exposed to the Internet? If so, this means it should be prioritized.
- Asset importance: High-value assets at risk usually take precedence over less important ones, regardless of the type of vulnerability involved.
- Impact of exploitation: Security teams assess the potential ramifications of a successful attack. This process considers possible financial, regulatory, reputational, and/or legal consequences.
- External severity ratings: Security teams evaluate vulnerabilities against external frameworks, such as CVSS scores.
- Chances of exploitation: Security teams determine the likelihood of vulnerability exploitation using EPSS scores or other sources.
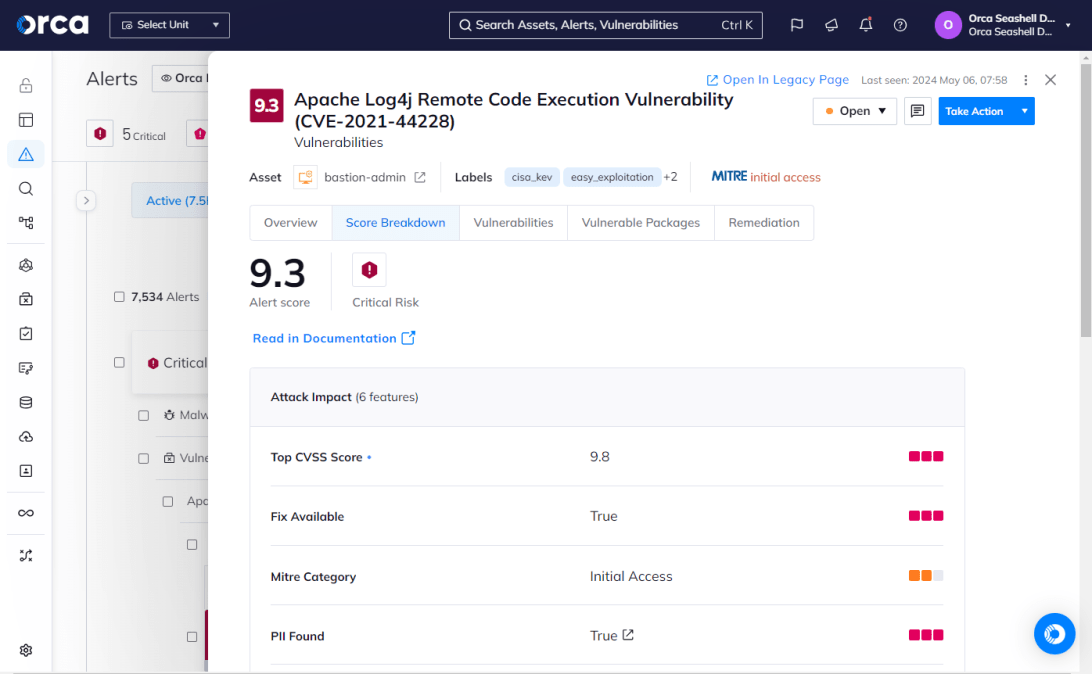
3. Vulnerability remediation and mitigation
At this stage, security teams begin fixing the prioritized risks they identified. They remediate risks that they can fully resolve, while mitigating others that would prove impractical or impossible to do so. Common remediation and mitigation activities include patching systems, encrypting sensitive data, removing files exposed to the internet, to name a few.
It’s important to note that security teams don’t address every vulnerability in their cloud environment. Rather, they ignore the flaws that present an acceptable level of risk.
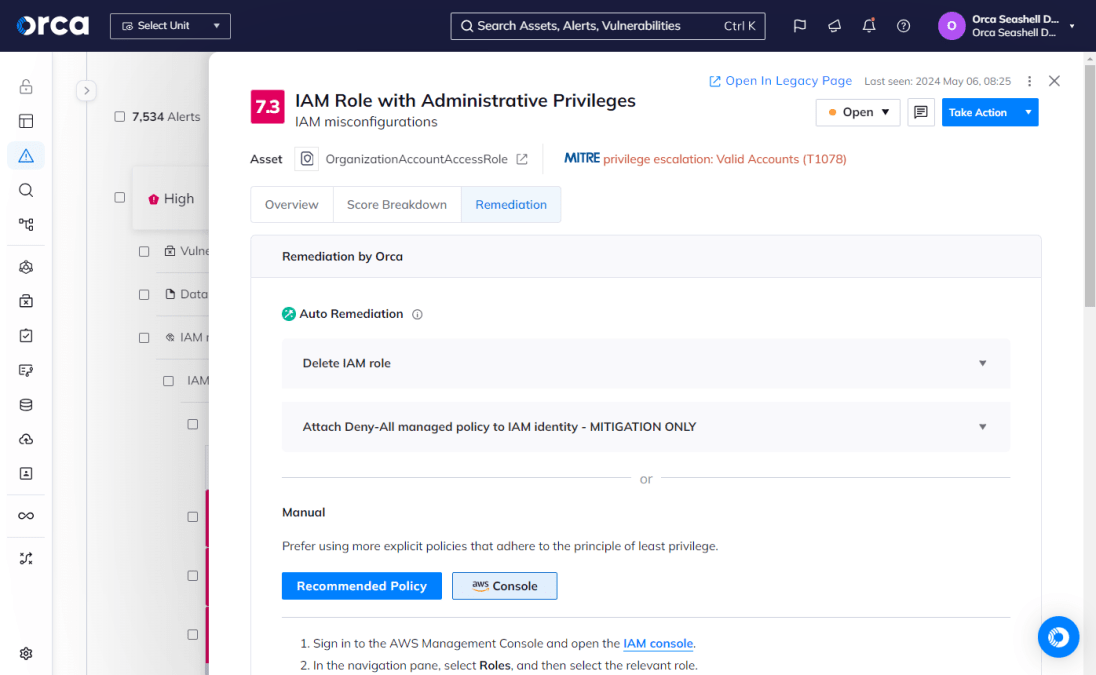
Vulnerability management solutions aid in the remediation and mitigation efforts. For example, CNAPPs like Orca Cloud Security Platform provide automatic remediation for common and complex security alerts through configured rules. This accelerates response time, reduces the workload of security teams, and minimizes the amount of unaddressed vulnerabilities.
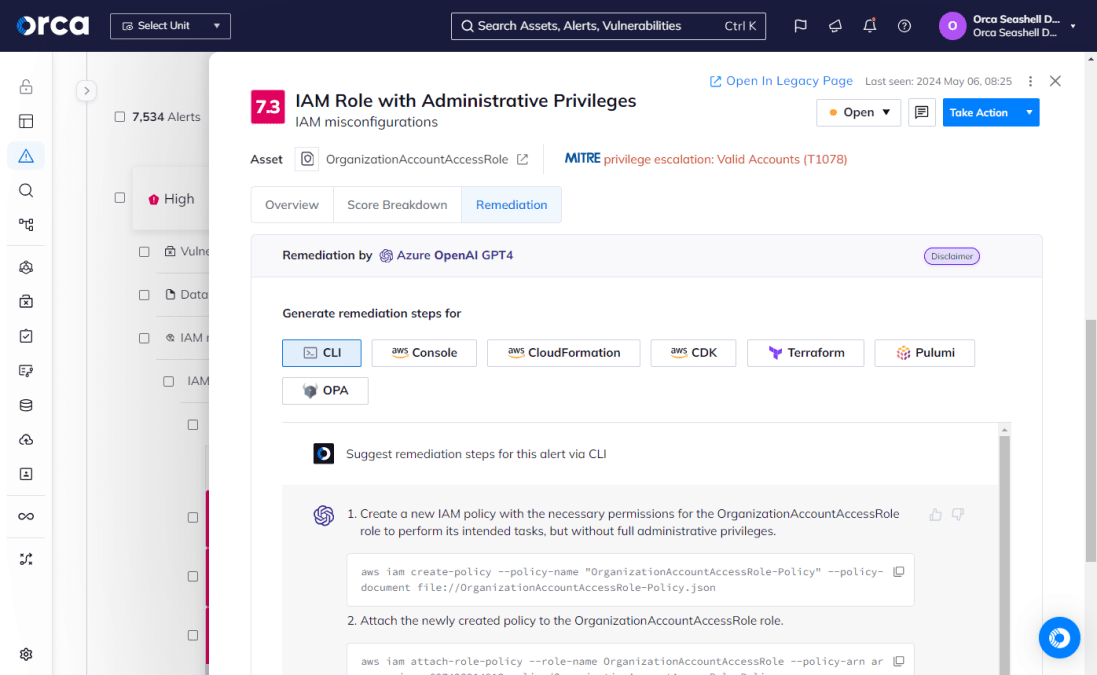
Additionally, some CNAPP solutions leverage GenAI to automate remediation and mitigation tasks. This includes Orca’s AI-driven cloud security solution, which generates on-demand remediation instructions for your specific remediation tools.
4. Vulnerability verification and monitoring
After remediation and mitigation efforts, security teams verify that vulnerabilities have been fixed or defused, and identify any new vulnerabilities in the environment. They also monitor the environment to ensure previous actions remain effective.
Security technologies like CNAPPs and some vulnerability scanners perform continuous scanning and monitoring of the environment. This automates some of the manual work involved during this stage. For example, the Orca Cloud Security Platform automatically rescans cloud assets after remediation or mitigation to check if the vulnerabilities have been resolved.
5. Reporting and continuous improvement
At this stage, security teams record their activity across all phases of the process. They share reports internally with relevant stakeholders, including executives, compliance officers, and other relevant stakeholders as appropriate.
Additionally, they also look at performance of the vulnerability management program, considering key performance indicators. These include the age of vulnerabilities, time to detect, patching rate, number of exceptions granted, and more.
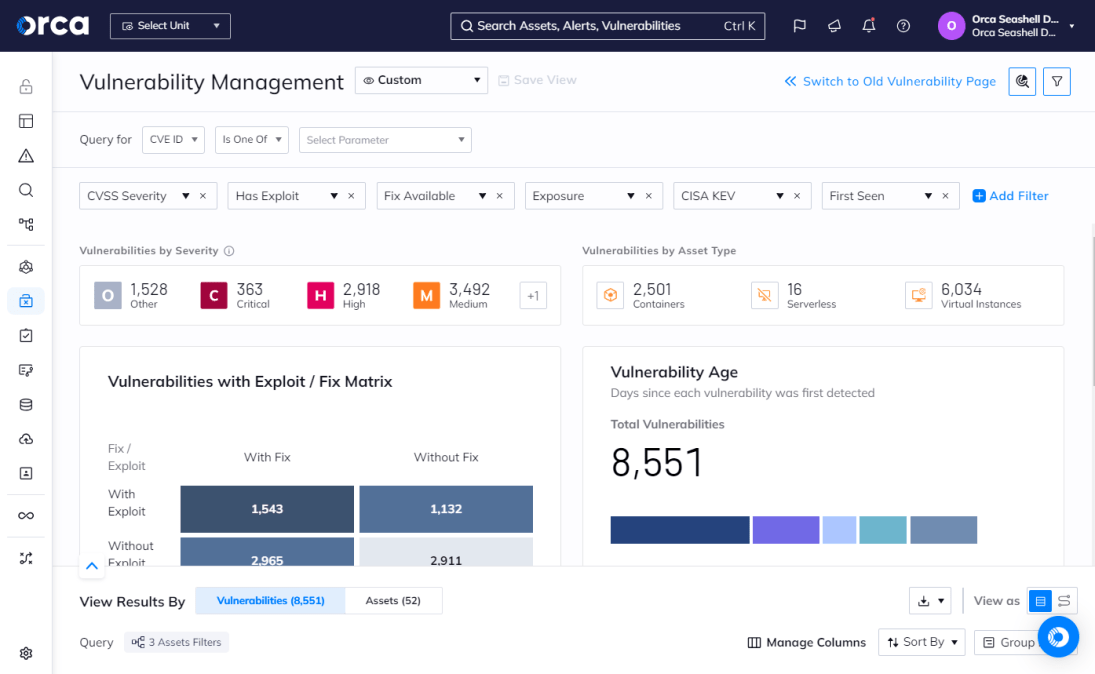
Vulnerability Management solutions can automate and enhance reporting and ongoing improvement processes. The Orca Cloud Security Platform, for example, enables security teams to download detailed reports of existing vulnerabilities, vulnerability management activities, and prescribed remediation steps. It also displays key vulnerability metrics in organized dashboards, including an SLA widget that categorizes vulnerabilities by age.
Vulnerability scanning and assessment tools
Organizations rely on one or more solutions for their vulnerability management programs. Each technology provides important advantages and limitations. While not an exhaustive list, below are the commonly used vulnerability management technologies:
Cloud security posture management (CSPM)
Cloud security posture management (CSPM) solutions detect misconfigurations and vulnerabilities in your cloud infrastructure that attackers could exploit. CSPM plays a preventative role similar to locking the doors and closing the windows on a house to stop a break-in from happening. CSPM solutions continuously monitor cloud infrastructure to identify any gaps in security policy enforcement.
Cloud workload protection platforms (CWPP)
Cloud workload protection platforms (CWPP) belong to a group of cloud security tools designed to safeguard cloud-based workloads spanning virtual machines, containers, and serverless functions. Typically, these platforms are installed as agents and prioritize the security of the cloud environment by focusing on the activities and processes taking place within an endpoint.
Cloud-native application protection platforms (CNAPPs)
CNAPPs offer a comprehensive and unified approach to managing cloud security risks. By integrating various cloud security capabilities such as CSPM, CWPP, and CIEM, along with compliance and cybersecurity risk management, CNAPPs provide a holistic view of cloud security within a single platform.
Unlike point solutions, an effective CNAPP solution ensures complete coverage and visibility across cloud environments. It can detect risks throughout the entire technology stack, including cloud misconfigurations, insecure workloads, and mismanaged identity access.
Patch management solutions
Patch management solutions automate the end-to-end patching process. These solutions monitor and identify missing patches for cloud assets, acquire and apply available patches, and assist with fixing patch malfunctions when they occur. Patch management solutions come as standalone products or integrated offerings.
Security incident and event management (SIEM)
Security incident and event management (SIEM) solutions assist organizations with monitoring and analyzing security events and activity in real-time. SIEM solutions capture intelligence from a variety of internal and external sources, which they synthesize to detect threats, facilitate incident response, enable threat investigations, monitor network activity, and more.
Vulnerability scanners
Vulnerability scanners are automated cloud security solutions that scan cloud environments for known security vulnerabilities. These scans are typically conducted externally and aim to identify issues such as insecure configurations.
How to choose the right technology
To find the optimal solution for your organization, consider the following criteria:
- Complete coverage: the solution should provide 100% coverage and visibility into your cloud estate.
- Comprehensive protection: the solution should address all types of vulnerabilities, including those related to configurations, identities and entitlements, APIs, data, containers and Kubernetes, and more.
- Context-aware: the solution should account for all important contextual factors that determine the severity of risk (e.g., internet exposure, lateral movement risk, EPSS score, sensitive data exposure, etc.).
- Consumable: the solution should empower security teams to enhance the efficiency and effectiveness of their vulnerability management activities. This calls for actionable insights, an optimal user experience, and technical integrations with productivity, security, and development tools.
For example, the Orca Cloud Security Platform provides universal coverage of the cloud estate, security for every type of vulnerability, a complete contextual analysis of risks, and presents findings that shows security teams which issues to focus on first. Orca also offers a number of key technical integrations, including bidirectional ones. Orca populates intelligence from its platform into these solutions to support existing workflows.
Vulnerability prioritization and risk assessment
Traditional vulnerability management programs determine the criticality of vulnerabilities using external intelligence from industry standards. These include CVSS scores, which are owned and maintained by FIRST, a US-based non-profit.
CVSS scores the severity of vulnerabilities on a scale from 0.0 to 10.0, with the latter being most severe. It also groups scores into four severity categories: low, medium, high, and critical. CVSS scores are calculated from metrics in three categories: Base Metrics, Environmental Metrics, and Temporal Metrics. These categories focus on characteristics of vulnerabilities.
Organizations use CVSS scores as benchmarks for deciding where to spend their time, capacity, and resources. In reality, organizations can’t fix every vulnerability that exists in their environment. For one, many vulnerabilities lack an available fix, such as a software patch released by a vendor. Also, thousands of new vulnerabilities continue to emerge every day, adding to an already extensive and unmanageable backlog. Additionally, not every vulnerability is likely to be exploited by attackers. And last, organizations remain hampered by a shortage of time, people, skills, and bandwidth.
Because organizations need to prioritize their remediation and mitigation efforts, CVSS scores help them in this regard. While useful, the benchmarks provide a limited view of risk severity and fail to account for all contextual factors that influence it.
For example, CVSS scores don’t account for the likelihood a vulnerability will be exploited. In fact, approximately only 2.7% of CVEs (critical vulnerabilities) are actually exploited. This clearly shows the limitations of CVSS scores as a risk prioritization measure. Without also considering other contextual factors, organizations run the risk of not addressing vulnerabilities that, while less critical, are more likely to be attacked by threat actors.
To address these limitations, new technology has emerged to account for other contextual factors that influence risk. These factors include:
- EPSS score
- Sensitive data exposure
- Secret keys exposure
- Access to critical roles
- Lateral movement potential
- Internet exposure
- Importance of asset to business continuity
For example, the Orca Cloud Security Platform automatically evaluates vulnerabilities using the above criteria.
Effective risk prioritization requires automation and a context-aware approach to vulnerability management that only technology can provide. Step one is investing in a cloud security solution that offers complete coverage and contextual analysis of your entire cloud estate. Both considerations are necessary to prioritize risks accurately and without bias. Solutions with incomplete visibility into your cloud environments will only prioritize the vulnerabilities they can see, while neglecting those that may present more risk to your organization.
Agentless-first solutions like the Orca Cloud Security Platform provide 100% coverage of and visibility into your cloud estate. Using our patented SideScanning™ technology, Orca collects data from the runtime block storage of workloads and cloud configuration data via API to gain a comprehensive, fully contextualized view of your cloud environment(s).
Best practices for vulnerability management
To establish a successful vulnerability management program, focus on the early detection and mitigation of vulnerabilities, as well as implementing measures like software hardening in the production environment. The practical techniques outlined below can assist businesses in developing effective cloud vulnerability management practices.
1. Gain complete cloud visibility
An effective cloud vulnerability management program begins with an in-depth and comprehensive inventory of your cloud estate. This focuses on ensuring full coverage of every cloud asset and gives security teams a complete inventory of their environment(s), which allows them to detect vulnerabilities in network and endpoint parameters. It also accelerates their remediation efforts.
2. Scan for vulnerabilities continuously
To ensure the resolution of vulnerabilities, conduct continuous and automated scans of applications before deployment. In the cloud, where programs are often packaged in containers, image scanning helps establish a secure baseline for operating systems. Additionally, vulnerability code checks can be integrated into CI/CD pipelines using tools such as software composition analysis (SCA) and static application security testing (SAST) analyzers.
3. Integrate an automated patch remediation policy
Remediation is a crucial phase in vulnerability management following vulnerability detection. Integrating an automated patch remediation policy enables prompt issue resolution, minimizes the attack surface, and safeguards the cloud environment against potential network exploits. To expedite patch remediation, organizations can establish vulnerability remediation metrics like the CVSS and the mean time to remediate (MTTR).
4. Adopt comprehensive reporting
Monitoring your vulnerability management aids in visualizing and contextualizing threats within the cloud environment. A robust vulnerability management strategy should include a comprehensive set of analytical reports that consistently enhance security posture by addressing any bottlenecks in cloud deployments.
Conclusion
Vulnerability management is a vital area of cloud security that continues to gain importance. As vulnerabilities surge, organizations need to become more precise and intentional about how they remediate and mitigate flaws in their cloud attack surface. That calls for adopting a comprehensive cloud security solution that effectively prioritizes and contextualizes risk. This lays the foundation of any successful vulnerability management program and should serve as the focus of your strategy.
About Orca Security
Orca Security offers an advanced, comprehensive vulnerability management solution for AWS, Azure, Google Cloud, Kubernetes, and other cloud service providers (CSP). The Orca Cloud Security Platform combines vulnerability management with CWPP, CSPM, CIEM, container and Kubernetes security, API security, Data Security Posture Management (DSPM), and AI security for unified cloud security.
With full coverage of your cloud estate, and comprehensive protection against all types of vulnerabilities, Orca effectively prioritizes the most critical risks in your environments, giving your security teams precise guidance for their remediation and mitigation efforts.
Leading organizations trust their cloud security to Orca, including Autodesk, Unity, Gannett, Digital Turbine, Postman, SAP, Wiley, Lemonade, and many more.
FAQs
What is the difference between vulnerability management and vulnerability assessment?
While the terms vulnerability management and vulnerability assessment are often used interchangeably, they mean different things. Vulnerability management refers to a collection of ongoing activities, technologies, and techniques. Meanwhile, vulnerability assessment is one function among many in a vulnerability management program.
Organizations conduct vulnerability assessments by using technology to scan their environments for security weaknesses that require remediation or mitigation. In this way, vulnerability assessments provide necessary and crucial intelligence for vulnerability management.
How often should vulnerability scans be conducted?
According to the Center for Information Security (CIS), organizations should scan their cloud environments at least quarterly, if not more frequently, depending on their unique circumstances. Factors that may call for more frequent scans include the storing and processing of sensitive data, unique compliance requirements, value of business services, etc.
While the CIS recommendation is helpful, best practice is to rely on a solution like Orca Cloud Security Platform to perform continual vulnerability scans that update daily.
What are common tools used in vulnerability management?
Common vulnerability management tools include CWPP, CSPM, CNAPP, patch management solutions, SIEM, and vulnerability scanners. Except for CNAPP solutions, each technology addresses a specific use case in vulnerability management. This explains why organizations prefer CNAPPs for their vulnerability management, which unifies the capabilities of multiple point solutions.





