Table of contents
According to Gartner, nine in every 10 global companies will be running containerized applications by 2027, up from just 40% in 2021. The dramatic growth of cloud-native applications is largely due to the benefits of containers and container orchestration platforms like Kubernetes. From enabling the creation and reproduction of consistent environments, to accelerating deployments, to increasing scalability and more, containers have revolutionized software development and digital ecosystems.
Still, containers present unique security challenges that today’s traditional security tools can’t address. Fortunately, container security, a newer branch of cybersecurity, has emerged to solve the inherent challenges and risks associated with containers.
In this guide, we dive deep into container security, revealing what it entails, why it’s important, and best practices your organization can apply.
Introduction to Container Security
A container is a standard unit of software that packages up code and all its dependencies so an application can run quickly and reliably from one computing environment to another. Lightweight, modular, and scalable, containers have transformed how applications are built and deployed.
Container security refers to strategies, solutions, and techniques that protect container-based systems and workloads from threats. Containerized environments present unique security risks that container security aims to solve. Examples include vulnerabilities in container images, excessive container permissions, lack of proper isolation between containers, limited container visibility, and more.
Container security covers the entire software development lifecycle (SLDC), including development, deployment, production, as well as cloud back to development.
Container Security Key Threats
Container deployments face a constant risk of security breaches due to potential vulnerabilities that can exist across the software supply chain, as well as misconfigured cloud and container environments. A container image with an exploitable vulnerability can compromise a significant portion of your cloud infrastructure, because images can propagate quickly to hundreds and thousands of cloud assets.
While not an exhaustive list, below are some of the common security risks associated with containers.
Vulnerabilities in container images
A container image is a template for creating a containerized environment, containing everything needed to run an application. Using the same image, developers can quickly and easily launch multiple containers that—if they contain vulnerabilities—can introduce flaws into the production environment. Container image vulnerabilities typically stem from dependencies such as insecure libraries transferred to a container image.
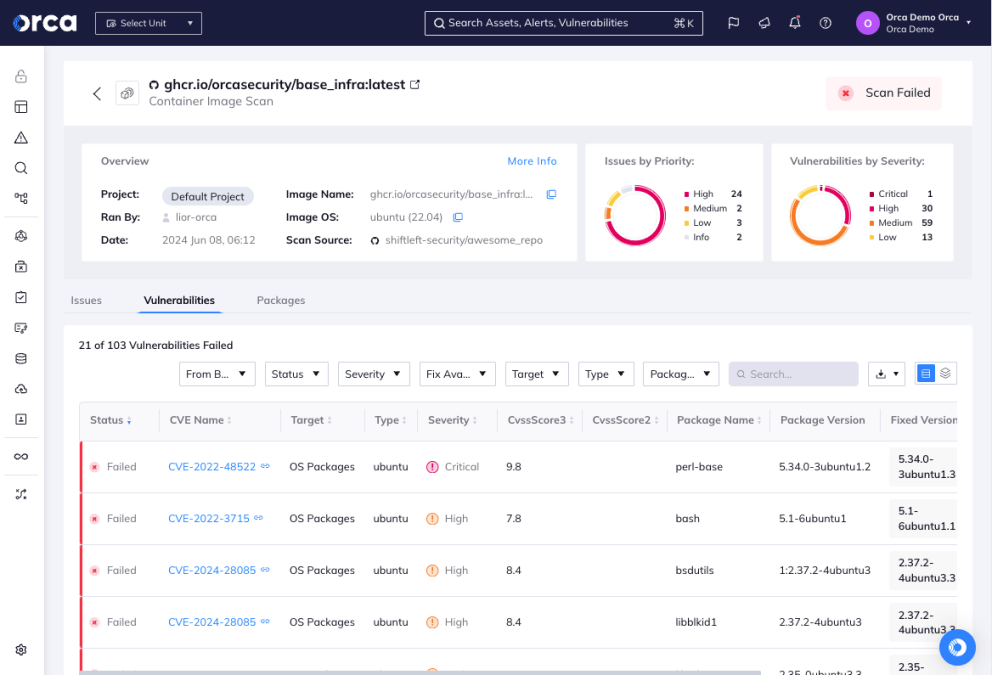
Container images infected with malware
Similar to vulnerabilities, container images infected with malware will introduce malicious code into production if the containers they create enter the live environment. Container malware can arise from multiple scenarios, including developers using malicious container images from public repositories, attackers inserting malware into source code repositories, or threat actors infiltrating container registries and substituting legitimate images with malicious ones.
Lack of visibility
Given their dynamic nature, containerized workloads pose visibility challenges that traditional monitoring tools often can’t solve. This includes issues ranging from a faulty container image to anomalous activity, which can rapidly surface and propagate without continual and in-depth monitoring.
Excessive container privileges
Containers running in privileged mode share the same privileges as the host system. This gives containers broader access to resources, while also creating the opportunity for privilege escalation attacks. If threat actors gain access to a privileged container, they can exploit vulnerabilities in container software or software running on the host, execute malicious code, and more. Excessive container privileges usually occur when Kubernetes security contexts are not properly defined.
Application vulnerabilities
When the applications hosted by containers contain vulnerabilities, they present significant security risks. These weaknesses can allow hackers to escalate privileges within a container, execute arbitrary code, exfiltrate data, and more. Vulnerabilities commonly arise when applications use outdated libraries or software with known flaws.
Inadequate access controls
Considering the impact of vulnerable or tainted container images, inadequate access controls also presents significant risks. Without proper access controls, unauthorized parties can modify, publish, or delete container images and introduce security risks and threats into your software development lifecycle (SDLC).
Best Practices for Container Security
The following container security best practices apply to one or more stages of the SDLC, including development, deployment, production, and cloud to development.
Use secure base images
Container images consist of layers and start with a base image, the foundational layer from which subsequent layers are derived. Because base images serve as the starting point for your container-based development, it’s best practice to use them with caution.
To use secure base images:
- Source a limited number of base images from trusted registries and repositories, making sure they’re actively updated and maintained.
- Scan all images for vulnerabilities.
- Remove unnecessary components from base images to reduce their size and attack surface.
- Maintain a set of golden base images that use an internally shared set of images. This allows you to deliver images while adhering to best practices.
Secure all open-source components
Open-source components make up most of today’s applications. Still, they remain a key source of security risks and vulnerabilities.
To secure open source components:
- Scan container images for known vulnerabilities using software composition analysis (SCA) tools.
- Regularly update your vulnerability database.
- Promptly address any detected issues.
- Ensure that open source packages aren’t vulnerable to dependency confusion
SCA tools scan source code to detect vulnerabilities that originate from third-party modules or libraries. They can examine your source repositories at the beginning of the CI/CD pipeline and alert you to any dependencies that could introduce security vulnerabilities into a live application.
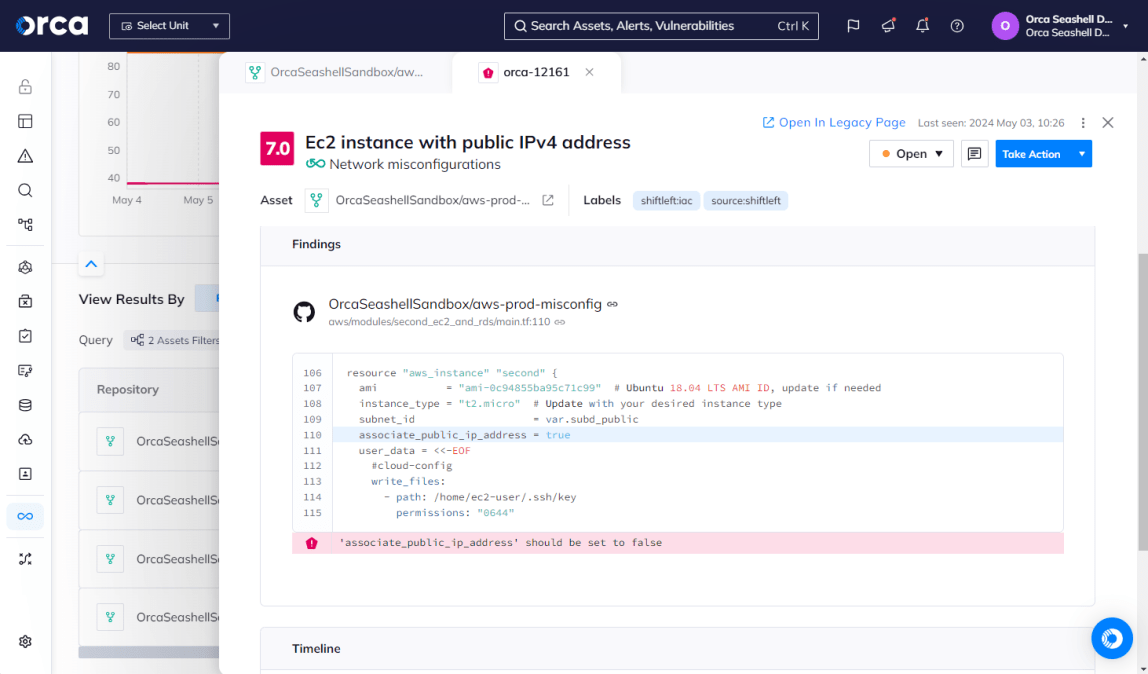
For example, the Orca Cloud Security Platform offers SCA analysis that automatically discovers vulnerabilities, misconfigurations, and hard-coded secrets in development, and generates alerts and remediation steps.
Apply image hardening techniques and image signing
Container hardening refers to the process of securing container images and removing any vulnerabilities. To harden your container images and protect their integrity:
- Apply image hardening best practices, including disabling unnecessary services, removing unnecessary packages, and minimizing the attack surface.
- Sign your container images using digital signatures. This helps verify their authenticity and integrity.
- Store and manage signing keys using a secure and trusted key management system.
Practice secure configuration management
To ensure proper access control and privileges:
- Establish secure configuration management processes for containers.
- Follow the principle of least privilege (PoLP) and configure container runtime settings, network configurations, and access controls appropriately.
Implement secrets management
Secrets management refers to a process that enables developers to safely and securely store sensitive data (e.g., passwords, API keys, and certificates) needed for authentication and access.
To implement secrets management:
- Use secrets management tools and adopt secrets management across the entire SDLC.
- Retrieve secrets securely at runtime and refrain from hard-coding them within a container image.
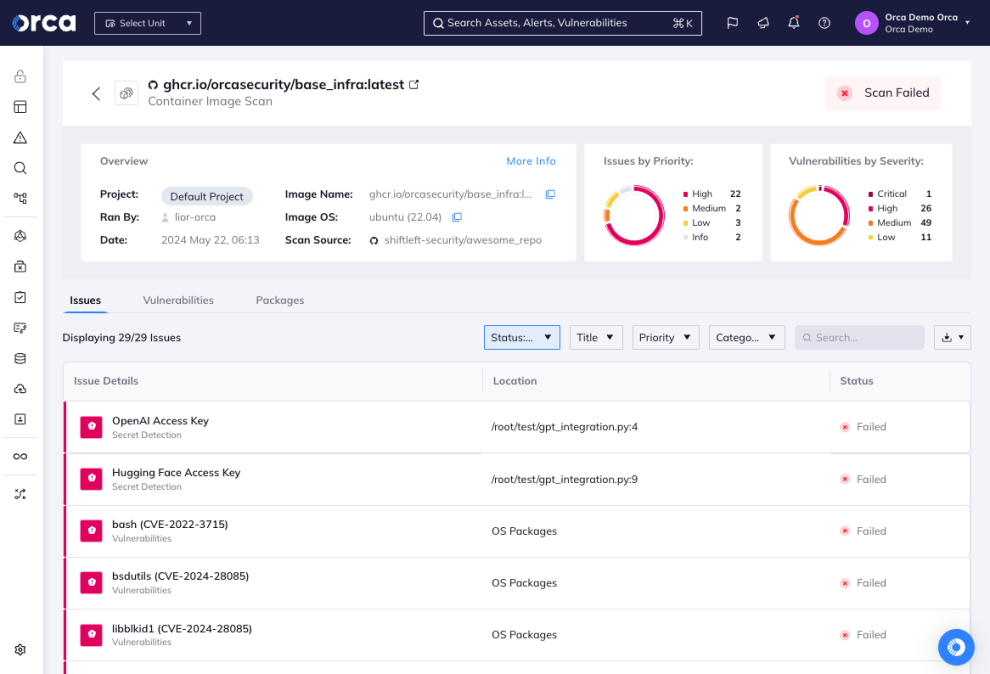
Regularly update and patch container images
Software patching is an essential security practice that also applies to container images.
To monitor and address container image vulnerabilities:
- Update base images and software packages within the container using the latest security patches.
- Regularly scan and update containers to address newly discovered vulnerabilities.
Implement network segmentation
Network segmentation refers to the process of splitting networks into smaller, distinct parts, which improves performance, security, and monitoring. Network segmentation provides multiple benefits for containers, enabling you to secure container communications, both between containers and also externally. It also helps prevent unauthorized access and data exfiltration.
To properly isolate containers:
- Utilize network segmentation techniques such as network policies and firewalls.
Incorporate IaC template scanning
Infrastructure-as-Code (IaC) is an important technology that enables organizations to quickly and repeatedly provision cloud infrastructure through code. It also aids container security by improving consistency, reducing errors, and reducing the need for manual configurations.
To maintain a secure deployment environment:
- Ensure that IaC artifacts undergo a thorough validation.
- Adopt IaC auditing by scanning for vulnerabilities and misconfiguration on the developer desktop or as part of your regular workflows for continuous integration, continuous delivery (CI/CD).
IaC auditing allows for end-to-end traceability, security, and accountability measures. As a result, you can ensure the protection and integrity of infrastructure code throughout its lifecycle.
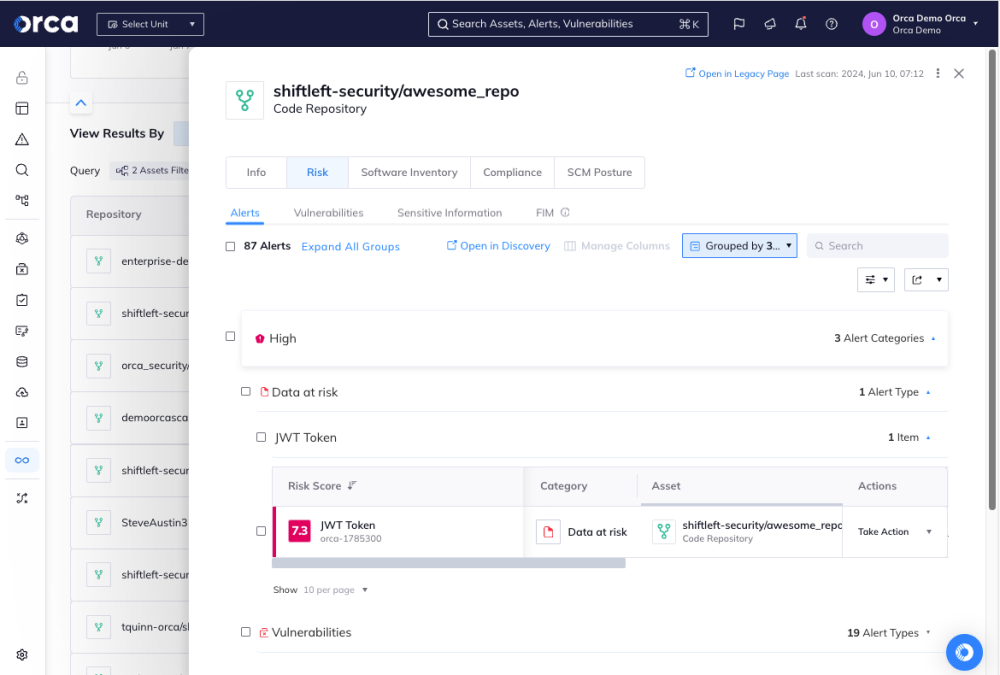
Set controls on registry images using rules-based image pulls
Container registries serve as repositories for container images. Developers can use registries to save, access, and share container images. They “push” container images by uploading them to a registry, and “pull” images by downloading them to another system. Registries often contain outdated or unused images that developers don’t want to pull and don’t need to scan.
To enhance container image scanning:
- Establish rules-based image pulls for automated container scanning tools. This ensures container scanning solutions focus on images in the pipeline and deployment, not those at rest in the registry.
Rules-based image pulls save developers considerable time. They automatically pull images from registries and schedule scans or rescans at set intervals.
Implement role-based access controls (RBAC)
Role-based access controls (RBAC) refers to the process of assigning privileges and access to roles, rather than specific users. RBAC is a type of access control that promotes security, consistency, and efficiency.
To strengthen access controls:
- Apply role-based access controls (RBAC) principles. This ensures that only authorized individuals or entities have access to deploy and manage containers.
- Limit access to sensitive resources by assigning appropriate roles and permissions to different users.
Harden container hosts
Like container images, hardening should also extend to container hosts to prevent security misconfigurations. Container hosts manage one or more containers, and if compromised, can put all containers running on the host at risk.
To harden container hosts:
- Follow best practices when configuring container runtimes. This includes enforcing resource limitations, using read-only file systems, and restricting privileged access within containers.
Tighten Kubernetes security and monitor container activity
Kubernetes offers built-in security features that provide significant benefits, such as granular access controls, security measures for sensitive data, workload isolation at runtime, and more.
To tighten Kubernetes security and improve container security:
- Implement comprehensive monitoring and logging mechanisms. This enables you to track container activity and detect any suspicious or unauthorized behavior.
- Utilize Kubernetes to gain visibility into container performance and security metrics.
- Enforce least-privilege access to Kubernetes.
- Use a cloud security platform for identifying and prioritizing risks inside the Kubernetes environment.
For Kubernetes best practices, consult Center for Internet Security (CIS) Kubernetes benchmarks.
Block risky builds
Cloud security solutions designed for DevSecOps enable you to establish “guardrails”—preventative measures to stop risky builds and other large security mishaps from making it into production.
To block risky builds:
- Set guardrail policies using the appropriate cloud security settings.
Monitor container behavior
Container behavior can identify potential security threats, a key reason to continuously monitor it for anomalies and suspicious activity.
To monitor container behavior:
- Implement monitoring and logging.
- Track resource usage, network connections, and system logs, including log monitoring of Linux system calls, Kubernetes audit logs, and cloud activity logs.
Encrypt sensitive data
It remains important to protect sensitive data within containers, both at rest and in transit. This can safeguard it from unauthorized access.
To encrypt sensitive data successfully:
- Use encryption protocols and secure storage mechanisms
Leverage API visibility and security
API misconfigurations are a common risk that attackers exploit to gain unauthorized access into container and Kubernetes environments.
To protect against API misconfigurations:
- Maintain a continually updated inventory of APIs across your cloud accounts.
- Leverage an API security solution that identifies and prioritizes API-related risks.
For example, the Orca Cloud Security Platform provides API security that continuously tracks and analyzes your managed and unmanaged API assets, including domains, subdomains, applications, path groups, users, and API endpoints. It also surfaces and prioritizes any potential API security risks.
Incident response and recovery
Incident response (IR) and recovery plays an essential role in maintaining a strong security posture. With strong measures in place, organizations can enhance container security during runtime or production, while reducing the risk of security breaches and further securing their containerized environment.
To develop an effective IR and recovery process:
- Develop and routinely test IR plans specific to container security incidents.
- Establish procedures for detecting, responding to, and recovering from security breaches or unauthorized activities within containers.
Integrate alerts with existing developer tools
When it comes to container security, alerts to potential security incidents only provide value if DevSecOps teams can receive and respond quickly to them. That illustrates the importance of cloud security tools that integrate alerts into common incident response, communication, and ticketing platforms. Equally important are cloud security solutions that can provide accurate origin and attribution tracking, which enables security teams to quickly work with the appropriate developer(s) to fix issues when discovered.
To integrate alerts with existing developer tools:
- Check the integrations of your container security solution.
- Activate the appropriate integrations.
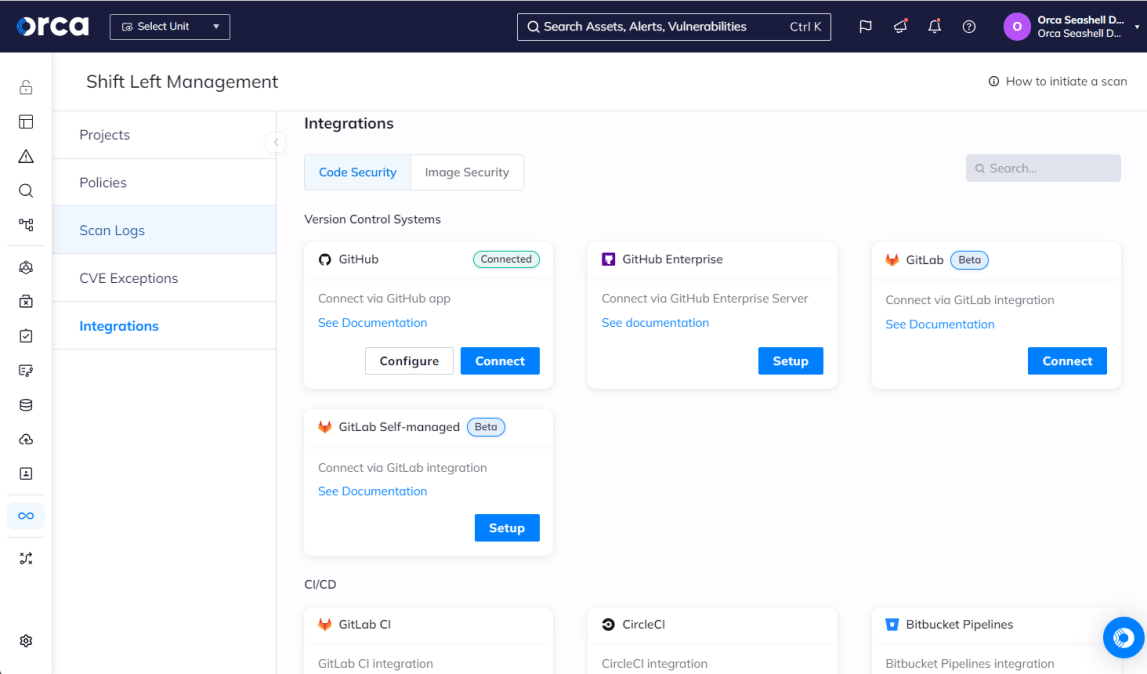
Cloud security solutions like the Orca Cloud Security Platform provide a number of technical integrations to enhance container security for DevSecOps. Integrations are particularly important for container security, as the process involves multiple teams (security, DevOps, and development) that span every stage of the SDLC. This illustrates the value and need for making alerts and other insights not only accessible in other platforms, but actionable consistent with existing workflows.
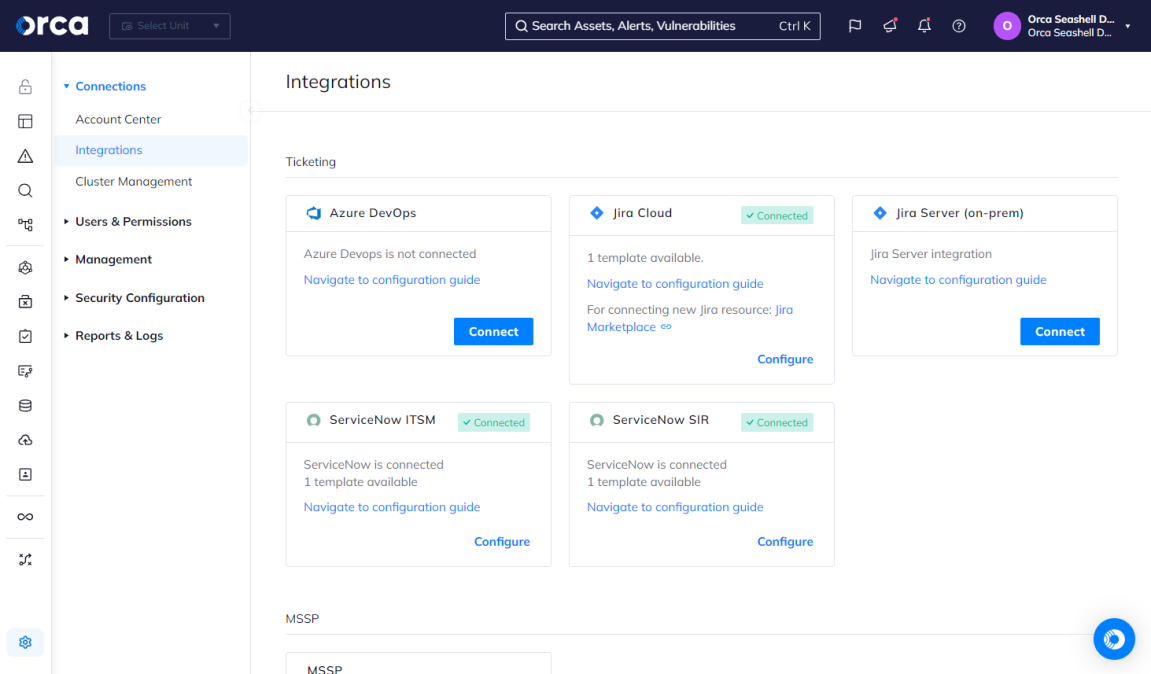
To illustrate, Orca integrates alerts with incident response tools such as OpsGenie and PagerDuty, automated ticketing systems like Jira and ServiceNow, and communication tools like Slack and email.
Additionally, to support origin and attribution tracking for detected issues, Orca traces misconfigurations or vulnerabilities in production directly to the original source code repository, including the exact line of code responsible for a detected risk. This eliminates the need to track down source artifacts and their respective owners and greatly reduces mean time to resolution (MTTR).
Adopt a cloud native application protection platform (CNAPP) to protect containers and Kubernetes environments
While several tools exist for container security, one of the most important ones is a cloud-native application protection platform (CNAPPs). CNAPPs unify multiple cloud security solutions in one platform, and this includes container security and all the capabilities, visibility, security measures, visibility, and risks associated with it.
CNAPPs effectively support a more effective approach to container security, a reason Gartner recommends adopting the technology: “Use a cloud-native application protection platform (CNAPP) to protect container environments from workload attacks and cloud misconfigurations.”
Unlike other solutions, CNAPPs allow DevSecOps teams to see development and production risks holistically in a single, unified data model, rather than a fragmented series of siloed risks. This allows teams to gain a fully contextualized view of the different risks across their cloud estate, which can then be prioritized according to severity, exploitability, radius, business impact, and more. As a result, security teams can get a true understanding and clear picture of criticality and remediate issues accordingly.
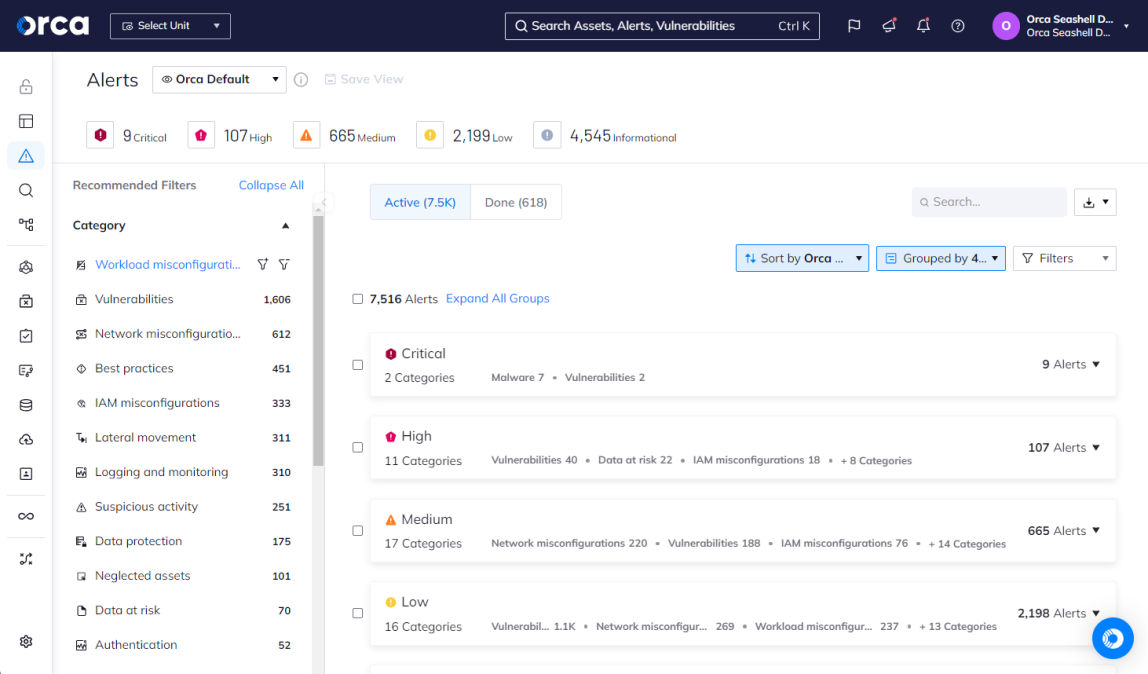
For example, true CNAPPs like the Orca Cloud Security Platform provide a holistic approach to cloud security and container security by unifying the capabilities of multiple standalone technologies. This includes cloud workload protection (CWPP), cloud security posture management (CSPM), cloud infrastructure and entitlements management (CIEM), data security posture management (DSPM), API security, container and Kubernetes security, and AI security.
Orca also provides “shift left” security capabilities including container image scanning, source code scanning, and IaC scanning to detect risks in these artifacts.
Container Security Tools and Solutions
Below are some of the most common tools and solutions used for container security.
Software composition analysis (SCA) tools
SCA solutions can enable organizations to scan source code in repositories for early visibility into vulnerabilities. Some solutions offer integrations with repositories and CI/CD pipelines to provide feedback to developers throughout the SDLC. SCA tools also help prevent vulnerabilities from reaching production environments.
Container monitoring tools
Container monitoring tools track container performance, events, and resource usage. These tools aim to prevent container failures and identify the cause of certain container-specific events. They also aim to optimize resource allocation.
Container runtime security
Container runtime security solutions safeguard containers against threats and vulnerabilities in production. These solutions automatically scan for vulnerabilities and other risks in the production environment and help prevent configuration drift.
Kubernetes security
As referenced, Kubernetes offers several important built-in security features. When properly configured and used, they provide significant benefits for securing container workloads and the Kubernetes platform.
Cloud native application protection platform (CNAPP)
Cloud-native application protection platforms (CNAPPs) consolidate multiple cloud security solutions into one platform, including container and Kubernetes security. True CNAPPs like Orca Cloud Security Platform offer comprehensive capabilities in a unified platform and advanced container security from pipeline to production. These solutions scan container images and IaC templates before deployment, continuously scan container registries, and monitor advanced threats, compliance issues, and vulnerabilities at runtime.
Strengthen your container security at every stage
Containers offer invaluable benefits to the modern SDLC and applications as we know them today. Yet they also introduce significant security concerns that require dedicated and ongoing attention. Without the right approach and technology to support container security, your organization runs the risk of dramatically expanding your attack surface. You also increase the likelihood of introducing new vulnerabilities and threats into your live environment and at an accelerated rate.
About Orca Security
Orca Security offers an advanced, comprehensive container security solution for AWS, Azure, Google Cloud Platform, Kubernetes, and other cloud service providers (CSP). The Orca Cloud Security Platform combines container and Kubernetes security with CWPP, CSPM, CIEM, API security, data security posture management (DSPM), Shift Left security, and AI security for unified cloud security.
With its agentless-first approach, Orca provides 100% coverage of your cloud environments and comprehensive security and compliance checks across the full SDLC. This ensures your organization can protect your CI/CD process, reduce friction between security and development teams, and embed security from development to cloud and back to development.
Leading organizations trust their cloud security to Orca, including Digital Turbine, Vercel, Docebo, Vivino, MailinBlack, Rods&Cones, Postman, Lemonade, and many more
FAQs
Why is container security important?
While containers offer substantial benefits for software development, they also represent an attractive target for attackers. Open-source resources have made organizations susceptible to container vulnerabilities and compromised containers. When pushed into production, these security risks can allow attackers to gain access to an organization’s environment, move laterally, carry out multi-phased attacks, and more.
How do you secure a containerized environment?
Securing a containerized environment calls for a collection of technologies, strategies, and ongoing measures. These apply across the entire software development lifecycle (SDLC) and generally include at least the following:
Build stage security activities
- Scanning source code for vulnerabilities
- Securing container images
- Detecting hard-coded secrets
- Scanning Infrastructure-as-Code (IaC) templates
Deploy stage security activities
- Tighten Kubernetes security settings
- Implementing guardrails to block risky deployments
- Implementing controls on container registries
- Role-based access control
Runtime security activities
- Detect and respond to runtime anomalies
- Identify emerging vulnerabilities and risks
- Leverage API security and visibility
Cloud-to-development activities
- Retrace production issues to origin and notify development teams
- Mitigate code






