Table of contents
According to Gartner, more than 70% of organizations will depend on cloud-native computing for innovation by 2027, a near-five-fold increase in adoption since 2023. Organizations of all sizes are recognizing the benefits of cloud-native applications in terms of growth and competitive advantage. Meanwhile, they’re also discovering the need for cloud-native security, with the segment already experiencing the highest growth in the global security and risk management market.
As demand for cloud-native computing continues to increase sharply, so does the impact of its associated security risks. From vulnerabilities and misconfigurations, to sensitive data exposure and malware, cloud-native applications remain susceptible to a wide range of risks that can result in significant consequences.
In this in-depth guide, we dive deep into the topic of cloud-native security, revealing what it means, why it matters, how it works, and how you can leverage it in your organization.
Cloud-native security defined
Cloud-native security is a collection of strategies and solutions designed to secure cloud-native applications and infrastructure developed and deployed in the cloud. It encompasses all phases of the application lifecycle—from development to runtime—and involves multiple functional teams, including security, DevOps, and development.
What areas does cloud-native security cover?
Below are the primary areas that cloud-native security monitors and secures.
Software development lifecycle (SDLC)
The software development lifecycle (SDLC) encompasses everything needed to bring an application to life. This includes multiple stages, such as planning, development, building, testing, deployment, and maintenance; components such as code, container images, IaC artifacts, libraries, dependencies, open source projects; and tools such as source code management systems, repositories, security and monitoring solutions, etc. The SDLC also involves multiple teams and practices in software development.
Cloud-native security introduces measures to catch issues early stages of the SDLC and helps prevent risks from getting deployed to production environments.
Container images
A container image is a template for creating a containerized environment, containing everything needed to run an cloud-native application. Developers use a single container image to quickly and easily create multiple containers. When an image contains a vulnerability or malware, it reproduces the risk in every container generated from the image—often resulting in hundreds or thousands of runtime risks.
Cloud-native security solutions secure container images by applying a variety of hardening techniques, such as disabling unnecessary services, removing unnecessary packages, signing images, securely storing signing keys, and more.
IaC artifacts
Infrastructure-as-Code (IaC) is an important technology that enables organizations to quickly and repeatedly provision cloud infrastructure through code. It also improves the security of applications by improving consistency, reducing errors, and reducing the need for manual configurations. Still, IaC artifacts can present significant security risks. Similar to container images, one mistake in an IaC artifact can quickly propagate into hundreds or thousands of misconfigurations when developers use the artifact for multiple projects.
Cloud-native security ensures IaC artifacts undergo a thorough validation and get scanned for vulnerabilities and misconfigurations. This ensures the protection and integrity of infrastructure code throughout its lifecycle.
Open-source components
Open-source components make up most of today’s applications, eliminating the need to create software components from scratch and offering developers a head start on their software projects. Despite these benefits, open-source components commonly contain security risks and licensing requirements that expose organizations to critical security risks.
Cloud-native security uses Software Composition Analysis (SCA) tools to identify and understand the open-source components used in their software projects. This includes detecting any vulnerabilities and risks, as well as any licensing requirements that may expose an organization to legal and regulatory consequences.
Kubernetes
Kubernetes, also known as K8s, is an open-source container orchestration platform for the management of containerized applications. Kubernetes plays a crucial role in many cloud-native applications, providing a flexible and scalable platform for running and managing applications in the cloud. While it provides substantial benefits, the orchestration platform is susceptible to a variety of security risks, such as misconfigurations, vulnerabilities, exposed secrets, and more.
According to Orca’s 2024 State of Cloud Security Report, 82% of organizations have a publicly-accessible Kubernetes API server. This critical exposure can allow attackers to modify resource states and potentially breach underlying infrastructure, containers, and more.
Cloud-native security solutions ensure the confidentiality, integrity, and availability of resources within the Kubernetes environment, protecting sensitive data, and preserving the overall integrity of the system.
Cloud workloads
A cloud workload is a collection of applications, resources, processes, and tasks needed to run a simple application to a complex service. It may include computing power, storage, applications themselves, networking, and data processing tasks. Still, workloads are vulnerable to a variety of risks, such as vulnerabilities, misconfigurations, malware, sensitive data exposure, and more.
Cloud-native security secures workloads running applications and storing data in the cloud, providing vulnerability scanning, malware detection, and data security management.
Cloud configurations
Under the Shared Responsibility Model, organizations must establish and maintain the proper configurations of cloud services offered by providers like AWS, Google Cloud, Azure, and others. Misconfigurations remain one of the most prevalent security risks, which explains why Gartner predicts that 60% of organizations will make cloud misconfigurations a top security priority by 2026.
Cloud-native security solutions detect and facilitate the remediation of cloud misconfigurations. This includes enforcing security policies, monitoring misconfigurations, auditing configurations across the cloud control plane, performing compliance checks, and more.
Cloud identities and entitlements
Cloud environments are highly dynamic, making it challenging to control an ever-growing number of identities and entitlements and their interrelationships. The complex and evolving nature of this ecosystem often leads to misconfigurations, excessive permissions, and more.
Cloud-native security enables organizations to effectively secure their cloud identities and entitlements, restricting access and permissions to what users need to perform their job (also known as the Principle of Least Privilege (PoLP)). These solutions provide scalable entitlements visibility, compliance assurance, cloud permission rightsizing, and automatic discovery and remediation of access risks.
AI systems
According to the Orca 2024 State of AI Security Report, 56% of organizations are using AI in cloud-native environments to build custom applications. This figure clearly shows that organizations are discovering the combined benefits of AI and cloud-native technology. Despite the advantages in terms of innovation, AI also presents key security risks in cloud-native applications and environments. For example, 62% of organizations have deployed an AI package with at least one CVE in their cloud-native environment.
What are the challenges of cloud-native security?
Many challenges contribute to the difficulty of cloud-native security. Below are some of the most common.
Dynamic and changing nature of cloud-native environments
As highlighted earlier, cloud environments are highly dynamic, not to mention the cloud-native applications that run on top of cloud infrastructure. This dynamism presents challenges for legacy security tools, point solutions, and poorly integrated cloud-native security platforms. It also can inhibit security teams’ visibility into cloud resources, resulting in overlooked security risks, an inability to prioritize existing security alerts, and significant consequences.
Coverage gaps
Complete coverage is a core challenge of cloud-native security, as most organizations utilize multiple cloud environments and often from more than one cloud service provider. This makes ensuring complete coverage difficult in terms of cloud-native security, as tools offered by cloud service providers only work with their specific platform and not across a multi-cloud environment involving other vendors.
Additionally, the rate and scale of container development makes monitoring difficult, with many containers being scheduled, deployed, and terminated. The more containers that get deployed, the more challenging it becomes to gain or maintain coverage of cloud-native infrastructure. Meanwhile, the distributed and dynamic nature of containerized workloads makes it challenging to collect data.
Ease of development
Cloud services prioritize ease of use and speed. This often comes at the expense of security, where developers can easily spin up new instances on demand, resulting in misconfigurations and other risks. According to the Orca Cloud Security Strategies Report, 57% of executives say misconfigurations are the top cloud security risk to their organization.
Alert fatigue
Security teams must contend with a deluge of security risks, which often leads to alert fatigue, anxiety, turnover, and critical risks going undetected. According to Cloud Security Alert Fatigue Report, 59% of security teams receive more than 500 cloud security alerts per day, and 55% report missing critical alerts on a daily or weekly basis.
A number of factors contribute to this problem. This includes the ease with which users can spin up new cloud resources that create security risks, the number of users creating and deploying cloud resources, the scarcity of security personnel and capacity, and the absence of cloud-native security solutions that can effectively prioritize risks.
Cross-functional friction
When security teams uncover a cloud-native risk, they must collaborate with developers to fix the source of the issue. Unfortunately, this often occurs at the most time-consuming, difficult, and tedious stage for developers: when risks are found in runtime. Legacy tools and poorly integrated cloud-native security platforms make the process cumbersome for developers, requiring them to learn and use new applications and divert focus from software development for extended periods.
As a result, developers often resent security teams and see them as impediments to productivity. This can make cross-functional collaboration less effective and limit the adoption of best practices that promote security.
What are important considerations in cloud-native security?
Cloud-native security is a unique field compared to other areas of security. The following concepts help distinguish it.
Shared Responsibility Model
The Shared Responsibility Model is an established agreement between cloud service providers and their customers that defines roles and responsibilities for cloud-native security. Generally, this model holds cloud providers responsible for protecting their cloud infrastructure, and organizations accountable for securing their applications at a minimum, along with their databases and/or operating systems depending on the arrangement. Three different arrangements exist under the Shared Responsibility Model (posing the most to the least responsibilities for the customer): IaaS, PaaS, and serverless.
The Shared Responsibility Model creates the need for cloud-native security and maintains its importance for organizations.
Complete visibility and coverage
Visibility remains a prerequisite of cloud-native security. Modern cloud-native security solutions focus on establishing full coverage and visibility through important innovations that distinguish them from legacy and traditional security solutions. This includes supporting public cloud environments across multiple providers and consolidating points solutions in one unified platform.
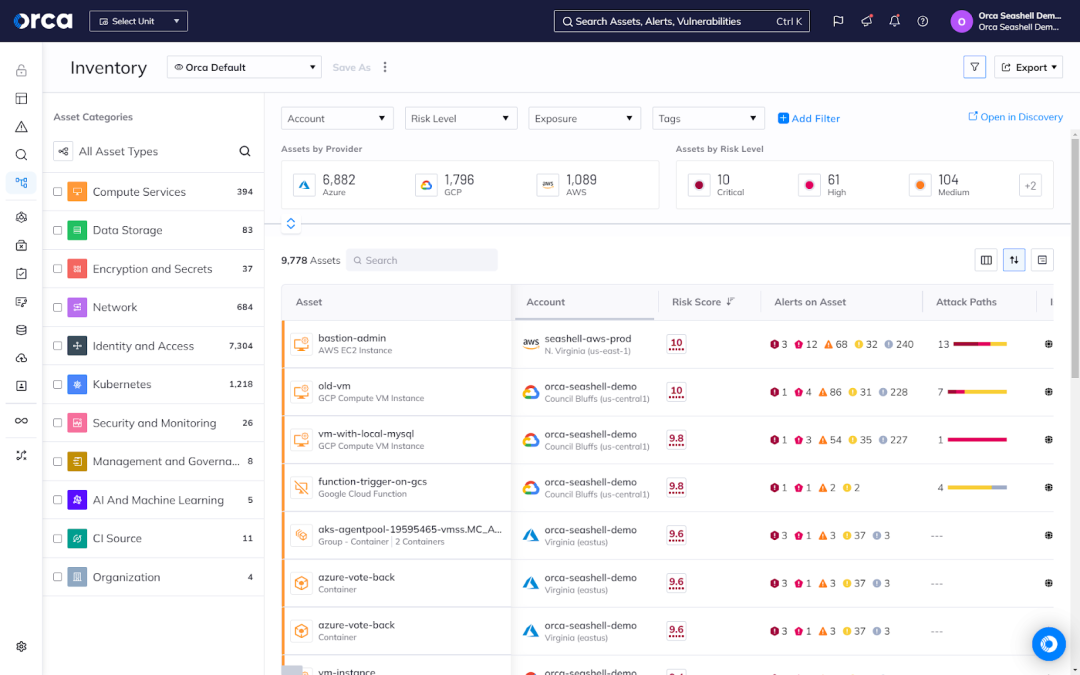
Comprehensive risk detection
Cloud-native environments are susceptible to multiple types of risks, including misconfigurations, vulnerabilities, malware, API risks, lateral movement risks, identity and entitlement risks, sensitive data exposure, and more. These risks often can interact, presenting major challenges for legacy tools unable to detect more than one type of risk or a limited set. Cloud-native security calls for comprehensive risk detection, a reason advanced solutions provide this capability.
Automation
Security teams often lack the time, resources, or capacity to address all the security risks detected in a cloud-native environment. While this may be acceptable for certain risks, it can result in significant consequences for an organization. Security teams often take advantage of the automations and automated features offered by cloud-native security solutions. These cover a range of use cases and can complete routine tasks without human intervention. As a result, security teams can save time and add capacity, enabling them to focus on higher-value activities.
AI-driven features
AI technology continues to boost productivity across functions and lines of business, cloud-native security among them. Advanced cloud-native solutions leverage generative AI (GenAI) to automate and accelerate critical tasks, as well as lower the knowledge and skill thresholds needed for cloud-native security. AI-driven features cover multiple use cases, including cloud-native search, remediation, policy recommendations for identity and entitlements, and more.
For example, the Orca Cloud Security Platform offers AI-Driven Remediation to generate remediation code and instructions on demand and tailored to your unique remediation solution and process. It also offers AI-Driven search to enable users to ask any question in plain language about their cloud-native environment, resources, or risks, and get immediate answers. The feature supports queries in more than 50 different languages, making security accessible to global teams regardless of location.
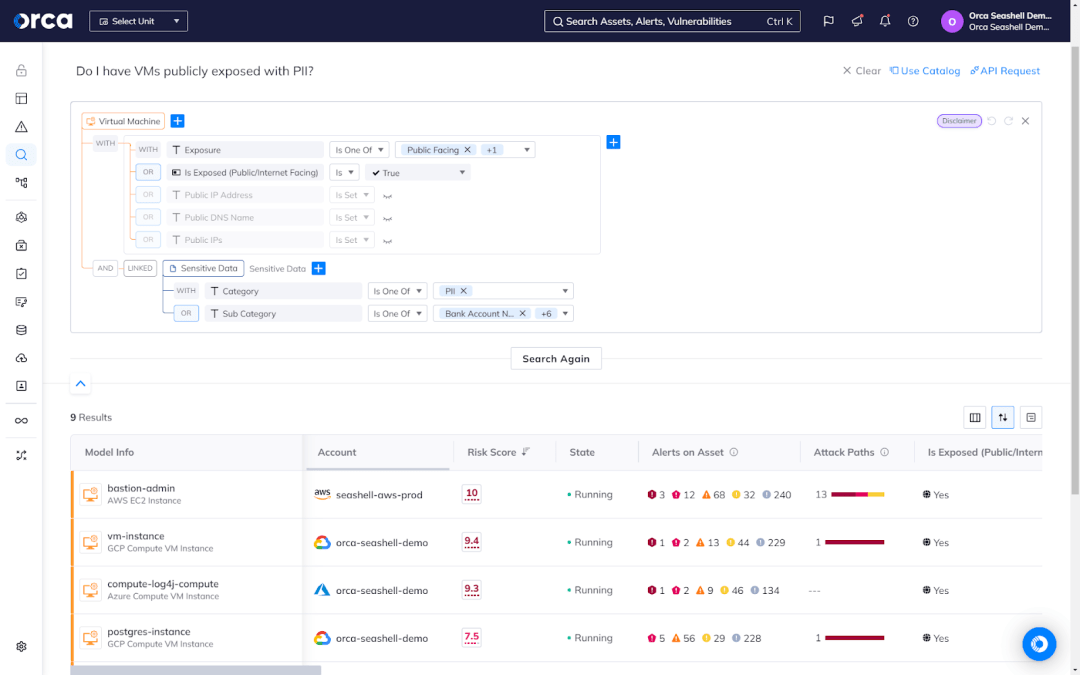
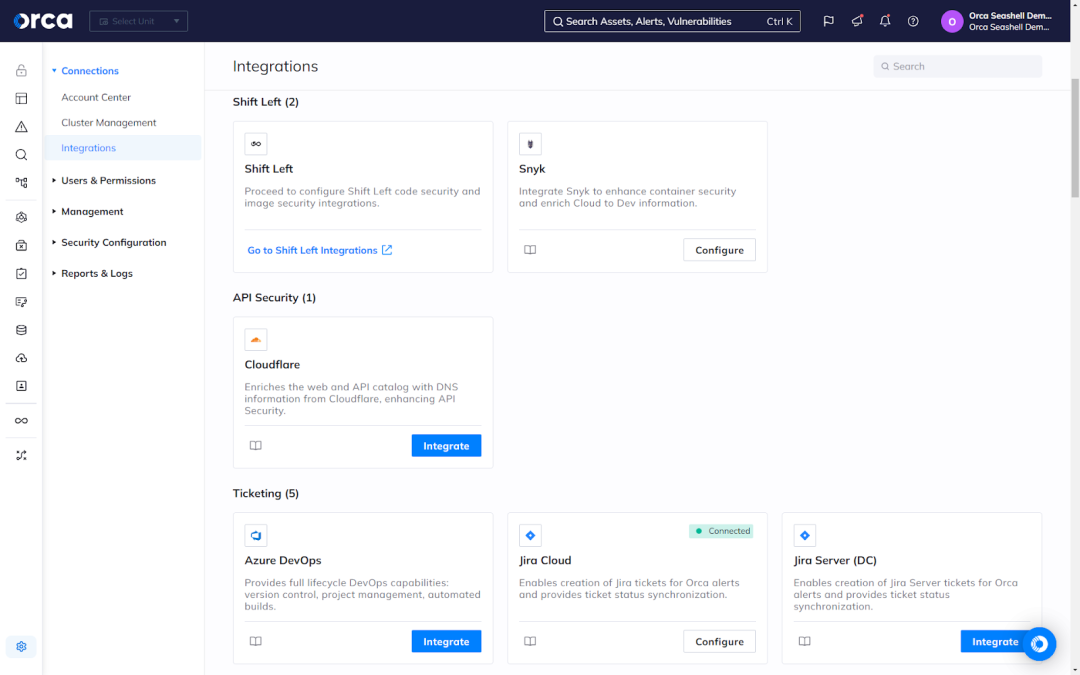
Integration with existing tech stack
Cloud-native security solutions offer a number of integrations to promote cross-functional collaboration and the adoption of security practices. While these integrations address a number of use cases, they often concentrate on the relationship between security, DevOps, and development teams, as these groups address cloud-native risks collectively and tend to experience frustration resulting from disparate tools and processes.
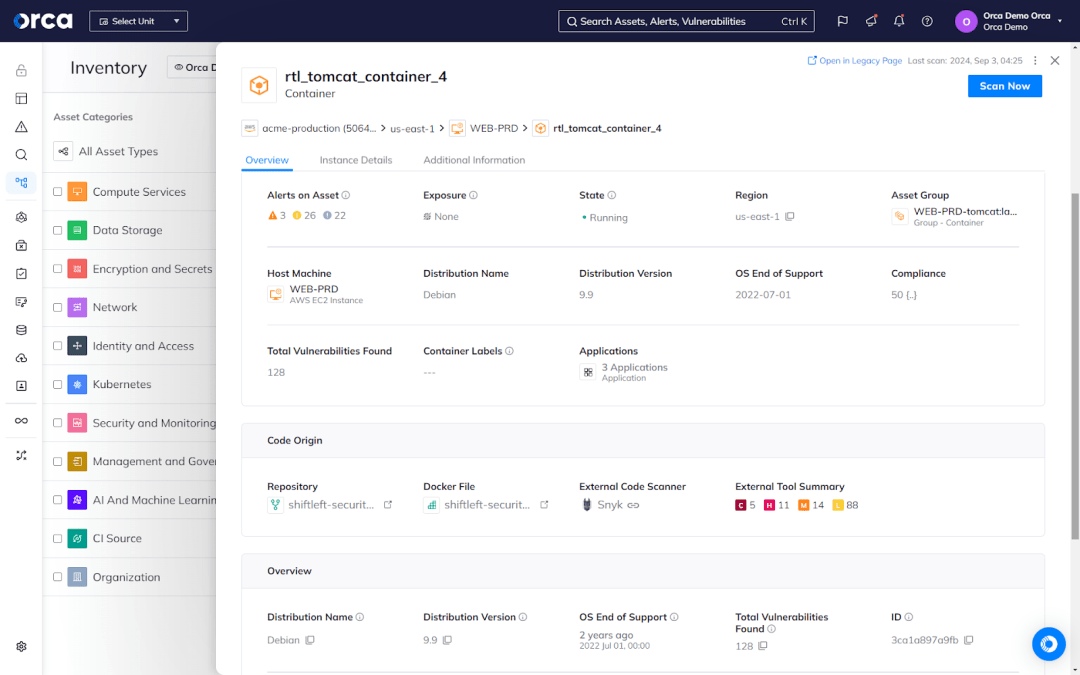
Cloud-to-development capabilities
When it comes to cloud-native security, security teams need the ability to trace runtime risks to their code origins, so they can effectively address issues at their source. As mentioned earlier, a single flawed container image or IaC artifact can easily result in hundreds or thousands of cloud risks. Cloud-to-development capabilities facilitate this tracing of risks from cloud to development environments, enabling security teams to immediately identify the development artifact at the root of a security risk, along with the associated code owner, contributor(s), source code repository, and more.
Cloud-to-development capabilities ensure security teams can quickly coordinate with developers to remediate existing risks and prevent future instances, while drastically reducing the Mean Time to Resolution (MTTR).
What solutions are used in cloud-native security?
Cloud-native security encompasses a wide range of solutions. Rather than using multiple disparate technologies, today organizations rely on Cloud-Native Application Protection Platforms (CNAPP), which provide comprehensive visibility and protection across cloud-native security use cases. CNAPPs consolidate the following technologies into one platform:
- Cloud Security Posture Management (CSPM): Secures cloud infrastructure by ensuring proper configurations, helping organizations limit risks and compliance issues.
- Cloud Workload Protection Platform (CWPP): Secures cloud workloads, detecting and helping remediate risks such as vulnerabilities, misconfigurations, and malware, to name a few.
- Cloud Infrastructure Entitlement Management (CIEM): Helps enforce the Principle of Least Privilege by managing access rights and permissions.
- Data Security Posture Management (DSPM): Detects sensitive data at risk in cloud resources and provides the tools and capabilities to secure it.
- Vulnerability Management: Detects and mitigates weaknesses in cloud-native infrastructure, applications, and services that attackers can leverage for malicious purposes.
- API Security: Discovers and secures APIs from exposure, misconfigurations, vulnerabilities, threats, and other risks.
- Cloud Detection and Response (CDR): Protects against in-progress attacks through detection of malicious or anomalous activity, continuous monitoring, and remediation.
- Container Security: Secures containers through scanning, continuous monitoring, network security, and other controls.
- Kubernetes Security Posture Management (KSPM): Ensures the security of Kubernetes deployments through secure cluster configurations, access controls, continuous monitoring, and other practices.
- Multi-Cloud Compliance: Enables organizations to manage their compliance initiatives across multi-cloud environments through continuous monitoring, tracking, alerting, remediation, and reporting.
- Shift Left Security: Secures software projects from development to deployment, enabling organizations to embrace DevSecOps and shift security left in the SDLC.
- AI Security Posture Management (AI-SPM): Protects your cloud-native AI innovation, covering AI services, models, packages, and data.
What are best practices in cloud-native security?
Organizations can take a number of different approaches to cloud-native security. The following best practices help produce the best results:
- Incorporate security early in the SDLC: Focus on preventing security risks by shifting security left in the SDLC. This involves adopting cloud-native solutions that support DevSecOps and promote seamless collaboration between security and development teams. It also calls for promoting security and prioritizing it across your organization.
- Operationalize security across different teams, workflows, and tools: Building on the previous practice, adopt cloud-native security tools that integrate effectively with the technologies and processes used by functional teams outside security. Development teams are the primary consideration here, as they present the greatest demands for seamless integration and the biggest impact on security outcomes.
- Leverage customizations and automated features: Advanced cloud-native security tools typically offer a number of customizations and automated features to suit the specific needs of your organization. From building custom alerts, to detecting specific issues of special concern, to developing automations that execute low-level tasks, utilizing these features can provide enormous benefits in terms of security, efficiency, and productivity. Best practice is to learn the features available from your cloud-native solution, carefully evaluate them, and use them immediately.
- Unify point solutions across the application lifecycle: Cloud-native security encompasses a wide range of use cases, point solutions, and risks. Best practice is to adopt a Cloud-Native Application Protection Platform (CNAPP). CNAPPs provide a unified offering, simplifying and accelerating deployment, eliminating information silos and blind spots, enhancing usability, and enabling the analysis of risk holistically and contextually.
About the Orca Cloud Security Platform: a true CNAPP
The Orca Cloud Security Platform is an agentless-first solution designed to fully secure cloud-native applications and environments across their lifecycle. A true CNAPP built from the ground up, the Orca Platform combines full multi-cloud coverage and comprehensive risk detection to analyze risks holistically, contextually, and dynamically. This enables the Platform to effectively prioritize alerts as well as surface toxic risk combinations that endanger your high-value assets.
The Orca Platform also supports end-to-end cloud compliance, offering continuous monitoring, tracking, alerting, remediation, and reporting capabilities across more than 160 out-of-the-box frameworks and any custom built using the Orca Platform.
To see how the Orca Cloud Security Platform enhances cloud-native security and compliance, book a personalized demo with one of our experts.
Conclusion
Cloud-native computing represents both an opportunity and liability for organizations. On one hand, it creates the conditions for gaining or retaining a competitive advantage, while on the other, it exposes organizations to significant security risks that demand agility and action. Cloud-native security enables organizations to strike a balance between development and security, allowing them to optimize their innovation while doing so safely, securely, and sustainably.
FAQ
What are cloud-native security risks?
Several different types of risks affect cloud-native applications and environments. While not an exhaustive list, common risks include:
- Misconfigurations
- Vulnerabilities
- Malware
- Exposed sensitive data
- Identity and Access Management (IAM) risks
- AI risks
- API risks
What are common cloud-native security tools?
Organizations rely on a number of solutions for cloud-native security, which they leverage as part of a Cloud-Native Application Protection Platform (CNAPP). CNAPPs consolidate the following point solutions and unify them in one platform. They include:
- Cloud Security Posture Management (CSPM)
- Cloud Workload Protection Platform (CWPP)
- Cloud Infrastructure Entitlement Management (CIEM)
- Data Security Posture Management (Data Security Posture Management)
- Vulnerability Management
- API Security
- Container Security
- Kubernetes Security Posture Management (KSPM)
- Multi-Cloud Compliance
- Application Security Posture Management (ASPM)
- AI Security Posture Management (AI-SPM)
How does cloud-native security work?
Cloud-native security involves adopting a collection of tools and strategies designed to protect cloud-native applications throughout their lifecycle. This process calls for implementing measures that catch vulnerabilities and misconfigurations as applications are developed, comprehensive detection for runtime risks, effective risk prioritization, and fast and flexible remediation. Cloud-native security aims to neutralize all security risks before attackers can exploit them.







