Cloud services permeate every organization, with two-thirds of enterprise infrastructure now based in the cloud.
Cloud-native workloads are also changing how companies are managing their businesses. By 2025, Gartner estimates that more than 95% of new digital workloads will be deployed on cloud-native platforms, up from 30% in 2021.
This massive shift has provided security leaders with an opportunity to consider how to innovate their approaches to solve their top cloud security challenges. With the pervasiveness of cloud-native workloads and the potential impacts on alert-fatigued, understaffed security teams, there’s never been a better time to reconsider how cloud security risks are being managed.
As today’s threat actors are increasingly attacking web applications and misconfigured clouds as primary vectors, building a foundation for a comprehensive cloud security program that integrates compliance, vulnerability management, cloud workload protection, threat detection and rapid response, along with cloud risk management in one integrated platform proactively is imperative.
Read on for some of the most pressing cloud security challenges security leaders are facing, and how four specific best practices that can help quickly enable cloud security and DevOps teams tackle these cloud security challenges now.
Shared responsibility and the public cloud
Securing the public cloud estate is a shared responsibility between the cloud service provider (CSP) and the organizations consuming those services.
Generally speaking, where the CSP is an infrastructure as a service (IaaS) provider, the CSP is responsible for the underlying infrastructure, such as the virtual machines, disks, and networks. The organization is responsible for securing the OS and software stack required to run their applications, as well as their data.
Many enterprises struggle with managing the complexity, cost, and consistency of security controls across their cloud ecosystems.
Case in point: roughly 80% of organizations have experienced a cloud-related breach, according to a recent survey of US-based CISOs. These struggles increase the security risk to the enterprise itself and its value chain, including its clients, vendors, and partners.
Multi-cloud environments and alert fatigue
There are numerous challenges with deploying and consuming cloud services from today’s top CSPs. For many organizations, the biggest challenge relates to staffing security operations for multi-cloud environments.
One of the most pressing risks that arises from using multi-cloud environments and staffing is the number of alerts coming from cloud service providers. Without experienced staff in place, security leaders have to find ways to triage hundreds of unprioritized cloud security alerts from their CSPs and security tools.
If a critical alert is missed, i.e., a cloud instance is misconfigured, an expensive breach could occur. A security leader can minimize that risk by prioritizing critical alerts for the security team to remediate.
Recently, Orca Security commissioned a survey of 813 IT Security professionals to understand the impact of alert fatigue on security teams.
As illustrated below, 81% of security practitioners reported their organization is using a multi-cloud strategy with more than one cloud platform, and 55% reported their company was using three or more public cloud platforms.
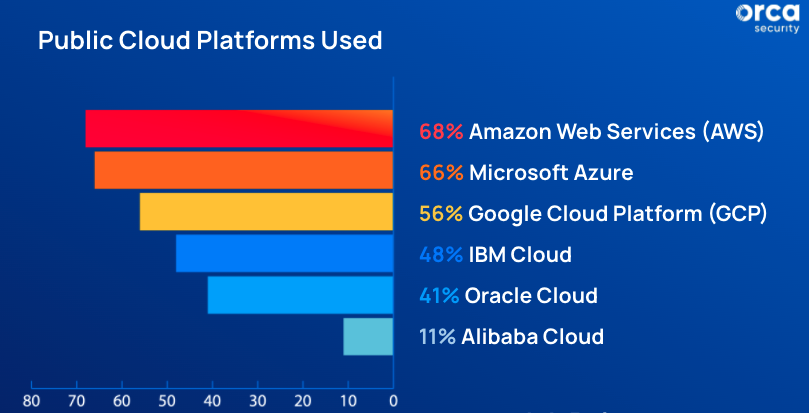
Number of public cloud platform used – Orca Security’s 2022 Alert Fatigue Report
As more organizations make the move to multi-cloud environments, security teams are adopting different types of disconnected tools that contribute to daily alert volume. In the same survey, 59% of respondents reported receiving more than 500 security alerts every day from their public cloud security tools.
What’s the impact of these unprioritized alerts in multi-cloud environments? The security practitioners surveyed reported that up to 55% of critical alerts are simply not getting investigated on a day-to-day basis.
Alert-fatigued security teams are likely to be negatively impacted as organizations seek to expand cloud deployment across multiple CSPs with multiple point solutions and agents to protect their public multi-cloud estate. As the adoption of multi-cloud environments takes hold, security leaders can mitigate the risk of alert fatigue with better cloud security technology and/or more experienced (and expensive) security staff.
Managing data security in the cloud
Another cloud security challenge is data security. Organizations often don’t know what data is in the cloud and where it is stored, which means sensitive data could lack the controls required by standards and regulations and/or be publicly accessible, increasing the risk of a compliance violation and data loss.
Implementing proper access controls is also a challenge in the public cloud. Organizations must ensure that only authorized users and critical systems can access data.
A simple four-step approach to cloud security
Organizations should take a basic block-and-tackle approach to cloud security by following these four steps.
1. Build a cloud asset inventory
It’s mission critical for enterprises to understand what they have and where it is in their cloud ecosystem. This includes the number of VMs or containers, public cloud workloads, the number of VPCs, databases, types of data, users, and so on. A cloud security solution should be able to generate a complete asset inventory that does not miss a single asset. In addition, it should be able to find vulnerabilities fast and effortlessly. A cloud asset inventory sounds simple, but when a zero-day vulnerability like log4j hits, security teams need to have a reliable way to identify exactly what assets they have in the cloud estate for rapid response.
2. Get full cloud visibility
The next step is to get full visibility of the cloud estate – whether that’s a single cloud provider’s infrastructure, or a combination of AWS, Azure, or Google Cloud. Visibility enables organizations to see their cloud assets, including data, in context, and respond quickly as needed. Security leaders with visibility have a complete understanding of what is going on inside their cloud environment, including the cloud infrastructure level, operating systems, applications and data, at any given time.
3. Understand identity and access permissions
The next step is to understand what identity and access looks like within this cloud ecosystem. For example, what server or VM can access what VPC or database, what resources do developers or administrators have access to, and how can data be accessed. To manage risks associated with hybrid and multi-cloud deployments, having identity and access management in place for cloud resources is key.
4. Apply comprehensive cloud security controls
Once these foundational aspects are understood and addressed, enterprises can apply security controls to fully manage their cloud risks succinctly. Controls for compliance, malware detection, vulnerability management, and shift left security can be integrated to provide greater flexibility at scale to secure the cloud estate.
How Orca Security can help with cloud security
With Orca Security, security leaders gain the advantage of our agentless sidescanning technology that provides comprehensive visibility into the entire cloud ecosystem in minutes with one comprehensive platform. This answers the question of what’s in the cloud or multi-cloud environment and where it is. This innovative approach to cloud security technology helps DevOps identify common misconfigurations, compliance events, and critical security vulnerabilities that pose the highest levels of risk to the enterprise. The Orca Security platform deploys in minutes across multiple cloud ecosystems without the need to install agents, which eases the burden on security teams, reduces enterprise cyber risk, and improves overall cloud visibility and hygiene.
Ready to try it out? With Orca Security’s free 30-day trial and cloud risk assessment, you can have 100% visibility into your entire cloud security estate in minutes. This gives you and your team the ability to quickly identify and remediate critical risks to sensitive data, such as malware, lateral movement, and misconfigurations, in your cloud environment. Discover how your cloud security and DevOps teams are enabled with continuous vulnerability management and shift left security built to reduce workflow friction.







