According to the ENISA Threat Landscape Report 2023, the variety, quantity, and consequences of cyberattacks in the European Union (EU) have increased significantly in the past year. Threat actors concentrated their attacks on critical industries like public administration, health, and digital infrastructure, attempting to take advantage of the more than 12 percent increase in industry-wide vulnerabilities observed over this period.
These evolutions in the threat landscape help explain why the EU is introducing new legislation to bolster cybersecurity controls and standards across its 27 Member States. Among them is the NIS2 Directive, a framework designed to usher in a safer, more secure digital future for EU companies, citizens, and other stakeholders.
In this post, we examine the NIS2 Directive to uncover what it entails, why it matters, and how you can best prepare for implementing it in your organization. We also detail how the Orca Platform can help support your NIS2 compliance efforts.
What is the Network and Information Security (NIS2) Directive?
The Network and Information Security (NIS) Directive was first introduced in 2016 in an attempt to strengthen cybersecurity in the EU and across its Member States. In December 2022, the EU repealed and replaced the legislation with the NIS2 Directive, a more comprehensive and stringent set of requirements aimed at addressing the limitations of the original legislation, including a lack of uniform security practices across the EU. Among other changes, NIS2 expands the scope of the regulation to include additional industries, risk management and incident reporting standards, and more disciplines of cybersecurity, including supply chain security.
Enacted on January 16, 2023, the NIS2 Directive requires all EU Member States to formally adopt its measures and make them national law by October 17, 2024. Once ratified by individual Member States, NIS2 measures go into force and mandated compliance begins.
Who must comply with NIS2?
NIS2 requires organizations deemed Essential or Important to comply with its requirements.
Essential entities include any large organization operating in the industries below. NIS2 defines large organizations as companies with 250 employees or more, or an annual turnover and balance sheet total of at least €50 million and €43 million, respectively.
NIS2 Essential sectors
- Aerospace
- Banking
- Digital infrastructure
- Drinking water
- Energy
- Financial market infrastructure
- Government services
- Healthcare
- Managers of ICT services
- Transport
- Wastewater
NIS2 considers entities as Important in two cases. First, they meet the definition of medium-sized and operate in the sectors listed previously. Alternatively, they meet the definition of large- or medium-sized and operate in the sectors listed below. NIS2 considers entities as medium-sized if they employ at least 50 employees, or they maintain an annual turnover and balance sheet total of at least €10 million.
NIS2 Important sectors
- Chemicals
- Digital providers
- Food
- Manufacturing
- Postal and courier services
- Research
- Waste management
NIS2 distinguishes between Essential and Important entities based on their importance to society and the impact a business disruption would cause.
Essential entities must undergo proactive oversight of compliance, including before a violation. Meanwhile, Important entities are subject to monitoring after an incident of non-compliance is reported.
The classification of Essential and Important entities marks a departure from the original NIS Directive, which covered Operators of Essential Services (OESs) and Relevant Digital Service Providers (RDSPs). Because of this change, NIS2 increases the number of organizations that must comply with the regulation.
NIS 2 also deviates from the original legislation in another important way: penalties for compliance violations. Like the General Data Protection Regulation (GDPR), the NIS2 poses stiff fines for covered entities. The measure stipulates that Essential entities can face fines up to €10 million or 2% of total worldwide annual turnover, whichever is greater. Meanwhile, Important entities can be subject to paying the higher of €7 million or 1.4% of total worldwide annual turnover.
What are the specific requirements of the NIS2 Directive?
The detailed requirements of NIS2 won’t become available until the regulation goes into effect on October 17, 2024. Until then, guidance remains limited to the 9 chapters of the NIS2 Directive listed below, which contain a total of 46 articles:
- Chapter 1: General Provisions
- Chapter 2: Coordinated Cybersecurity Frameworks
- Chapter 3: Cooperation at Union and International Level
- Chapter 4: Cybersecurity Risk-Management Measures and Reporting Obligations
- Chapter 5: Jurisdiction and Registration
- Chapter 6: Information Sharing
- Chapter 7: Supervision and Enforcement
- Chapter 8: Delegated and Implementing Acts
- Chapter 9: Final Provisions
For covered entities, Chapter 4 contains the important security requirements that Member States must use to hold them accountable. These include Article 20, Article 21, Article 23, and Article 24.
Article 20: Governance
NIS2 requires Member States to hold the management of entities accountable for overseeing and approving cybersecurity risk management measures taken by their organization. It also requires management to undergo training and recommends entities administer it regularly to employees for improved security awareness.
Article 21: Cybersecurity risk management measures
NIS2 stipulates that Member States ensure entities take the proportionate technical, operational, and organizational measures to effectively manage the security of their information systems. This means that the measures should account for the entity’s risk exposure, potential for a security incident, and consequences of an incident—the latter including the impact on society.
NIS2 prescribes organizations to take an all-hazards approach to adequately prepare for all types of security incidents and protect their information systems. This means adopting measures that cover at least the following aspects of cybersecurity:
- Risk analysis and information security policies
- Incident handling
- Business continuity
- Supply chain security
- Vulnerability handling and disclosure
- Procedures to assess the effectiveness of cyber risk management
- Computer hygiene practices and cybersecurity training
- Policies and procedures for cryptography and encryption
- Human resources security, access control policies and asset management
- Use of multi-factor authentication and secure communication systems
Article 23: Reporting obligations
NIS2 increases the reporting obligations for entities that experience a significant security incident. Organizations that experience a significant incident must report it to the appropriate computer security incident response team (CSIRT) or competent authority (CA) in four phases:
- Early warning – Within 24 hours of becoming aware of a security incident, organizations must provide an early warning that indicates whether they suspect that the incident was caused by unlawful or malicious activity.
- Incident notification – Within 72 hours of becoming aware of a security incident, entities must provide an update of the early warning and provide an assessment of the incident, its severity, its impact, and any indicators of compromise (IoC).
- Status updates – As requested by the CSIRT or CA, organizations must report on any status updates.
- Final report – Within one month of the incident notification, entities must submit a final report.
Additionally, NIS2 requires entities to notify customers of any significant cyber threat that could potentially affect them. This communication should include any measures they should take to mitigate or remediate the threat.
Article 24: Use of European cybersecurity certification schemes
Under Article 24, Member States may require covered entities to use certain information and communication technology (ICT) products, services, and processes that are certified under European cybersecurity certification schemes. This helps ensure that organizations can meet their cybersecurity risk management requirements.
3 best practices for complying with the NIS2 Directive
While the exact requirements of NIS2 have yet to be announced, four best practices can help you better prepare for when that time comes. They include the following:
1. Inventory your digital assets and risks.
No matter what NIS2 Directive exactly entails, it will undoubtedly require you to identify, monitor, and report on your digital assets, business processes, and risks. That presents unique challenges for organizations in the era of cloud computing. Most organizations (64%) maintain more than half of their IT resources in the public cloud, according to Orca’s 2024 Cloud Security Strategies Report. Meanwhile, many companies lack visibility into their cloud environments, which are dynamic and constantly changing day-to-day.
That illustrates the importance of adopting a cloud security solution that automatically provides both 100% coverage of your cloud environments and the ability to detect all types of risk.
The former requires an agentless-first solution, which covers the blindspots missed by agent-based technology. The latter calls for solutions that detect vulnerabilities, misconfigurations, malware, lateral movement risk, API risk, data risk, identity and access risk, AI risk, and more.
With automatic coverage and comprehensive risk detection of your entire cloud estate, you can effectively manage risks—which will certainly be a core requirement of NIS2.
2. Automate compliance monitoring and reporting
Compliance is a time-intensive and resource-consuming endeavor on its own, not to mention when coupled with the demands of operating a business. The more you can automate compliance, the better. Automation can help you free up scarce resources and capacity and also approach compliance proactively, rather than racing to prepare for an upcoming audit.
Building on the previous best practice, you should also look for cloud security technology that ingests the NIS2 framework and can determine your compliance status automatically and continuously—using the full coverage and comprehensive risk detection mentioned previously.
Additionally, you should find solutions that not only present your compliance status on-demand, but also allow you to export it as a report to share with external or internal stakeholders as needed.
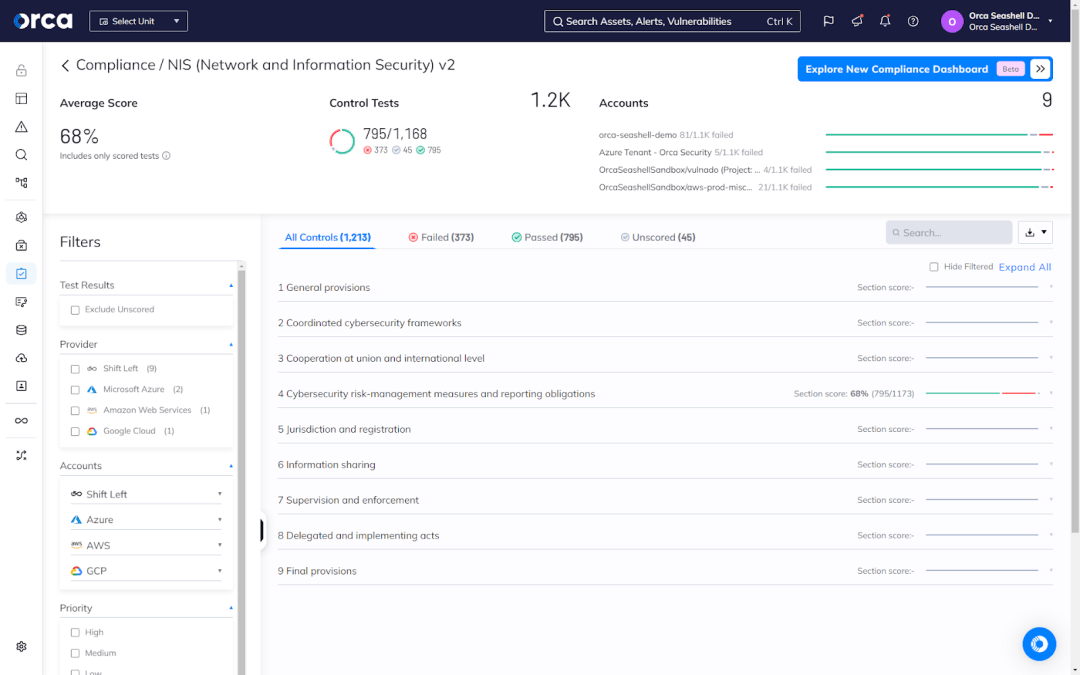
3. Streamline your remediation processes
Detecting a vulnerability is one of your important responsibilities under compliance rules. Yet so is effectively and efficiently remediating any discovered issues. In addition to finding cloud security solutions that offer full coverage and comprehensive detection, you should also favor solutions that offer dynamic risk prioritization.
This means the capability to continuously assess risk using a number of data points, as well as organizing and presenting risks according to criticality. Importantly, the data points used for risk analysis should include factors outside your cloud estate—such as an EPSS Score, which rates the probability of a vulnerability being exploited—and inside your cloud environments—such as the relationship between risks and assets.
Solutions that accurately prioritize risks allow your teams to focus on remediating the most pressing compliance issues, saving them from time-consuming investigations and unnecessary delays that increase risk exposure.
Meanwhile, you should also look for solutions that provide features for automating and streamlining aspects of remediation. Sophisticated technology can allow you to automatically generate remediation instructions, integrate remediation tasks with tools used by other functional teams, as well as automatically remediate certain issues based on predefined criteria.
How Orca helps with compliance for NIS2 Directive
The Orca Cloud Security Platform is an agentless-first cloud security solution that identifies, prioritizes, and remediates security risks and compliance issues across the most popular public-cloud environments, including AWS, Azure, Google Cloud, and Kubernetes. Importantly, Orca offers the following capabilities to support your multi-cloud compliance efforts.
Complete coverage and comprehensive risk detection for NIS2
Orca’s patented SideScanning™ technology provides full visibility of your entire cloud estate. SideScanning achieves complete coverage by collecting data—with read-only access—from your workload’s runtime block storage, as well as retrieving cloud configuration metadata via APIs. This enables Orca to not only cover your cloud infrastructure, but all your workloads too—e.g., virtual machines, containers, serverless functions, etc.
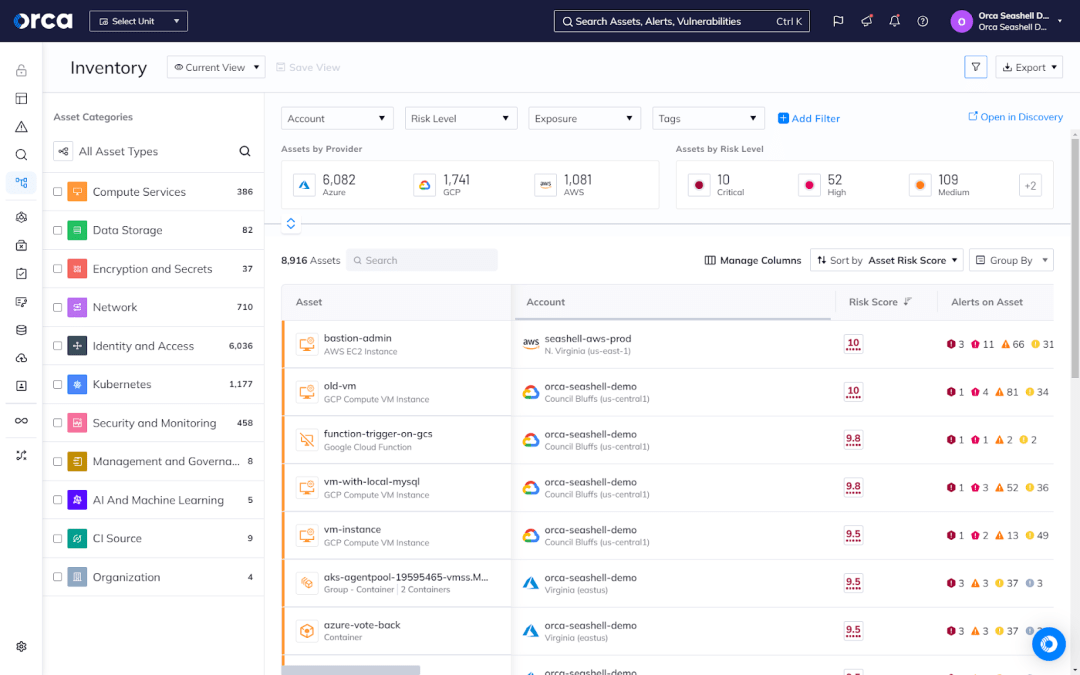
The Orca Platform also detects and helps remediate the full spectrum of risks that can arise in your cloud estate. This includes vulnerabilities, misconfigurations, and risks associated with your APIs, AI models, identities and permissions, sensitive data, and more.
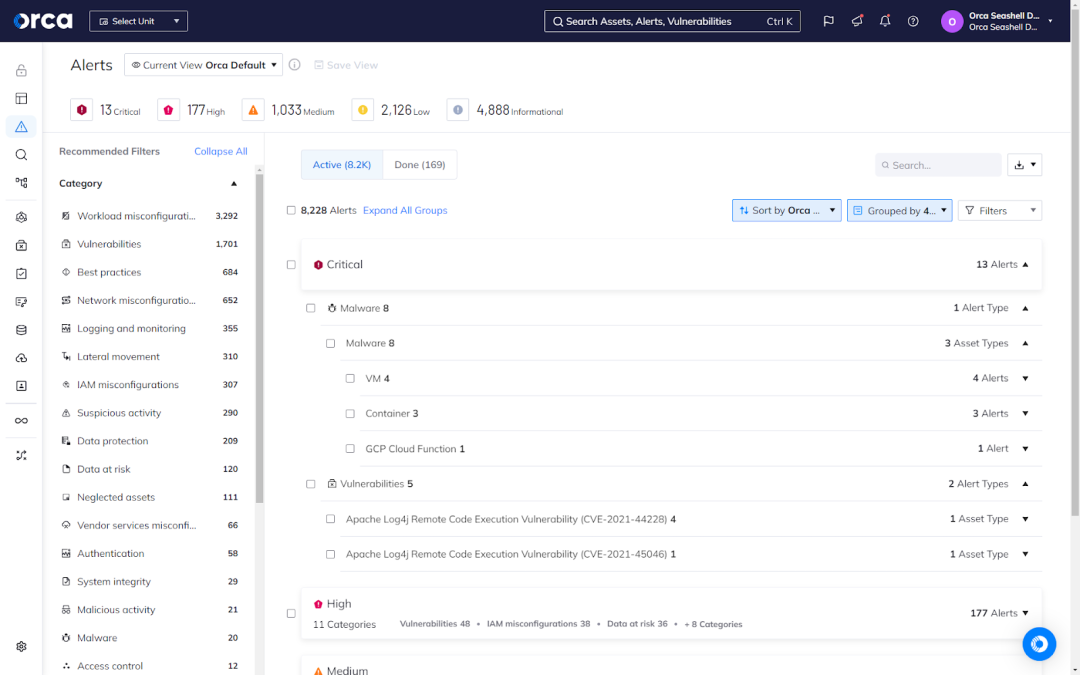
Orca’s complete coverage and comprehensive risk detection creates the conditions needed to achieve compliance with NIS2, eliminating the potential for violations due to blindspots in your estate.
Automatic NIS2 compliance monitoring and reporting
Orca automates your compliance monitoring and reporting efforts. It offers more than 150 up-to-date compliance frameworks covering most major regulations and industry standards, including CIS benchmarks.
Once you select a framework, Orca automatically assesses and displays your current compliance status, including an average compliance score. It also allows you to see the framework in four views: All Controls, Failed Controls, Passed Controls, and Unscored. These views show every control included in the framework, non-compliant controls, compliant controls, and controls that require intervention outside the Orca Platform, respectively.
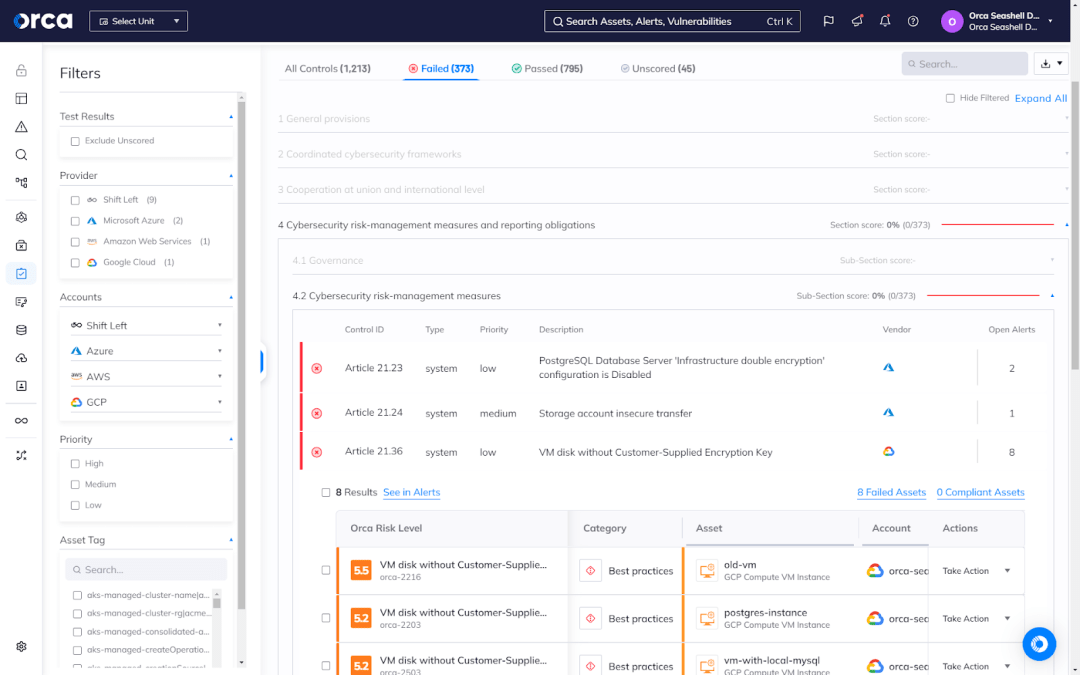
Using the Failed Controls view, you can access each failed control to see the relevant Orca alerts resulting in non-compliance. You can also remediate them directly from the framework.
Importantly, Orca updates the framework on a continual basis to ensure that your compliance status reflects the dynamic changes occurring in your cloud estate.
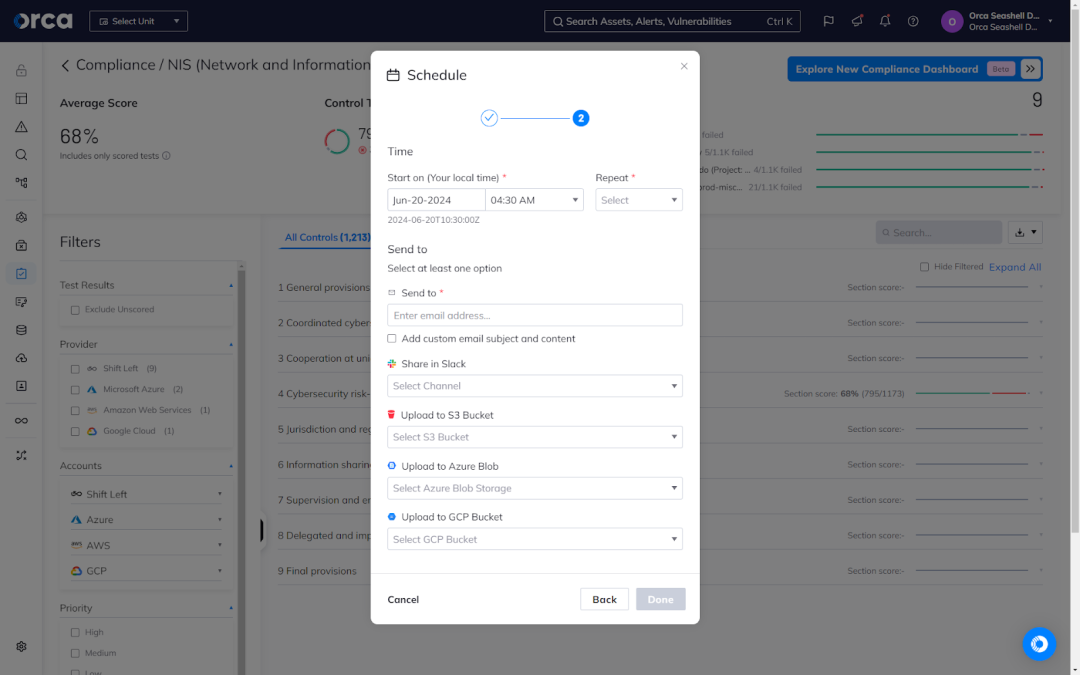
Orca also streamlines the compliance reporting process by allowing you to automatically generate ad hoc or recurring compliance reports. You can create reports in PDF format for sharing with high-level stakeholders (internal or external) as well as JSON or CSV format to provide more granular information, such as remediation instructions. You can also schedule reports to send automatically on a daily, weekly, monthly, or quarterly basis to an email address, Slack channel, or storage bucket.
Together, Orca’s automatic compliance monitoring and reporting capabilities greatly eases the burden of compliance on your teams. It also makes continuous compliance—staying compliant proactively on an ongoing basis—feasible and beneficial.
Enhanced remediation and automation for NIS2
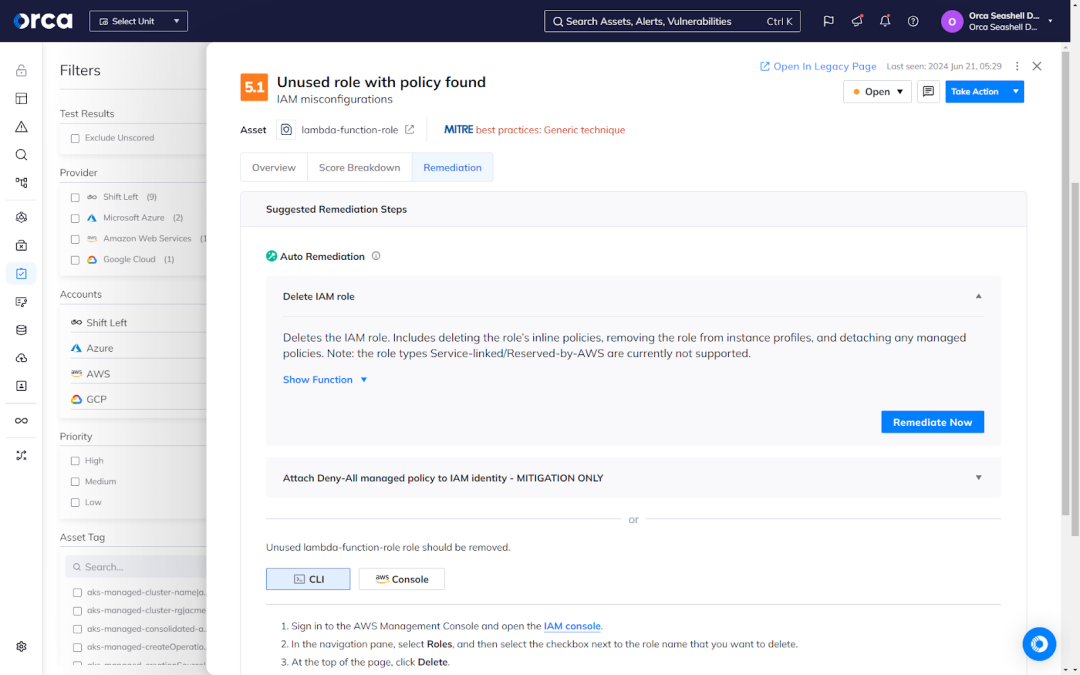
Orca empowers your teams to remediate issues efficiently and effectively. Each Orca alert features multiple remediation options to provide you with maximal flexibility. This includes detailed remediation instructions automatically generated and vetted by Orca, the ability to auto-remediate certain risks with one click, and AI-powered remediation. The latter leverages Azure OpenAI, Amazon Bedrock, or Vertex AI to automatically generate step-by-step remediation instructions and code (when applicable) for your specific remediation tool (e.g., Terraform, Pulumi, AWS CloudFormation, Google Cloud Console, Azure Console).
Orca also offers a two-way integration with Jira and ServiceNow, enabling you to create a ticket containing the remediation steps directly from an Orca alert. Once the ticket is closed, Orca automatically verifies the issue has been resolved and updates its status accordingly. In the event the issue remains unresolved, Orca will reopen the ticket for the appropriate team member to address.
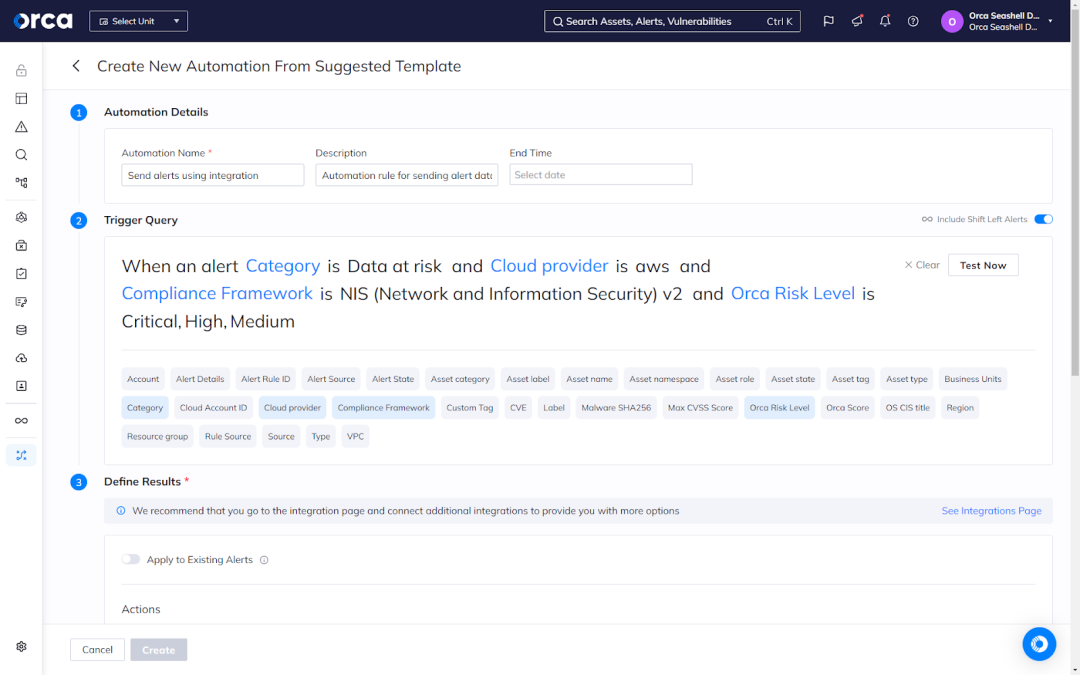
Additionally, Orca offers Automations, which allow you to automate your compliance workflows for the NIS2 framework. The Automations feature enables you to automatically send notifications for specific types of risks, risk severity thresholds, or both; auto-remediate specific kinds of alerts; automatically integrate alerts with your SIEM/SOAR solution; and more.
Orca’s remediation and automation capabilities also help you achieve a model of continuous compliance for NIS2 and any other frameworks.
Custom frameworks for your bespoke needs
Most organizations today must comply with multiple regulatory requirements or industry standards. Without the right cloud security solution in place, that can significantly increase the burden and complexity of compliance for busy teams.
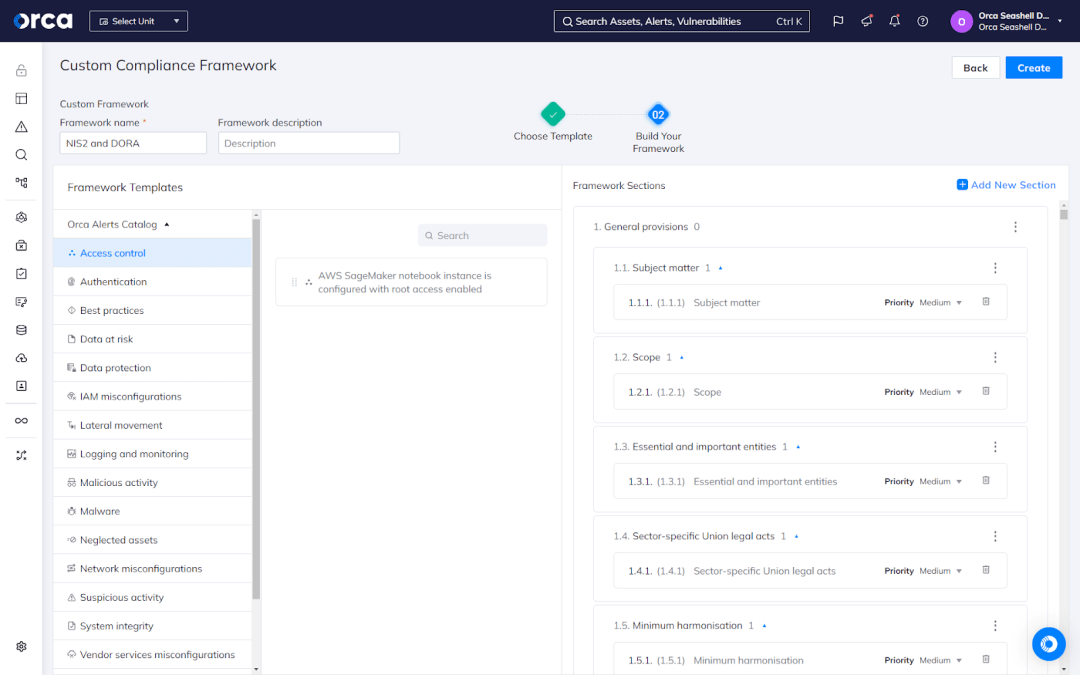
Fortunately, Orca offers the Custom Frameworks feature, enabling you to combine two or more frameworks—entirely or partially—from Orca’s extensive library or create one from scratch. Additionally, Orca allows you to further customize your framework by adding alerts from Orca’s catalog of more than 2,200, which cover the full spectrum of use cases.
Once you create your compliance framework, Orca automatically and continuously assesses and displays your current status.
Learn more about how Orca enhances compliance for NIS2 Directive
Orca enables your organization to achieve continuous NIS2 compliance for your multi-cloud environments—easily and continuously. It offers automated features for compliance monitoring, reporting, and remediation, as well as more than 150 up-to-date compliance frameworks, including CIS benchmarks.
The Orca Cloud Security Platform is certified across 24 cloud frameworks by the Center of Internet Security (CIS Benchmarks). This certification validates that Orca accurately identifies any configurations that deviate from best practices in more than 60 CIS Benchmarks.
To see how the Orca Platform can ease and enhance your compliance efforts, schedule a demo.





