Table of contents
In today’s world, where everything is moving to the cloud, security is no longer just about protecting the network perimeter. With the rise of cloud computing, hackers are targeting user identities and access permissions. It’s an entirely new landscape, where “identity is the new perimeter.” This is where Cloud Infrastructure Entitlement Management (CIEM) comes in.
CIEM focuses on managing and protecting identities and privileges in cloud environments. Think of it as your cloud’s bodyguard, always making sure everyone has the right access and no one is sneaking around with a fake ID.
CIEM, which stands for Cloud Infrastructure Entitlement Management, is pronounced “Kim” to distinguish it from Security Information and Event Management (SIEM). CIEM detects identity misconfigurations and ensures the principle of least privilege (PoLP) in cloud environments. Implementing CIEM gives organizations and security teams better visibility and security for their cloud infrastructure.
Ultimately, CIEM helps you manage identities more effectively so you can secure your cloud estate more effectively and efficiently. Let’s dive into what CIEM is, why you need it, and how to implement it.
What is CIEM?
Cloud Infrastructure Entitlement Management (CIEM) is the practice of managing and securing access rights and permissions (often known as entitlements) within cloud environments. According to Gartner, CIEM offerings are “specialized identity-centric SaaS solutions focused on managing cloud access risk via administration-time controls for the governance of entitlements in hybrid and multi-cloud IaaS.”
Put simply, CIEMs define what actions a cloud identity can perform and what resources it can access within the data context. By effectively managing these entitlements, organizations can ensure compliance and reduce security risks.
The need for CIEM systems surfaced with the emergence of cloud computing. Identity and Access Management (IAM) systems, which were designed for fixed on-premise settings, couldn’t keep up with the dynamic nature of cloud services. This led to the introduction of CIEM which was designed for the cloud.
By effectively managing entitlements (permissions and access rights), CIEM empowers organizations to ensure compliance and minimize security risks. It acts as a bridge between existing IAM practices and the unique challenges of cloud security. While IAM provides the foundation, CIEM offers a more tailored approach specifically designed to enhance security in the ever-evolving cloud landscape.
Why you need CIEM
CIEM plays a pivotal role in securing cloud infrastructure and driving digital transformation. By effectively managing identities and access permissions at scale, the technology mitigates security risks and ensures compliance with regulatory requirements.
There are several reasons why you need to adopt CIEM as part of your cloud security. Below are the top three:
1. The sheer scale of cloud environments
In today’s expansive cloud environments, managing user identities and their access permissions manually is nearly impossible. The sheer volume of users, applications, and resources is simply too impractical to even think about. CIEM leverages automation and machine learning to provide comprehensive visibility into—and control over—who has access to what, across the entire cloud infrastructure.
2. Increased security risks in the cloud
Without CIEM, cloud environments face significant security risks from improper access controls, identity sprawl, and orphaned accounts. CIEM addresses these risks by enforcing least privilege principles and actively monitoring suspicious account activities, thereby reducing the risk of data breaches or other cyber threats.
3. The need to stay compliant
CIEM solutions provide powerful reporting and auditing features that are crucial for showing that organizations follow regulations such as GDPR, PCI DSS, SOC 2, ISO27001, HIPAA, and others. By tracking both user access and policy enforcement, CIEM helps businesses achieve multi-cloud compliance while confidently harnessing the transformative potential of the cloud.
How CIEM works
At its core, CIEM enables organizations to discover, manage, and monitor entitlements in real-time. It continuously scans and tracks identities present in the cloud environment, capturing information about their permissions and behavior. This allows for a holistic view of access privileges and potential risks associated with each identity.
Here is where policies and rules come into play:
- Policy definition: CIEM allows organizations to define security policies that dictate who can access what resources, under what conditions (like time of day or location), and for how long. These policies translate to specific access controls.
- Rule enforcement: CIEM enforces these access controls by continuously monitoring user activity and identifying anomalies or suspicious behaviors. This could include attempts to access unauthorized resources, unusual access patterns based on defined policies, or compromised accounts.
CIEM employs advanced algorithms and analytics to:
- Detect risks: It can identify potential security breaches based on deviations from established policies and rules.
- Generate alerts: When such risks are detected, CIEM generates alerts to notify administrators, enabling them to take immediate action and mitigate the threats.
- Prioritize alerts: Based on context, CIEM will score and order alerts so that security teams know which ones to focus on first.
- Calculate optimal policies: Based on usage history, a CIEM solution such as Orca can recommend and provide optimal policy configurations using AI.
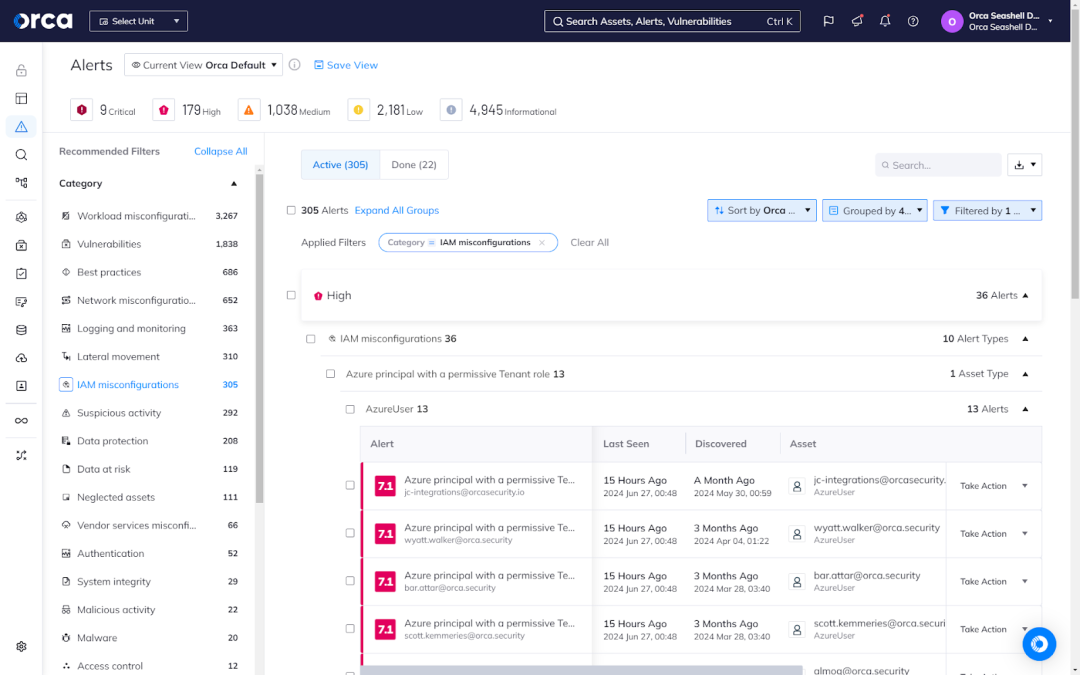
Additionally, CIEM plays a crucial role in enforcing least privilege policies. It ensures that each identity within the cloud environment has the appropriate level of access and permissions needed to perform their tasks effectively, without granting excessive privileges. By automatically adjusting entitlements based on established security guidelines, CIEM helps minimize the attack surface and reduce the risk of privilege abuse.
Benefits of CIEM
CIEM assists enterprises in achieving a strong cloud security posture by ensuring that identity and resource access are managed effectively across multiple cloud infrastructures. CIEM provides several key benefits, including:
1. Improved visibility and control over cloud resources
CIEM gives you better visibility into user permissions in your cloud estate. It helps identify accounts with excessive permissions as well as spot orphaned accounts. With this visibility, you can tighten access and implement the PoLP. With CIEM, organizations can also more effectively control access at scale across complex, multi-cloud environments.
For example, CIEM solutions offer a consolidated dashboard with full information on user entitlements, permissions, and access policies. This dashboard gives security teams a comprehensive view of the access landscape in their cloud environment. They can quickly detect any accounts with over-permissioned access rights and take suitable measures to mitigate the risk. Organizations with enhanced visibility and control may minimize the attack surface and improve their overall security posture.
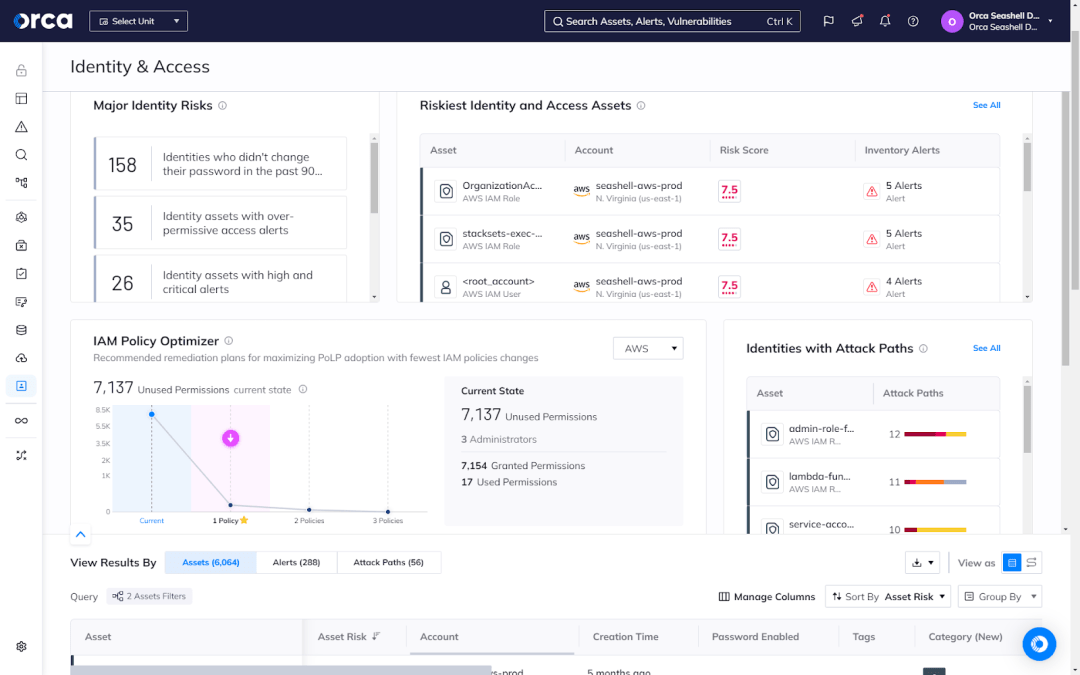
2. Enhanced security and compliance
CIEM plays a critical role in enhancing security and compliance in cloud environments. By managing identities and access in the cloud, CIEM helps address vulnerabilities arising from weak account permissions and excessive entitlements. This reduces the risk of data breaches and compromised accounts.
For example, CIEM solutions allow organizations to enforce the principle of least privilege by granting users only the permissions they need to complete their tasks. Organizations can mitigate the potential damage caused by a hacked account by implementing least-privileged access. CIEM solutions can assist firms in managing access to sensitive data and cloud resources, ensuring compliance with industry norms and standards.
CIEM solutions help firms comply with various regulatory obligations by implementing automated guardrails and enforcing consistent regulations. This streamlines the auditing process and guarantees they remain ready to demonstrate their compliance with standards.
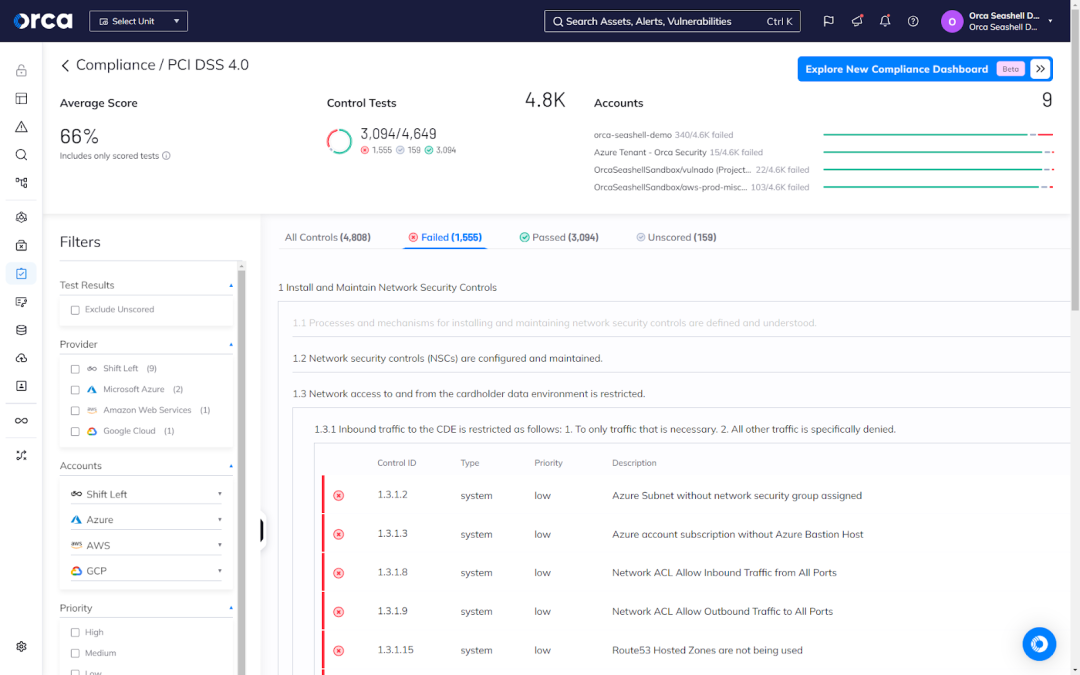
3. Scalability and flexibility in managing complex cloud environments
CIEM is built for the challenges of cloud infrastructure. It handles the scale and dynamics of cloud environments, where new resources are provisioned on demand. CIEM solutions are flexible enough to work with any cloud provider and can be tailored to your organization’s needs. They also help manage access at scale so you can free up resources and capacity to focus on other business priorities.
For example, CIEM systems can effortlessly integrate with cloud service providers to automatically discover and present a consolidated picture of access controls and permissions. This enables organizations to manage access to their whole cloud infrastructure through a single interface.
CIEM solutions also automate the process of provisioning and de-provisioning access. This scalability allows organizations to manage access more efficiently as their cloud environments expand and evolve.
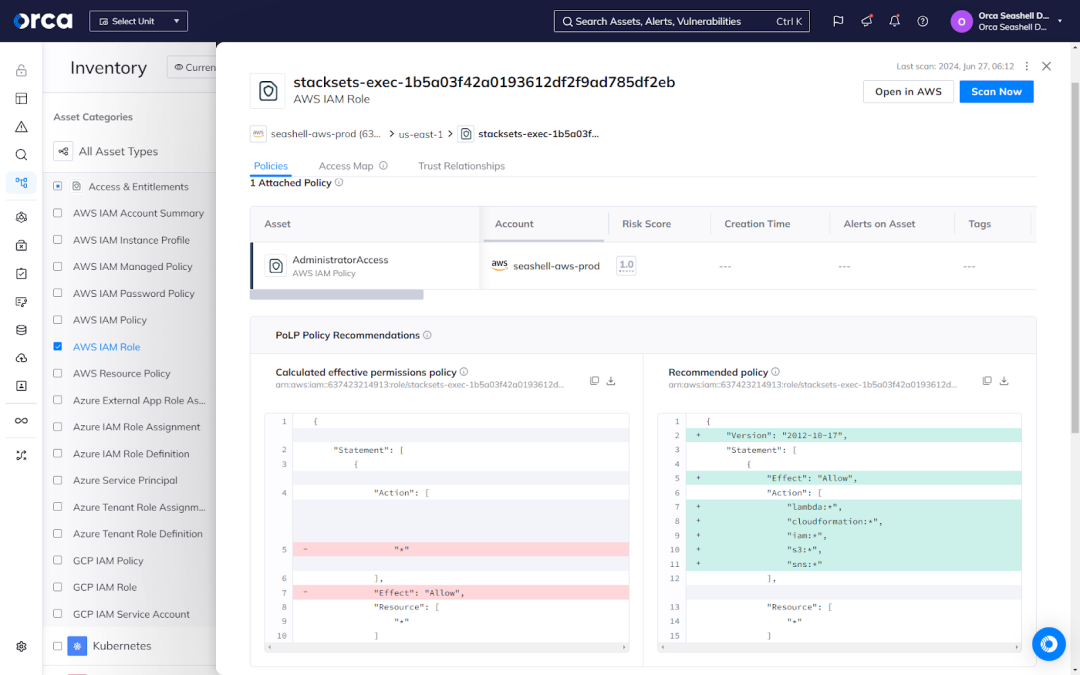
4. Rightsizing cloud permissions
CIEM tools help organizations improve identity and access management by continuously monitoring access activity and rightsizing permissions. CIEM accomplishes this by continually analyzing access patterns and entitlement usage.
For example, CIEM solutions can make recommendations on how to alter permissions so that people have the necessary access to complete their tasks without exposing critical resources. This, in turn, allows organizations to improve their security posture and reduce the dangers associated with excessive access rights by rightsizing cloud permissions.
5. Automated detection and remediation
CIEM systems leverage automation and advanced analytics to detect and handle possible security threats in real-time. By monitoring access patterns, CIEM solutions can detect irregularities and potential dangers such as insider threats, compromised accounts, and unwanted access.
For example, CIEM solutions can detect an account attempting to access resources outside of its usual behavior. When identifying anomalous activity, CIEM solutions can generate automatic alerts or take corrective action, such as canceling access or requesting extra verification.
Through automated detection and remediation, CIEM solutions help augment the capacity and productivity of busy security teams, alleviating any talent or skill shortages. CIEM solutions also speed up response times to security risks and events, decreasing the likelihood or severity of adverse outcomes.
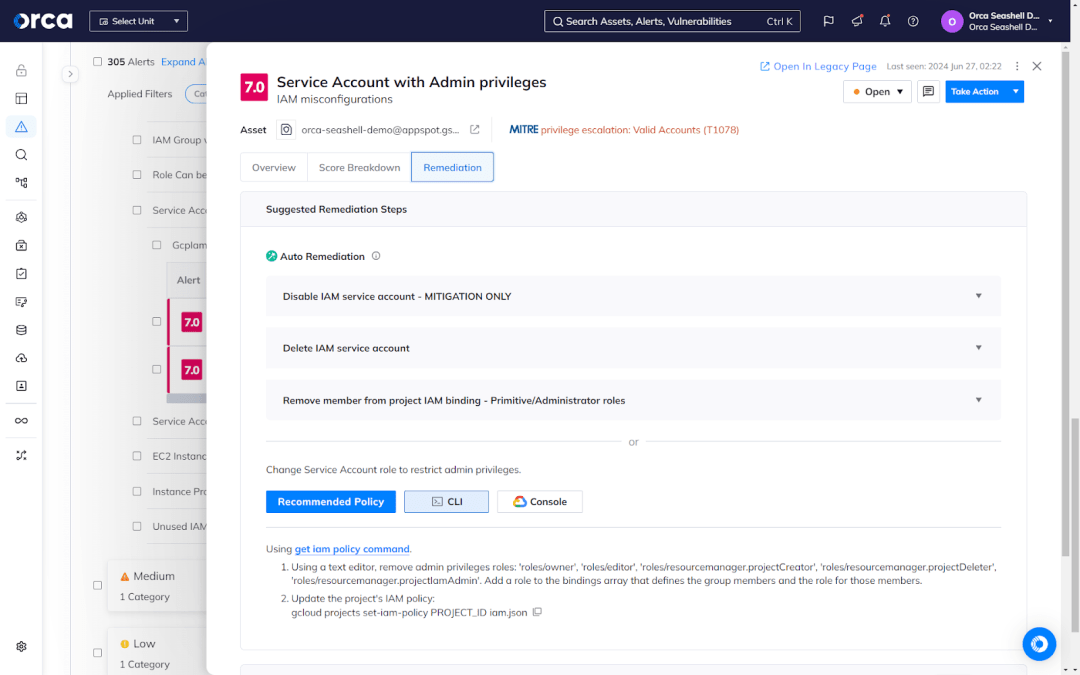
How to implement CIEM
To fully reap the benefits of CIEM solutions discussed above, you must find the right technology. The following steps and considerations can help you choose and implement the best CIEM solution for your organization.
1. Choose a CIEM solution. With many options available, selecting the right CIEM tool is key. Consider your existing security stack and compliance requirements. Look for solutions that provide full coverage of your entire cloud estate, comprehensive risk detection, extensive integrations, and comprehensive compliance capabilities. You should also favor CIEM tools that leverage AI and automation to accelerate critical tasks for your teams.
2. Implement policies and rules. CIEM relies on policies and rules to control access and entitlements. Determine what policies you need based on your risk assessment and compliance needs. Start with basic policies around least privilege and separation of duties before expanding to more complex rules.
3. Integrate with identity systems. Integrating your CIEM solution with existing identity and access systems is essential for a holistic view of permissions. Look for a CIEM tool that can connect to your cloud service providers, SIEM, and identity directories like Active Directory. This integration helps CIEM tools automatically discover and monitor entitlements.
4. Monitor and review. Continuously monitoring your CIEM solution is key to maintaining strong security. Review reports and logs regularly to detect issues early. Make adjustments to policies and rules as needed based on changes in your environment or compliance requirements. Conduct periodic audits of entitlements and access to ensure PoLP.
How to choose the right CIEM solution?
When it comes to selecting the ideal CIEM solution for your business or organization, it’s important to make an informed decision. The following considerations can help you choose the right CIEM solution.
- Comprehensive identity discovery: Look for a CIEM solution that automatically discovers, identifies, and presents all identities present in your cloud environments.
- Effective permissions management: Ensure the solution provides a complete and comprehensive diagnosis of the abilities and permissions associated with each identity, even across multiple accounts.
- Visual representation: The best CIEM tools include an identity graph or analytics feature that provides a visual representation of your identities and entitlements, enabling you to more easily comprehend and interpret them.
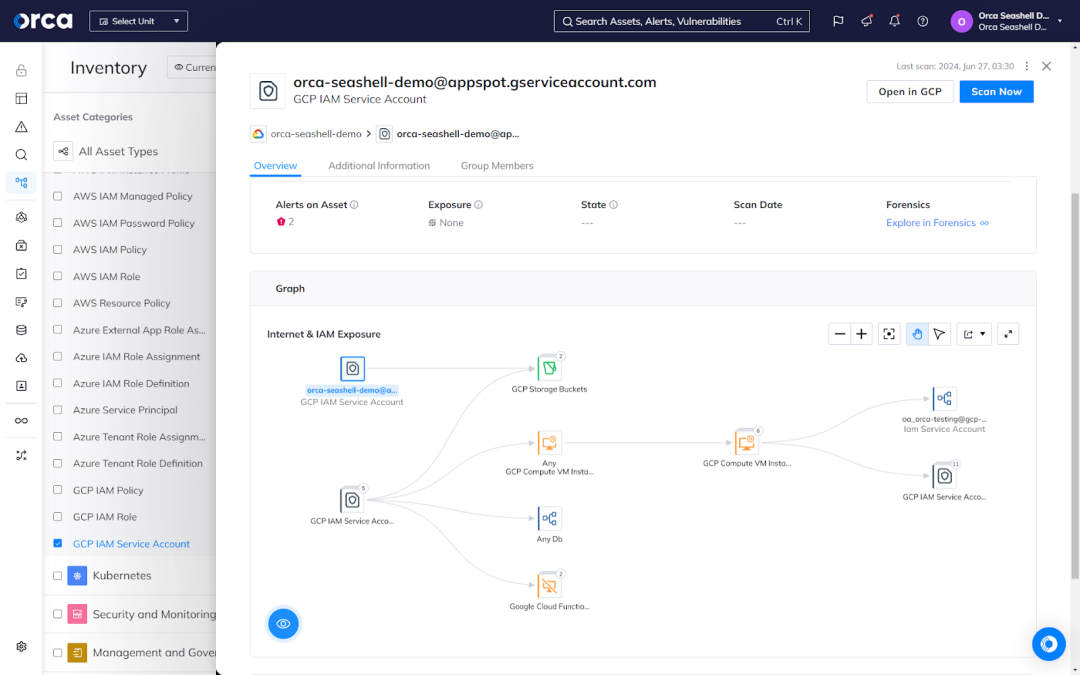
- Detection capabilities: Favor solutions that provide universal, granular, and continual monitoring capabilities. This enables you to detect anomalous, suspicious, and unauthorized activity that may signal a potential threat.
- Customizability: Opt for solutions that allow you to tailor features and functionality to your specific needs. From compliance efforts, to critical CIEM tasks, to remediation and mitigation activities, look for solutions that automate and accelerate workflows for your teams.
- Seamless integration: Choose solutions that fully integrate with your security stack, as well as common productivity and communication tools. Consider compatibility with your existing infrastructure, cloud platforms, identity providers, and other security tools to ensure smooth integration and interoperability.
By carefully evaluating CIEM solutions based on these factors, you can make an informed decision that aligns with your organization’s unique needs.
Why CIEM is not enough
CIEM is great at handling cloud identities and access, but Gartner says it shouldn’t be your only defense. Their Innovation Insight: Cloud Infrastructure Entitlement Management report points out an interesting trend:
“CIEM capabilities are increasingly being embedded in cloud security posture management (CSPM) and converged cloud-native application protection platforms (CNAPP), given the similar graph-based approaches used for scanning for misconfigurations and anomalies.”
Gartner, Innovation Insight: Cloud Infrastructure Entitlement Management, Henrique Teixeira, Abhyuday Data, and Michael Kelley, 11 May, 2023.
As cloud security evolves, organizations are moving away from siloed CIEM solutions and opting for more unified and advanced alternatives. This raises an important question, Do CIEM solutions provide adequate protection? To answer it, below we present the key limitations of the technology:
1. Limited scope
CIEM focuses mostly on one category of risks: those pertaining to identities and rights. It doesn’t address other significant security issues, such as cloud workload vulnerabilities, cloud service misconfigurations, or container image security.
Consider the following scenario: a user with excessive rights mistakenly launches a cloud instance that includes a publicly-available storage bucket. This misconfiguration would go undetected by CIEM since it doesn’t analyze the security posture of the cloud instance.
2. Siloed approach
Traditional security solutions are commonly disparate or siloed. While CIEM tools can provide useful insights into access controls, they may not integrate with a Cloud Workload Protection Platform (CWPP), which protects workloads from viruses and exploits.
For example, CIEM may detect a user with access to a sensitive database. However, it would not necessarily interact with a CWPP to see whether any malware is attempting to steal data from that database.
3. Limited threat detection
While CIEM solutions excel at detecting questionable identity activities, they may be unable to detect complex attacks that combine compromised credentials with weaknesses in cloud workloads.
For example, an attacker could acquire access to a low-privilege account with restricted rights. They might then use a cloud service vulnerability to escalate their privileges and gain access to sensitive information.
CIEM may fail to detect this advanced assault since it focuses on identity irregularities rather than cloud vulnerabilities. Some sophisticated CNAPP platforms, such as the Orca Cloud Security Platform, go beyond CIEM by incorporating Cloud Security Posture Management (CSPM), cloud workload protection, API risk detection, AI-SPM (AI Security Posture Management(, and many other capabilities. This allows the cloud security solution to not only detect suspicious user activity but also identify vulnerabilities within cloud workloads. By correlating data from both areas, the Orca Platform can identify potential privilege escalation attempts and take swift action to mitigate the threat.
Why a consolidated CNAPP is the future
While CIEM tools offer significant security benefits, the evolving cloud landscape demands a more comprehensive approach. This is where Cloud Native Application Protection Platforms (CNAPP) emerge as the future of cloud security.
CNAPP platforms combine the capabilities of CIEM with other necessary cloud security solutions, such as Cloud Security Posture Management (CSPM), Cloud Workload Protection Platform (CWPP), Cloud Detection and Response (CDR), Data Security Posture Management (DPSM), and more.
Unlike traditional CIEM tools, an agentless-first CNAPP such as Orca, offers complete coverage of your cloud estate to eliminate security blind spots and gaps. Additionally, advanced CNAPPs also offer comprehensive risk detection—discovering different types of risks that may affect identities and permissions but involve factors that go beyond the scope of traditional detection. CNAPPs also consolidate disparate tools and typically improve efficiency, convenience, and integration with other security applications.
Like any technology, not all CNAPPs provide the same capabilities or value. For example, many CNAPP solutions are the result of industry consolidation and vendors loosely coupling standalone technologies obtained through acquisition. These all-in-one offerings often present limitations in features, functionality, and coverage. In contrast, true CNAPP solutions have been developed natively, offering unified coverage, comprehensive risk detection, and seamless integrations with technologies seen as foundational to the security stack.
Overall, a holistic CNAPP delivers benefits beyond the scope of siloed CIEM tools. By consolidating visibility, control, and protection across your cloud infrastructure and workloads, a CNAPP fortifies your cloud security and compliance at scale. CNAPP empowers organizations to confidently secure their complex, ever-changing multi-cloud estate effectively and sustainably.
Learn more about the Orca Cloud Security Platform
The Orca Cloud Security Platform offers a true agentless-first CNAPP. Orca identifies, prioritizes, and remediates security and compliance risks for today’s most popular cloud service providers, including AWS, Azure, Google Cloud, Kubernetes, Alibaba Cloud, and Oracle Cloud.
The Orca Platform natively unifies—in a single platform—CIEM, CSPM, CWPP, DSPM, API Security, AI Security Posture Management (AI-SPM), Multi-Cloud Compliance, Vulnerability Management, Shift Left Security, and more. Orca’s patented SideScanning™ technology provides complete coverage and comprehensive risk detection across your entire cloud estate.
Orca brings together insights and data into its Unified Data Model, which enables it to fully contextualize risks and recognize when seemingly unrelated issues can create dangerous attack paths. As a result, Orca can effectively prioritize risks, reduce alert fatigue, and ensure your teams can focus on the most critical and important tasks.
Leveraging the Orca Platform begins as soon as you complete a quick 30-minute onboarding session. Schedule a demo with one of our experts to see how the Orca Platform can enhance your cloud security.
CIEM FAQs
What is the difference between CIEM and IAM?
IAM and CIEM are complimentary identity security solutions. CIEM is designed specifically for cloud environments, enabling visibility and control over entitlements, permissions, and privileged users. IAM, on the other hand, controls identities and rights across all IT resources, enforcing access regulations. However, IAM is not designed for the ephemeral and dynamic nature of cloud computing.
How does CIEM help in multi-cloud environments?
CIEM solutions enhance multi-cloud security by offering a centralized platform for managing policies and entitlements across cloud services. They monitor user access and permissions across environments, detecting abnormalities and ensuring security criteria are met.
Can CIEM reduce the risk of data breaches?
Yes, CIEM can reduce the risk of data breaches by enforcing least-privilege access, which guarantees that cloud entities only have the permissions they require to carry out their responsibilities. By consolidating identity governance, CIEM reduces risks such as data breaches caused by insufficient access control or credential compromise.




