Organizations are continuing full speed ahead in moving much of their sensitive data to the cloud. Cybersecurity Ventures predicted in 2020 that the total amount of data stored in the cloud will reach 100 zettabytes by 2025, or 50 percent of the world’s data at that time, double the amount from just a decade prior. Furthermore, according to The State of Data Privacy and Compliance, a 2022 report from Enterprise Strategy Group (ESG), “sensitive classified data in public clouds is expected to nearly double (37% to 61%) over the next 24 months, as 61% of organizations expect more data will be categorized as sensitive.”
It naturally follows that securing that sensitive data in the cloud should be at the top of the list for CISOs and security teams.
Towards the end of 2022, Techstrong Research polled its community of DevOps, cloud native, cybersecurity, and digital transformation readers to take their pulse on data security posture management (DSPM). The resulting ‘PulseMeter Report’ found:
- Too many organizations don’t know the location of their sensitive data in the cloud
- Security teams are using a diverse set of approaches to restrict access to sensitive data, and are concerned about a range of risks to that data
- Organizations expect their central cloud security platform to provide DSPM capabilities
Discovery of Sensitive Data in the Cloud is Lagging
The research found that while organizations say more sensitive data is being stored in the cloud than in on-premises data centers, many organizations don’t know where their sensitive data is located, as almost 50% of respondents conduct infrequent or no discovery.
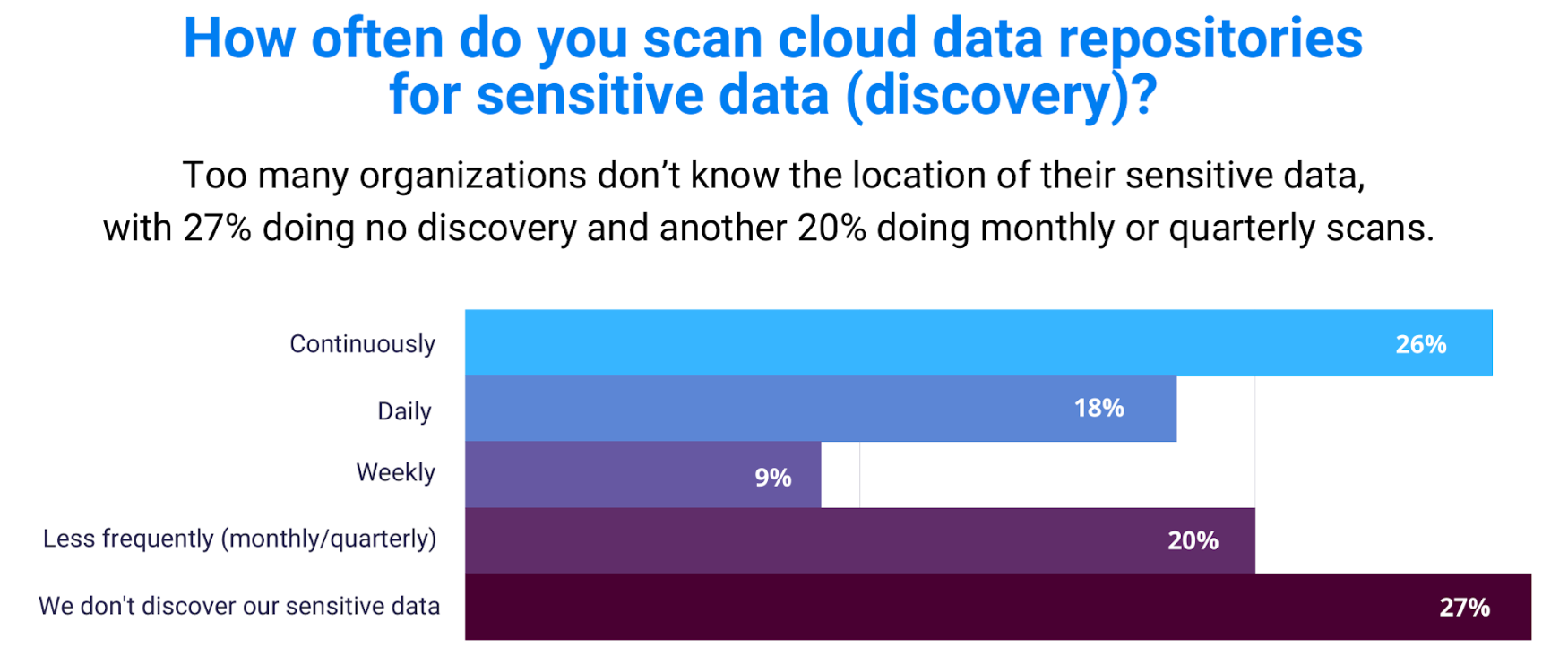
When asked “How often do you scan cloud data repositories for sensitive data?”, nearly half of respondents answered that they perform infrequent (20%) or no sensitive data discovery at all (27%).
This is concerning. Given the dynamic, distributed, and ephemeral architecture of cloud-native applications, in which cloud workloads and databases can be spun up or shifted around within minutes, data is increasingly proliferated and dispersed. In addition, the multi-cloud architecture increasingly adopted by organizations today often results in a data mess. Terabytes of data can be replicated or instantly created by anyone, leaving companies struggling to know what data is stored in the cloud, whether any of it is of a sensitive nature, and where it is located, even as breaches increase and rules become more stringent.
Furthermore, manual data classification processes such as tagging are not only very expensive, require constant training, and are time-consuming, but they are also impossible to scale to the exponential growth of data types, sources, and regulations that characterize contemporary cloud environments. It can also lead to omissions, inconsistent tagging, or other human errors.
What’s needed is an automated way to continuously scan managed and unmanaged data stores across your cloud estate.
A Mix of Strategies to Restrict Access to Sensitive Data
The report also shows that we’re still in a transition period, moving from more legacy data security techniques to newer strategies.
When asked, “How do you restrict access to sensitive data?” we see a mix between old school (network access rules – 36%) and new school (IAM rules, CIEM and DSPM tools – 57%):
- 36% network access rules
- 35% IAM rules
- 12% CIEM tool
- 10% DSPM tool
- 7% we don’t restrict access
Perhaps those responses reflect the diversity of answers when questioned about the perceived risks to sensitive data in the cloud. Responding to the question, “What risk to your data is the most concerning?” 36% of the respondents are most concerned about system vulnerabilities and software supply chain exposures, another 29% are worried about excessive permissions or lack of good permissions hygiene, 21% responded that access misconfigurations worry them most, while just 14% listed shadow data as their top concern.
It’s important to emphasize that shadow data should not be ignored. From a security standpoint, data that is unknown, cannot be protected. It is important to acknowledge that, no matter how meticulous the IT policies are, every company will have shadow data. Unavoidably, this shadow data will in certain cases also contain data that is sensitive and should be protected as such.
Another way of interpreting the data here is that organizations are indeed looking for more holistic cloud security approaches that surface many different risk categories. Which brings us to potential solutions.
Cloud Security Solutions Need to Include DSPM Functionality
Looking at potential solutions, it’s clear that respondents expect their cloud security platform to provide DSPM capabilities.
When asked “Do you view cloud data security as an integral part of your overall cloud security management, meaning it should be integrated into cloud security platforms?” the vast majority of respondents answered affirmatively:
- 65% agree
- 10% somewhat agree
- 15% neutral
- 8% disagree
- 2% somewhat disagree
This is important, for two reasons. First is that organizations recognize that DSPM capabilities are needed as a strategy to protect sensitive data in the cloud. It’s also noteworthy that the question was about integrating these capabilities into a cloud security platform that goes beyond just the data itself. Tools that are focused solely on DSPM concentrate too much at the micro level, lacking the wider breadth of risk context that can impact sensitive data in the cloud, such as cloud misconfigurations, vulnerabilities, exposed APIs, lateral movement risk and other threats.
These siloed tools have significant gaps when it comes to securing critical data assets, lack the wider risk context that can impact sensitive data in the cloud, and represent yet another tool in an already crowded security stack, requiring resources and maintenance.
How Orca Protects Cloud-stored Sensitive Data
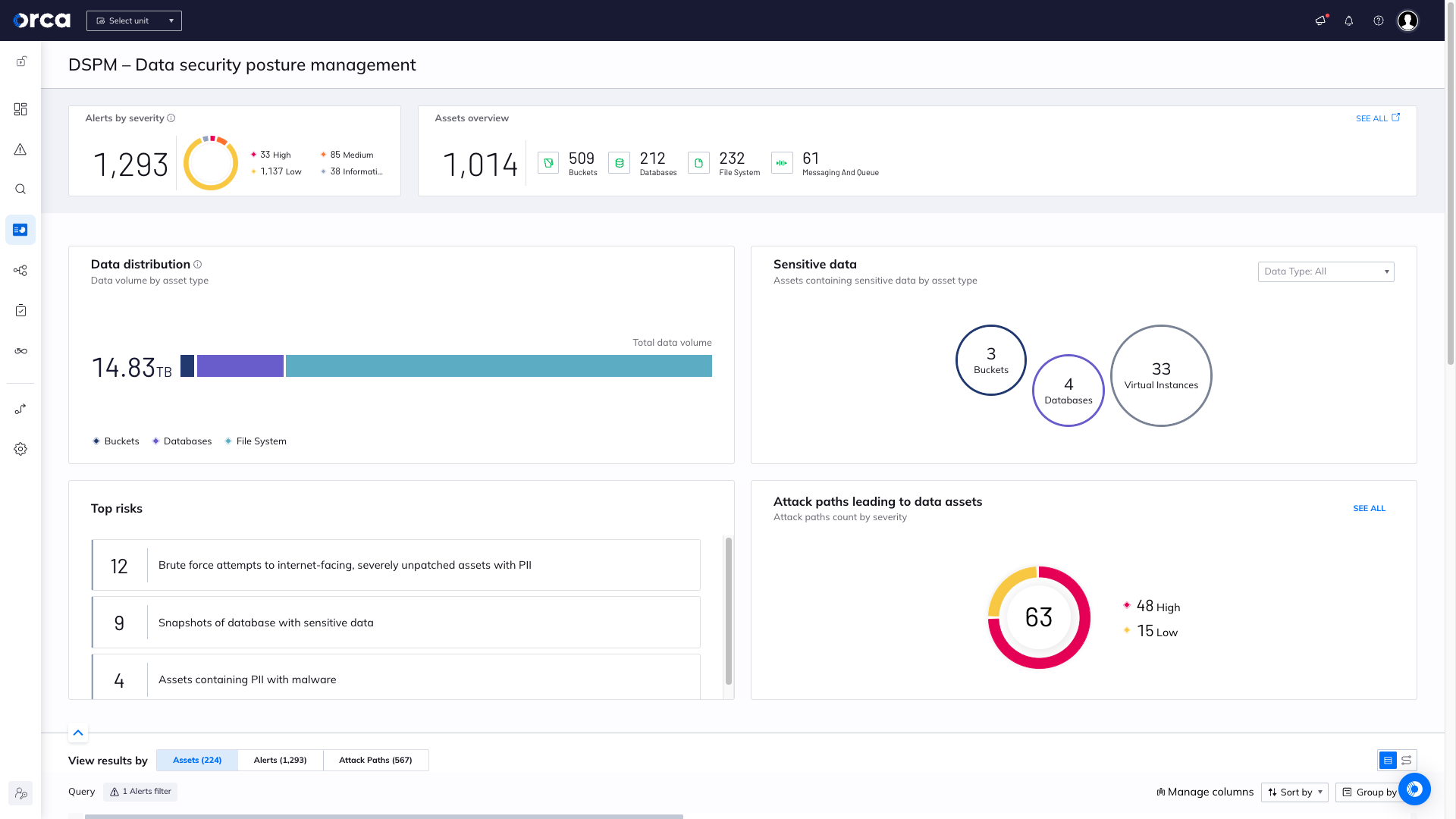
The Orca Cloud Security Platform includes a comprehensive offering of DSPM capabilities. As opposed to focusing solely on data security, Orca takes a much wider view and combines data intelligence with other cloud risks–including vulnerabilities, malware, misconfigurations, lateral movement risks, identity and access risks, and API risks–allowing Orca to highlight how indirect as well as direct risks can lead to exposed sensitive data.
Orca continuously detects sensitive data at risk in managed and unmanaged cloud data stores, as well as in files on virtual machines, containers and cloud storage buckets. These DSPM capabilities enable organizations to take preventive steps to reduce the data attack surface and triage anomalous data-related events across their cloud estates including AWS, Azure, Google Cloud, and Alibaba Cloud, from a single comprehensive cloud platform.
Learn More About Orca Security’s DSPM Capabilities
- Download the Techstrong PulseMeter Report.
- Read our eBook Top 5 Mistakes to Avoid When Managing Sensitive Data in the Cloud
- Read our comprehensive guide – What is Data Security Posture Management (DSPM)
Sign up for a Free Risk Assessment or Request a Demo to see how quickly and easily the Orca Cloud Security Platform can help you identify and address potential cloud data risks





