Table of contents
- What is multi-cloud compliance?
- Key regulations and standards
- Challenges of multi-cloud compliance
- Core components of multi-cloud compliance
- Best practices for achieving multi-cloud compliance
- Multi-cloud compliance tools and solutions
- Common pitfalls in multi-cloud compliance and how to avoid them
- AI and the future of multi-cloud compliance
- Conclusion
- FAQs
Orca’s 2024 Cloud Security Strategies Report found that maintaining cloud compliance is among the top three objectives of enterprise executives. The study also found that more than nine in 10 respondents in the study utilized two or more cloud environments.
These results shouldn’t come as a surprise. Failing to comply with government or industry regulations can result in hefty financial, regulatory, reputational, and legal consequences. It’s also more challenging than ever before with the rise of cloud computing. Organizations must now monitor, secure, and report on digital infrastructures that rapidly and continually change.
Fortunately, advanced solutions have forged a sustainable path for organizations to achieve and sustain compliance—especially in the age of multi-cloud computing.
In this guide, we answer the question, “what is multi-cloud compliance,” including what it entails, why it matters, and best practices for achieving it in your organization.
What is multi-cloud compliance?
Compliance is a collection of activities, solutions, and strategies focused on adhering to regulatory frameworks and industry standards governing the security, availability, and confidentiality of digital technologies. At its core, compliance determines an organization’s authority to operate and can result in significant penalties or disruptions to business continuity when not achieved or sustained successfully.
Compliance also requires:
- Adherence to a mandatory or voluntary framework managed by a regulatory authority or industry association.
- Tracking, documenting, and reporting on adherence at regular intervals.
- Undergoing validation by a third-party auditor or self-reporting method.
Multi-cloud compliance takes this base definition and extends it to an organization’s use of two or more public clouds (cloud environments owned and operated by cloud service providers such as AWS, Azure, and Google Cloud). In multi-cloud compliance, organizations tackle the previous activities using technology that helps streamline and automate the process.
With the pace of innovation continuing to accelerate, compliance is becoming more important and prominent than before. We can expect this trend to continue, especially with the emergence of AI technologies and security concerns that accompany them.
Key regulations and standards
Numerous compliance frameworks exist across the world, each tailored to specific regions, industries, or business lines. Below are several key regulations many organizations must comply with.
Digital Operational Resilience Act (DORA)
The Digital Operational Resilience Act (DORA) is a regulatory framework that applies to all financial institutions operating in the EU, as well as some third-party information and communication technology (ICT) vendors, including cloud service providers (CSPs). DORA consists of five core sections, known as “pillars of action.” Established in January 2023, the regulation goes into effect January 17th, 2025.
FedRAMP
FedRAMP, the Federal Risk and Authorization Management Program, was established by the US government in 2011 to set standards for the authorization, security assessment, and continuous monitoring of cloud products and services. This program aims to help the federal government take advantage of cloud technology while ensuring the highest-level of security and data protection.
General Data Protection Regulation (GDPR)
Enacted by the European Union (EU), the General Data Protection Regulation (GDPR) is a regulation designed to protect the security and privacy of personal data for individuals within the EU. GDPR defines rules for any organization collecting, processing, or otherwise handling this information and enforces strict penalties for non-compliance.
Health Insurance Portability and Accountability Act (HIPAA)
Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, establishes standards to safeguard the privacy of protected health information (PHI). HIPAA applies to any organization that stores, processes, handles, or manages PHI in the United States.
International Organization for Standardization (ISO) 27001
ISO 27001 is an international standard for managing the risk of information systems across 14 domains. A voluntary framework, some countries, industries, and companies require organizations to meet ISO 27001 requirements before doing business. ISO 27001 is especially relevant for organizations that collect, process, or manage sensitive information.
National Institute of Standards and Technology (NIST) Special Publication 800-53
NIST SP 800-53 is a set of standards focused on strengthening the privacy and security of information systems used within the federal government. Federal agencies and contractors use NIST 800-53 to meet the requirements set by the Federal Information Security Management Act (FISMA).
NCSC Cyber Assessment Framework (CAF)
The NCSC Cyber Assessment Framework (CAF) Is a sector-agnostic framework that assesses the cyber security resilience of organizations in several essential areas. Unlike other regulatory frameworks, CAF provides general guidance for achieving outcomes that support cyber security resilience and doesn’t prescribe rules or activities. CAF is designed to help UK organizations meet the requirements of the NIS Directive and support critical national infrastructure (CNI) needs.
NIS2 Directive
The NIS2 Directive is a comprehensive framework designed to strengthen cybersecurity in the EU and across its Member States. NIS2 requires organizations deemed Essential or Important to comply with its requirements, which it determines based on an entity’s importance to society and the impact a business disruption would cause. NIS2 requires Essential entities to undergo proactive oversight, while Important entities are subject to monitoring only after an incident of non-compliance is reported. Like the General Data Protection Regulation (GDPR), the NIS2 poses stiff fines for non-compliance by covered entities.
The Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) is a comprehensive, mandatory set of security guidelines that organizations handling credit card transactions must follow to protect cardholder information and prevent fraud. Regardless of their size, this applies to all businesses that either store, process, or transmit cardholder information, or sensitive data used for authentication purposes.
Service and Organization Controls 2 (SOC 2)
SOC 2 is a compliance framework used by service organizations to validate their ability to safeguard customer data. The framework evaluates internal controls for security, availability, confidentiality, privacy, and processing integrity. Service providers must identify the internal controls that warrant validation, which a licensed CPA firm audits and reports on.
StateRAMP
StateRAMP, or the State Risk and Authorization Management Program, is a voluntary cybersecurity assessment framework designed for use by state and government agencies to evaluate the security of cloud service offerings (CSOs). It requires service providers chosen by the government to show adherence to NIST 800-53 standards and other security controls before they can offer their services to state, local, and education (SLED) agencies.
How these regulations apply to cloud environments
Each regulation explored in the previous section includes standards that pertain to cloud environments. Generally, they require organizations to implement, monitor, test, and manage controls that ensure the security and privacy of cloud infrastructure and assets. This includes controls that perform the following functions, to name few:
- Restrict unauthorized access.
- Secure sensitive data through encryption and other measures.
- Protect systems from malicious software.
- Test security systems regularly.
- Limit access and privileges for cloud resources and roles.
For example, PCI DSS requires organizations to restrict network access to and from environments storing cardholder data. To meet this requirement, organizations must properly configure these environments to allow only necessary traffic. The regulation considers an organization out of compliance if one of its virtual machines permits direct public access.
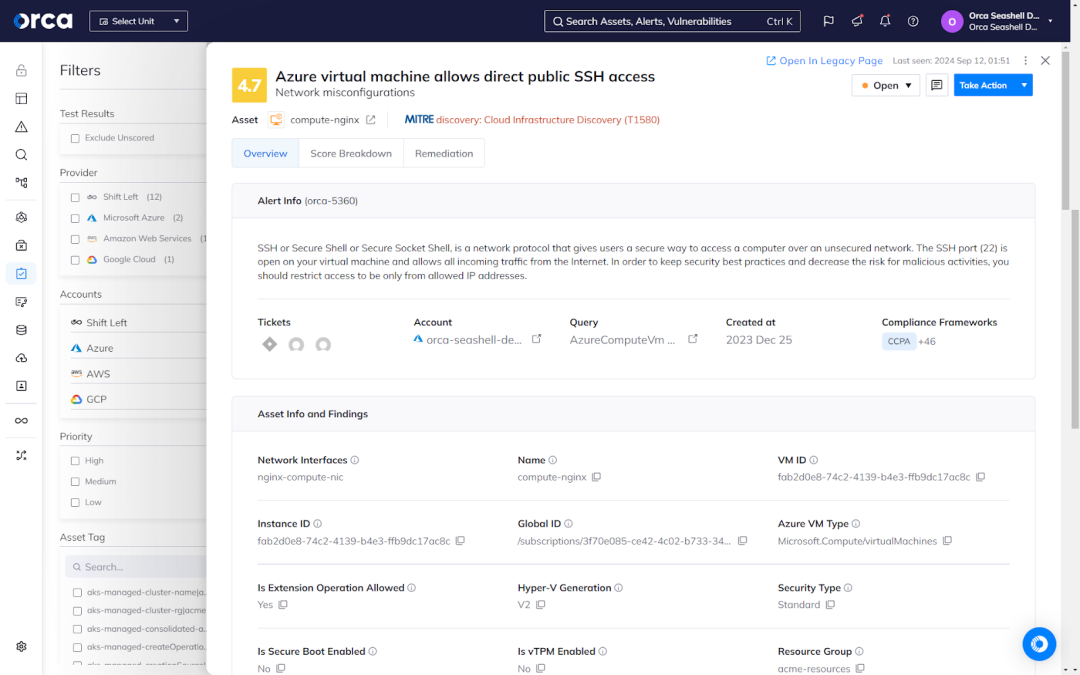
Challenges of multi-cloud compliance
Multi-cloud compliance only increases the difficulty of adhering to regulatory standards. Organizations tasked with achieving and sustaining it face the following challenges:
Visibility
Cloud environments are dynamic, with resources spinning up and turning down at a speed and frequency that demands the aid of technology. Still, due to technological constraints, organizations often can’t gain full visibility into their multi-cloud environments, making compliance unattainable. Several factors prevent full visibility into a cloud estate:
- Point solutions: Technology designed for specific use cases that is constrained by limited capability, visibility into a cloud environment, or both.
- Poorly integrated platforms: Technology that offers comprehensive capabilities but also limits visibility due to disparate interfaces, poor user experiences, and other barriers.
- Cloud-specific solutions: Technology that doesn’t support environments across multiple cloud providers. Typically, these solutions are offered by cloud providers.
Manual processes
Many organizations use a manual process for compliance that involves documenting and tracking adherence to security controls in spreadsheets. This approach is time and resource-intensive, not to mention highly ineffective.
As mentioned previously, cloud environments continually change on a daily basis, and the speed and frequency of these changes render manual documentation obsolete. Making matters worse, many organizations must comply with more than one regulatory framework or industry standard.
Organizations need the ability to access established frameworks digitally and automate key compliance tasks, including remediating security risks, implementing security measures, monitoring and reporting on compliance, and more.
Integration and delegation
Compliance often requires collaboration across multiple functional teams. Security practitioners often need to assign remediation tasks to developers. In reality, this type of collaboration results in duplicative and inefficient workflows, friction and frustration, and the forcing one or more of these teams to learn new tools and processes.
Reporting
Frameworks require organizations to formally report their compliance status at regular intervals, such as annually. This often becomes a time and resource-intensive task, requiring organizations to document the statuses of every control according to the format and guidelines prescribed by the regulator.
Here, technology can automate reporting, but many organizations run into trouble due to a lack of visibility into their multi-cloud environments (recall the first challenge in this section).
Core components of multi-cloud compliance
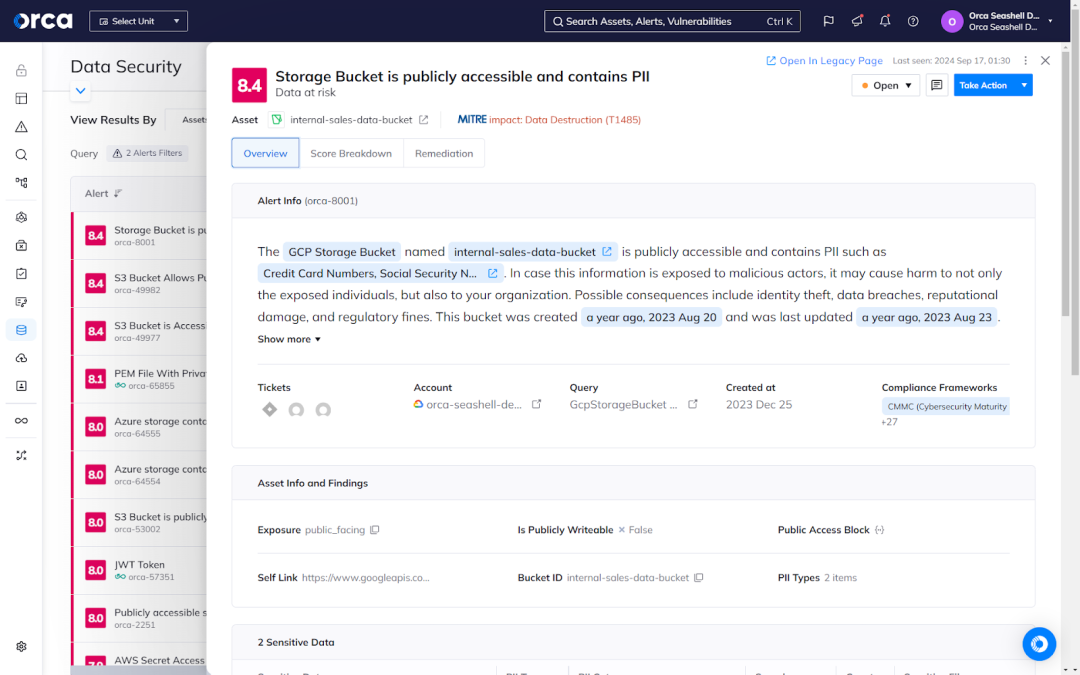
Data security and privacy
Data security and privacy is an important area of compliance included in all regulatory frameworks. It involves establishing the controls that ensure the safeguarding of sensitive information from unauthorized access, exfiltration, and other threats. This applies to the processing, storage, transmission of sensitive data.
It also calls for the following activities:
- Detect sensitive data exposure and remediate promptly.
- Encrypt sensitive data at rest and in transit.
- Educate developers and engineers on proper data security and privacy practices.
- Use secret stores for safe storage of encryption keys and secrets.
- Audit applications to ensure no sensitive information is logged.
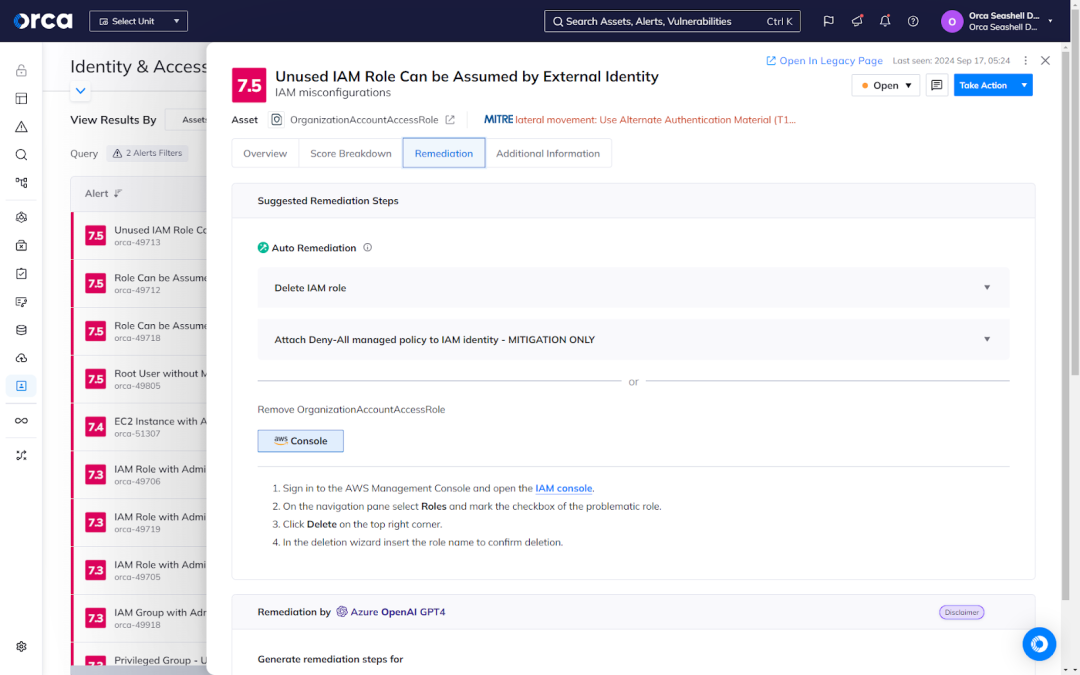
Identity and access management (IAM)
Identity and access management (IAM) focuses on controlling user access to digital resources and information. Like data security and privacy, IAM represents a core requirement of all regulatory frameworks, helping prevent unauthorized access and the security of cloud assets and data.
IAM involves the following activities:
- Ensure roles are properly defined and assigned to users.
- Ensure the permissions of those roles are limited to business necessity.
- Ensure proper security controls to limit lateral movement risk.
Full coverage across cloud environments
You can only protect what you can see. That’s why multi-cloud compliance demands full coverage—or protection that extends across your cloud estate, encompassing your infrastructure and workloads.
Full coverage requires agentless cloud security technology, as this eliminates the need to install an agent on every virtual machine and also prevents blindspots. Agentless technology works by collecting data and scanning environments through non-invasive methods. This includes collecting data—with read-only access—from your workloads’ runtime block storage and retrieving cloud configuration metadata via APIs.
For example, the Orca Cloud Security Platform leverages patented SideScanning™ Technology to see everything across a multi-cloud environment using the approach described above. The Orca Platform supports any combination of cloud environments from AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes.
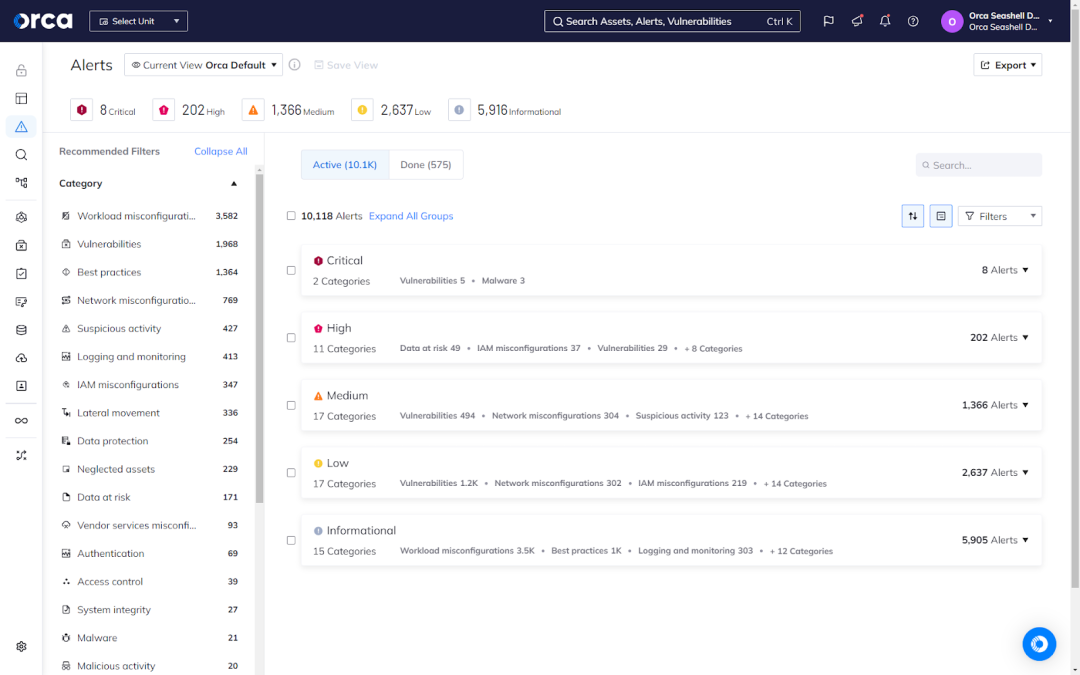
Comprehensive risk detection
Organizations must depend on solutions that automatically detect security risks and compliance issues. This need comes from the size of cloud environments, number of assets that they contain, and speed and frequency of changes within them.
Because numerous types of risks and issues exist, multi-cloud compliance calls for comprehensive risk detection. This means the ability to detect the following (though not an exhaustive list):
- Misconfigurations
- Vulnerabilities
- Malware
- Lateral movement
- API risks
- AI risk
- Sensitive data risk
- Identity and access management (IAM) risk
- Active breaches
Effective risk prioritization
According to Orca’s Cloud Security Alert Fatigue Report, 59% of security practitioners report receiving more than 500 alerts per day, a number well above what they can realistically address. In the same study, more than half of respondents said their organization frequently missed critical alerts.
This points to another critical component of multi-cloud compliance: risk prioritization. Organizations must prioritize the critical threats and compliance issues in their environments, and this should happen automatically via technology.
Effective risk prioritization calls for the following activities:
- Detect and present risks based on criticality, with priority given to the most critical.
- Assign a severity status to the risk that clearly indicates its severity.
- Dynamically and continually assess the severity of each risk using multiple factors.
The Orca Platform detects all types of risks and prioritizes them based on criticality. Orca also dynamically scores every detected risk using multiple criteria, including the severity of the risk (e.g., CVSS score), its likelihood of exploitation (e.g., EPSS score), as well as public exposure, presence of sensitive data, and other factors.
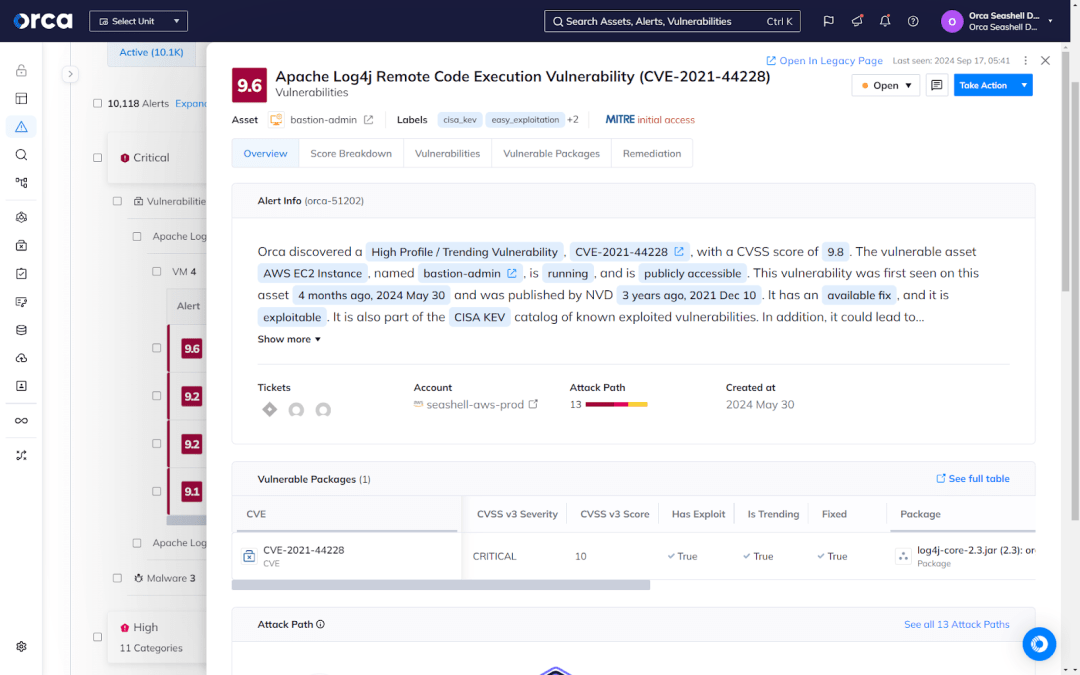
Automated tracking and reporting
Achieving compliance in the age of cloud computing calls for automation and digitalization. The rapidly changing and ephemeral nature of cloud environments render most tasks obsolete in terms of compliance monitoring, documentation, reporting, and more.
Organizations need multi-cloud compliance solutions that perform the following functions:
- Digitize compliance frameworks in a unified interface for managing all compliance-related tasks.
- Scan the entirety of cloud environments, generate alerts for areas of non-compliance, and map alerts to framework controls for fast diagnosis and remediation.
- Automate tasks that don’t require human intervention, such as auto-remediating certain IAM risks and generating notifications via third-party apps for cross-team collaboration.
- Customize ready-made frameworks to manage unique compliance requirements.
To illustrate, the Orca Platform offers more than 160 out-of-the-box compliance frameworks. Once a framework is selected, Orca automatically determines your compliance status with the chosen framework, based on the security risks and issues present in your multi-cloud environment. Orca also maps relevant alerts to each framework control, allowing for fast diagnosis and remediation.
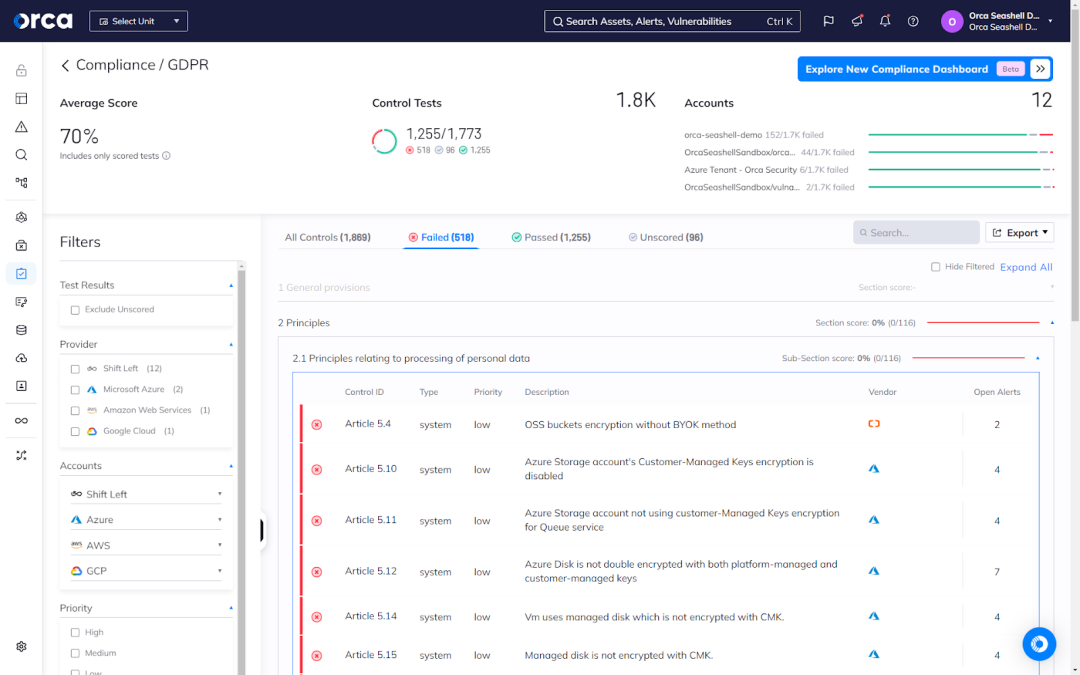
Orca also offers the ability to customize frameworks using any of its out-of-the-box frameworks or alerts from the Orca Alert library. This enables organizations to effectively achieve and sustain compliance, even when attempting to adhere to more than one framework.
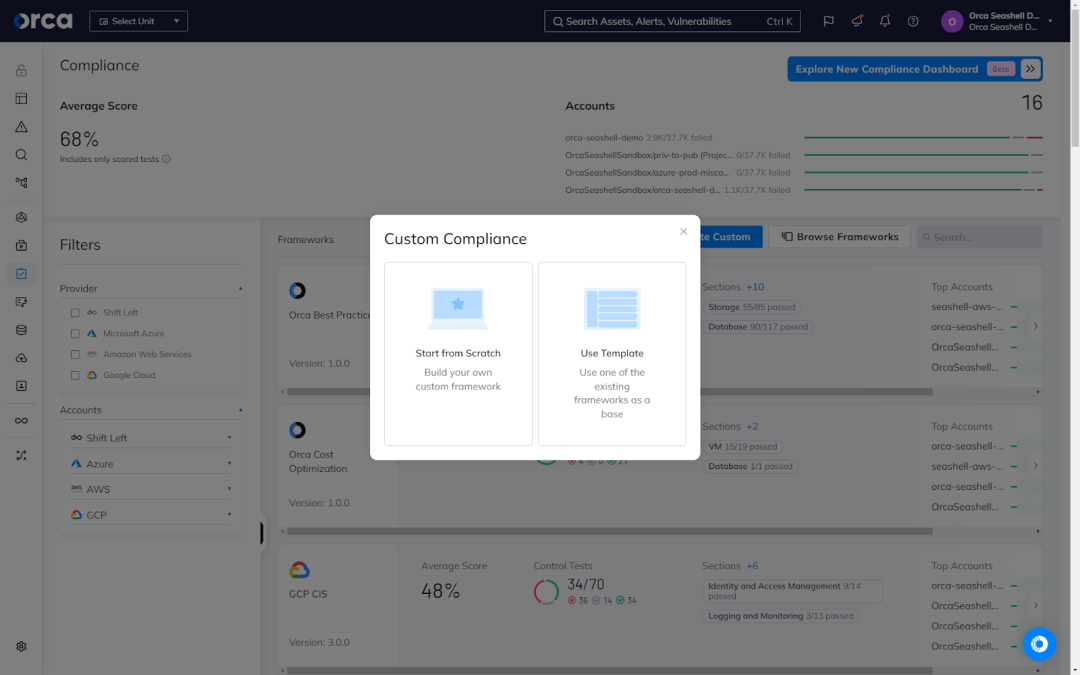
Best practices for achieving multi-cloud compliance
Achieving compliance calls for a unified strategy and intentional approach that extends across every department and function of your organization. Below are key best practices that can help your organization reach and sustain your compliance goals:
1. Make compliance a priority
Compliance is your authority to operate as a business. Considering the consequences of non-compliance—which include financial, legal, reputational, and regulatory ramifications—you should make compliance an ongoing priority for your organization. This requires a commitment from all levels of your organization, starting with executive leadership.
2. Verify vendor and partner compliance
Considering the dependencies in your digital supply chain, your compliance also depends on the compliance of your third-party vendors. That explains why regulations and industry standards require you to perform due diligence and provide proper disclosures on vendors.
For example, PCI DSS calls for performing a thorough review of a vendor’s data security and privacy practices before entering a partnership, as well as monitoring their compliance at least annually.
Importantly, your organization should invest the necessary time and resources for a thorough analysis of your vendors, including any legal issues, ethical practices, etc. Also, be sure to understand your compliance requirements when it comes to vetting third-party suppliers.
3. Leverage features for automation—from the start
Assuming your organization procures a multi-cloud compliance solution, best practice is to take advantage of features that can automate routine and repetitive compliance tasks. Most solutions offer some form of automation, and spending the time upfront to learn and adopt those features can result in significant time savings long-term. Best practice is to learn them and design workflows or processes that maximize their utilization and value.
4. Work toward continuous compliance
Many organizations make the mistake of treating compliance as an event. Preparation begins in the months leading up to an audit, resulting in stress, significant work, and the looming prospect of a compliance violation. After an audit, compliance becomes an afterthought, issues accumulate, and the cycle repeats itself.
In stark contrast, continuous compliance is when organizations make compliance a key aspect of their everyday operations. Once an organization becomes compliant, it focuses on staying compliant by actively addressing compliance issues as they surface. This approach eliminates the additional work and psychological costs that accompany compliance drift.
To achieve continuous compliance, make compliance an ongoing organizational priority, design workflows that support its ongoing sustainment, and leverage the automations of your multi-cloud compliance solution.
Multi-cloud compliance tools and solutions
1. Dedicated compliance solutions
Some organizations choose to adopt platforms dedicated to compliance. These solutions often provide continuous monitoring, support multiple compliance frameworks, and offer automations such as evidence collection and reporting. These solutions tend to offer limited visibility into the entirety of cloud environments, as well as the ability to detect all types of risks that affect compliance.
2. Cloud-Native Application Protection Platform (CNAPP)
Cloud-Native Application Protection Platforms (CNAPPs) unify a number of point solutions used for cloud security. With deep visibility and comprehensive risk detection, CNAPPs tend to serve as an effective compliance solution. Some offer advanced compliance capabilities, including out-of-the-box templates across most major regulations, the ability to customize frameworks, automations for compliance tasks, and automated reporting.
In terms of compliance, the effectiveness of CNAPPs as a compliance solution depends on the particular solution and vendor. For optimal results, your organization should opt for solutions proven to achieve results for a variety of organizations and compliance frameworks.
3. Case studies and real-world examples
Below are several examples of organizations that achieved multi-cloud compliance successfully:
- Cake, a startup that launched a banking app for European consumers, needed to comply with Europe’s Revised Payment Services Directive (PSD2). The company took a continuous approach to multi-cloud compliance and leveraged automated features of their cloud security platform.
- NGDATA, a global digital experience company, sought to improve security and meet its compliance requirements with the General Data Protection Regulation (GDPR). It implemented a cloud security solution to achieve both, finding value in the solution’s ability to simplify compliance monitoring, detect personally identifiable information (PII), and support the audit process.
Common pitfalls in multi-cloud compliance and how to avoid them
The list below includes some common pitfalls in multi-cloud compliance:
1. Overlooking data localization requirements
Organizations must meet the specific regulatory requirements of the countries or regions in which they collect data. This can prove challenging for companies with an expansive footprint because it calls for understanding and meeting the unique criteria of each regulatory jurisdiction.
Organizations should prioritize the effort to understand these requirements. They should also look for compliance solutions that not only make the effort feasible, but can allow them to sustain compliance as they expand into new markets. This represents a major advantage of using a CNAPP.
2. Allowing compliance drift
Compliance is an ongoing responsibility that continues for the life of any organization. Still, many organizations take an event-based approach to compliance, which we explored previously. This results in compliance drift and makes compliance more difficult, less efficient, and less effective leading up to the next audit.
Your organization should strive to sustain compliance after an audit. This makes the effort more manageable and effective, while less disruptive.
AI and the future of multi-cloud compliance
AI is rapidly transforming the multi-cloud compliance landscape. New regulations are emerging with many forming on the horizon. In 2024, the EU enacted the AI Act, the first comprehensive framework for regulating AI. The Act governs AI applications across the EU and presents stipulations based on their potential risk. It also bans applications found to pose an unacceptable level of risk.
Beyond new regulations, AI is also reshaping multi-cloud compliance in other ways, including asking more from existing solutions. These solutions must now offer AI Security Posture Management (AI-SPM) capabilities, which enable organizations to detect, remediate, monitor, and report on security risks in AI services, models, and packages.
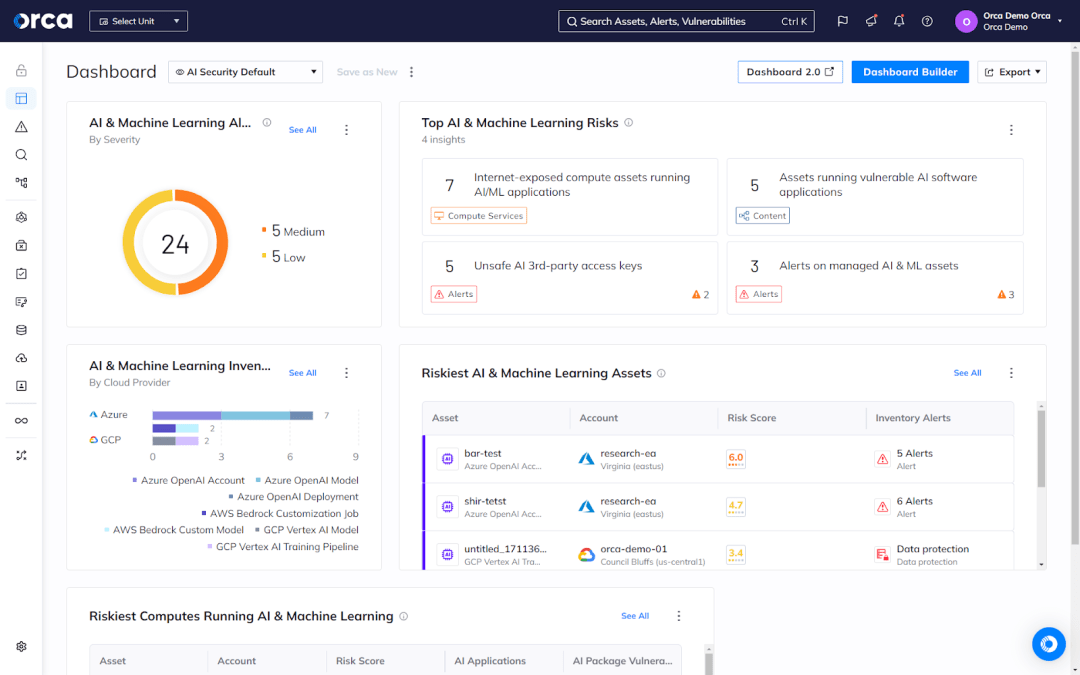
At the same time, AI is also empowering organizations to do more in terms of cloud compliance and cloud security—and with less. AI-driven features can make it easier and faster to remediate risks, understand the risks and resources across your entire cloud estate, and more.

Conclusion
Multi-cloud computing has fundamentally transformed the compliance landscape, increasing its importance while also making it more challenging to achieve and sustain. It also means organizations must become more technology-dependent. The cloud’s constantly evolving and ephemeral nature requires full and continuous visibility, substantive automation, and efficient features. Fortunately, cloud technologies also provide the answer to solving the challenges created by them.
Cloud security solutions like CNAPPs can help organizations not only achieve their compliance goals in the short-term, but reach a point of continuous compliance. As with any technology, it depends on choosing the right solution.
FAQs
What are multi-cloud compliance requirements?
A multi-cloud compliance requirement is a standard or control that ensures the security and privacy of digital information stored in two or more cloud environments. Each requirement governs a specific aspect or use case of multi-cloud computing and belongs to an organized framework maintained and enforced by a third-party organization or regulator. Multi-cloud compliance requirements can be mandatory or voluntary, as well as industry-specific or geographically determined.
What are some examples of multi-cloud compliance standards?
Numerous regulatory frameworks and industry standards apply to multi-cloud environments. Some of the most common include:
- Digital Operational Resilience Act (DORA)
- General Data Protection Regulation (GDPR)
- FedRAMP
- Health Information Portability and Accountability Act (HIPAA)
- International Organization for Standardization (ISO) 27001
- NCSC Cyber Assessment Framework (CAF)
- NIS2 Directive
- National Institute of Standards and Technology (NIST) Special Publication 800-53
- Payment Card Industry Data Security Standard (PCI DSS)
- Service and Organization Controls 2 (SOC 2)
- StateRAMP
What is the difference between multi-cloud compliance and governance?
Multi-cloud governance and compliance are similar concepts with different meanings. Multi-cloud governance refers to the ongoing practice of setting policies and standards that an organization will continuously monitor and track against, including those that are self-defined or stipulated by regulators and industry authorities. Multi-cloud compliance generally refers to the act of adhering to regulatory standards or industry regimes, though it may include internal policies as well.
Table of contents
- What is multi-cloud compliance?
- Key regulations and standards
- Challenges of multi-cloud compliance
- Core components of multi-cloud compliance
- Best practices for achieving multi-cloud compliance
- Multi-cloud compliance tools and solutions
- Common pitfalls in multi-cloud compliance and how to avoid them
- AI and the future of multi-cloud compliance
- Conclusion
- FAQs







