Table of contents
- What is serverless computing and how does it work?
- A brief history and timeline of serverless
- The benefits of serverless computing
- What is serverless security and why do you need it?
- What are serverless security threats?
- How can you implement serverless security?
- Best practices for implementing serverless security
- Tools and technologies for securing serverless functions
- Challenges in securing serverless environments
- How a CNAPP can enhance serverless security
- Conclusion
- FAQs
When it comes to cloud computing, serverless technology plays an essential role. This groundbreaking approach continues to rapidly gain traction, with almost half of cloud-first companies already using it. A report by the Intellectual Market Insights forecasts serverless computing to reach nearly $59 billion (USD) in market value by 2031, with a compound annual growth rate of 23.17%. Rising demand for serverless computing points to some of its considerable benefits, including faster development cycles, better scalability, and significant cost reductions.
However, with these benefits come a new set of challenges when it comes to security. This includes the use of traditional security measures, which are designed to protect on-premise servers and not serverless architectures. As IT environments continue to migrate to the cloud, organizations need to become more aware of the security considerations of serverless computing.
In this guide, we break down the concept of serverless security, including what it entails, why it matters, and how you can best implement it for your organization.
What is serverless computing and how does it work?
Before introducing serverless security, let’s first understand the fundamentals of serverless computing. At its core, serverless computing is a cloud-based paradigm that allows developers to concentrate solely on writing and deploying code as functions that execute on-demand, triggered by specific events. This means you can build apps without the headache of managing the underlying infrastructure. Imagine a world where your code runs seamlessly without any server worries—this is the essence of serverless computing.
In this model, cloud providers take care of all the server management tasks, including provisioning, scaling, and maintenance. You simply upload your code, and the provider handles everything else. For example, a user’s HTTP request or a data change in a database can set off your functions. This event-driven architecture enables automatic scaling, meaning your application can effortlessly handle varying loads without manual intervention.
A prime example of serverless computing in action is AWS Lambda. It allows you to run code in response to events, such as changes in a DynamoDB database or file uploads to Amazon S3. Similarly, Google Cloud Functions and Azure Functions provide comparable capabilities, enabling developers to create applications that adapt dynamically to user interactions or system changes. This flexibility not only enhances efficiency but also leads to significant cost savings, as you only pay for the compute time you actually use.
Is it really “serverless”?
When we talk about serverless computing, the word “serverless” can often mislead people. While it hints at a lack of servers, serverless applications run on servers; it just means developers don’t have to manage them. Cloud providers handle all server-related jobs, which allows developers to concentrate on building applications.
A brief history and timeline of serverless
Serverless technology has its roots in the early 2010s. Google App Engine (2008), a Platform as a Service (PaaS), set the stage by letting developers deploy apps without managing infrastructure. The concept took off when AWS Lambda came out in 2014. It brought in Functions as a Service (FaaS), which let code run in response to events without setting up servers. This new approach changed how developers built apps, putting the focus on writing code instead of looking after servers.

After AWS Lambda other cloud providers like Microsoft Azure (2016) and Google Cloud (2018) rolled out their own serverless options. These included Azure Functions and Google Cloud Functions, which made the technology even more popular. By 2020, more than 60% of big companies were looking into serverless solutions.
Today, serverless computing is an important aspect of modern cloud computing, with several use cases and applications. Organizations of all sizes have adopted the technology to streamline operations and increase application performance. The flexibility of serverless technology has resulted in improved creativity and shorter time-to-market for applications. As this technology advances, it remains a driving factor behind new ideas and improved performance in cloud computing.
The benefits of serverless computing
Serverless computing provides various benefits, which explains why this technology is gaining so much popularity:
- Cost-efficiency: One of the biggest perks of going serverless is the potential for significant cost savings. This is because it offers a pay-as-you-go billing model where you only pay for the compute time you actually utilize. This goes a long way in helping businesses of all sizes reduce costs.
- Scalability on demand: Serverless architectures shine when it comes to handling varying workloads. For instance, if your application suddenly gets too much traffic, the serverless platform dynamically increases the number of servers to accommodate new demand, and when the traffic decreases, it reduces the number of servers. This means that whether you are handling a few relays or millions, performance stays the same.
- Reduced operational overhead: With serverless computing, the burden of managing servers shifts to the cloud provider, liberating your development team so they can focus on high-value responsibilities. They no longer need to worry about managing and maintaining servers. This enables them to accelerate innovation and introduce new products and services faster to market.
While the benefits of serverless computing are undeniable, organizations must implement the appropriate cloud security measures to realize them.
What is serverless security and why do you need it?
Serverless security is your digital bodyguard in the cloud-native world. As your organization embraces the flexibility of serverless computing, it opens new doors for potential threats. That’s where serverless security steps in, enabling you to build secure serverless functions and keep data safe from prying eyes and malicious actors.
At its core, serverless security is about protecting your serverless applications from vulnerabilities and attacks. It involves checking for security risks like misconfigured permissions, insecure APIs, and sensitive data exposure.
Here are a just a few reasons why serverless security matters:
- Unique attack surfaces: Serverless functions are often event-driven, creating new entry points that attackers may exploit if left unprotected.
- Shared responsibility: While cloud providers are responsible for protecting the cloud and its infrastructure, you’re accountable for securing all data and assets stored in the cloud. This arrangement is known as the “shared responsibility model.”
- Resource management: Without proper security, you could fall victim to financial resource exhaustion attacks, in which attackers force serverless functions to execute repeatedly.
What are serverless security threats?
As you dive into the world of serverless computing, it’s crucial to be aware of the potential security risks lurking in the shadows. By understanding these common threats, you’ll be better equipped to implement robust serverless security practices and keep your applications safe in the cloud.
Let’s explore some of the most common threats you might encounter:
#1 Function event-data injection
Your serverless functions often process event data from various sources. Malicious actors can exploit this by injecting harmful code or commands into the event data. Always validate and sanitize your inputs to prevent unwanted surprises.
#2 Broken authentication
With serverless architectures, you’re relying heavily on APIs and microservices. This means authentication becomes a critical concern. Weak or improperly implemented authentication mechanisms can leave your functions vulnerable to unauthorized access.
#3 Insecure configurations
It’s easy to overlook a cloud provider’s security settings when deploying serverless functions. Misconfigured permissions, overly broad access policies, or exposed secrets can open the door to potential breaches. Properly configuring these important security settings can help you keep your serverless environment secure.
#4 Dependency vulnerabilities
Your serverless functions likely depend on various third-party libraries and packages. While these can boost productivity, they can also introduce security risks. An example of this is dependency confusion supply chain attacks. Stay vigilant and regularly update your dependencies to patch known vulnerabilities.
How can you implement serverless security?
Implementing serverless security requires a multi-faceted approach. You’ll need to focus on several key areas to ensure your serverless applications remain protected.
Gain visibility across your attack surface
You can only protect what you can see. While this holds true for every domain in cybersecurity, it especially applies to cloud and serverless security. Knowing what assets and services are deployed in your cloud estate is essential, as each can present an opportunity for attackers to exploit if not properly secured.
For example, the Orca Cloud Security Platform provides a complete inventory of serverless workloads across your cloud estate, allowing users to gain full visibility into them and their associated security risks.
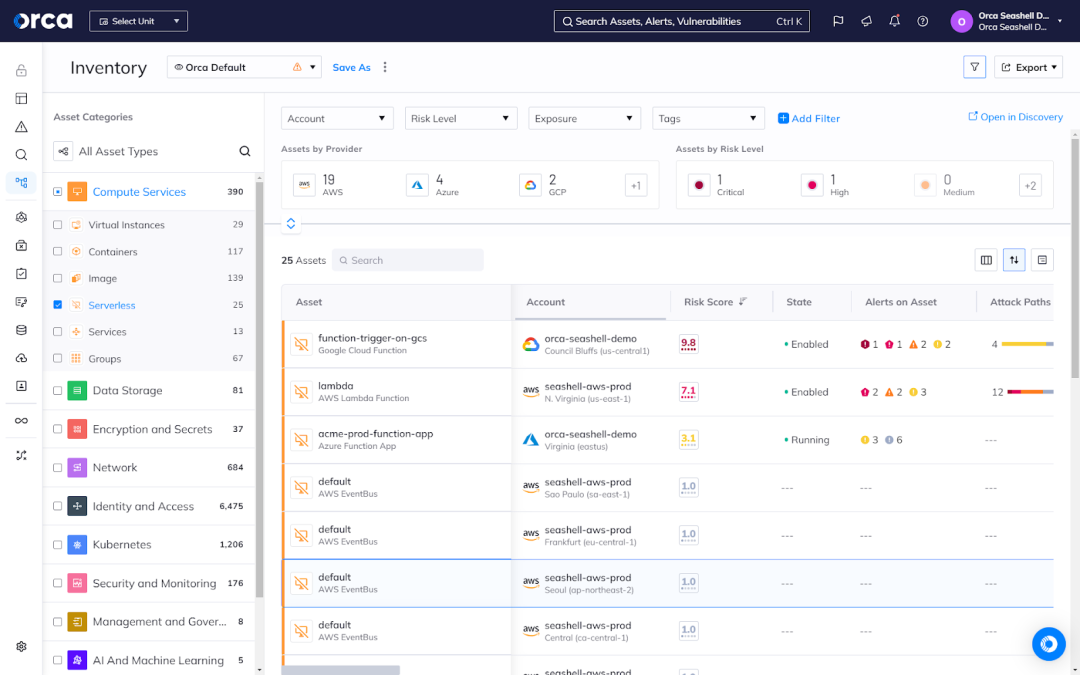
Prioritize risks
In reality, organizations can’t address every security risk or vulnerability discovered in their cloud environments, nor would it be practical to attempt to accomplish this task. Serverless security calls for prioritizing the most critical risks in your cloud estate, allowing your teams to remediate the issues that present the most danger to business continuity.
Risk prioritization calls for a continual and dynamic assessment of the risks related to your serverless functions. It also requires assigning a risk rating (low, medium, high, critical) and numerical score to allow security teams to quickly understand which risks to focus on first.
For example, the Orca Cloud Security Platform dynamically assesses the risks associated with serverless functions using multiple criteria. For example, these can include factors such as severity of a vulnerability (i.e., CVSS score), the likelihood an attacker may exploit it (i.e., EPSS score), whether an asset is externally exposed, whether an asset contains sensitive data, and much more.
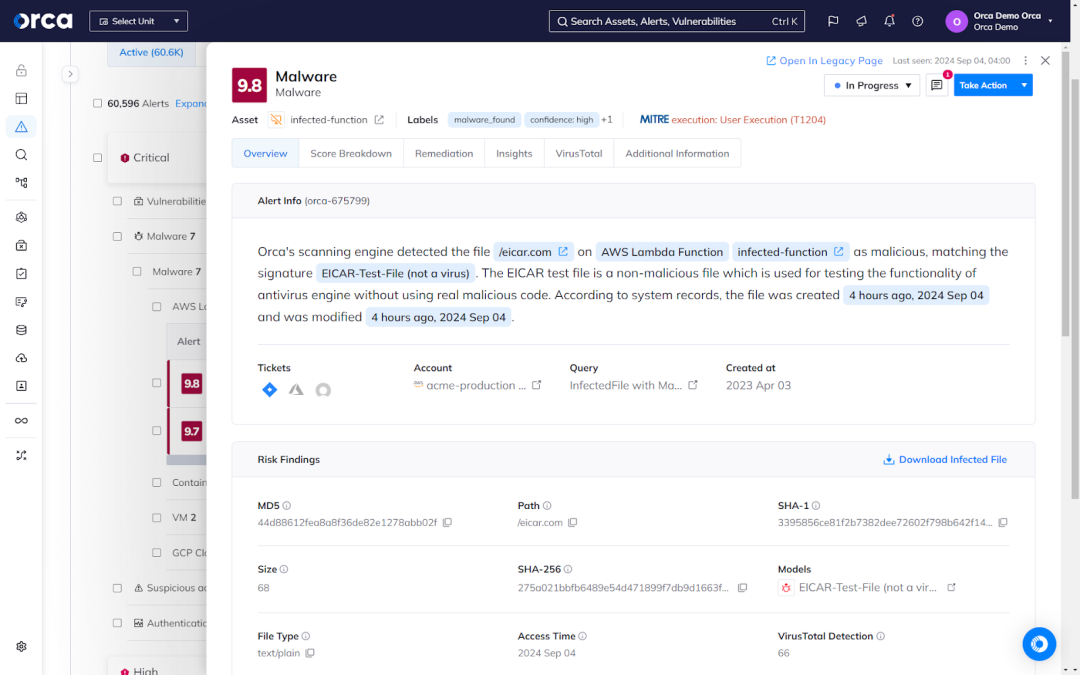
Shift security left
Serverless security also calls for implementing preventative measures that stop development teams from introducing security risks into your live environment. Known as Shift Left Security, this approach incorporates security practices into the early phases of the software development lifecycle (SDLC). Shift Left Security involves various code security practices, including Infrastructure-as-Code (IaC) Security, Secrets Management, Container Image Scanning, Software Composition Analysis (SCA), and Source Code Management Posture Management (SCM-PM).
Shift Left Security enables security teams to establish policies that act as guardrails for developers, blocking risky builds from making it to production and enabling developers to fix issues at the most opportune, least costly, and productive phase.
The Orca Cloud Security Platform provides a comprehensive Shift Left Security solution that encompasses both code security (i.e., IaC Security, Container Image Scanning, Secrets Management, SCA) and SCM-PM.
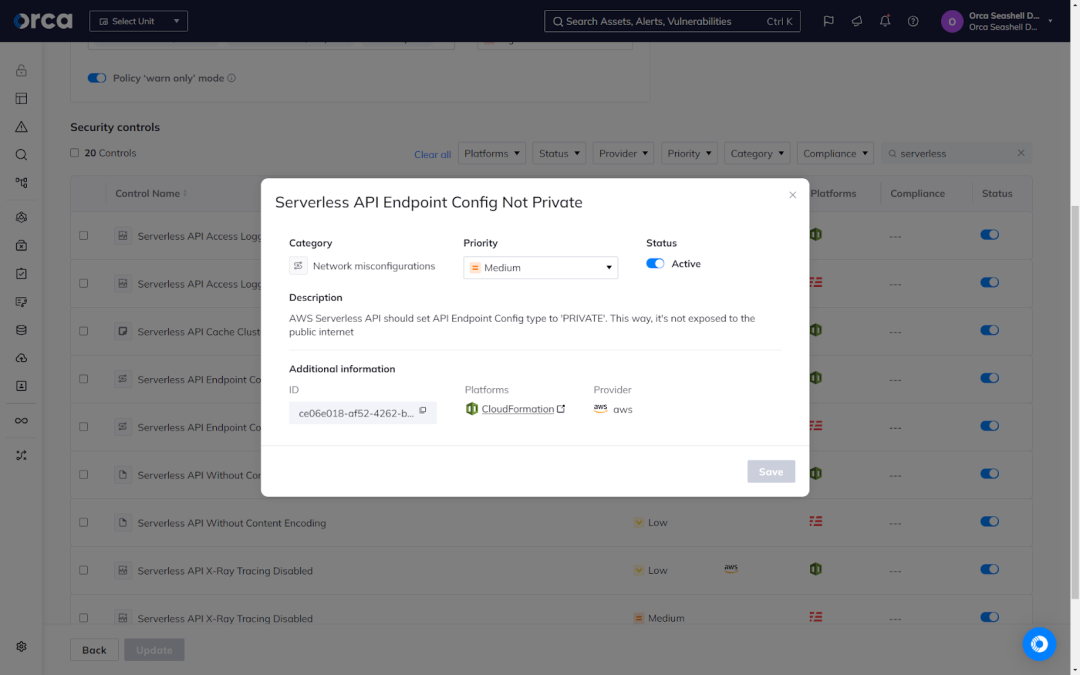
Notably, shifting security left calls for better collaboration between security and development teams. This explains why organizations often leverage Shift Left Security solutions with seamless integrations between security and development tools, which eliminate the need to establish new workflows or learn new applications.
For example, Orca features more than 50 technical integrations with a variety of solutions regularly used by development and DevOps teams, including two-way integrations with Jira, ServiceNow, and other platforms. This infuses security from Orca into the tools used by developers, improving visibility and productivity while reducing friction.
Manage access controls
Effective access control is crucial for securing your serverless functions. Start by implementing strong authentication methods, like multi-factor authentication (MFA), to protect access to your functions. Following the principle of least privilege is key—grant only the permissions necessary for each function to do its job. This minimizes potential damage if a function is compromised.
Additionally, consider adopting a Cloud Infrastructure Entitlement Management (CIEM) solution, which manages and secures access rights and permissions (often known as entitlements) within cloud environments. CIEM solutions define and enforce the actions a cloud identity can perform and what resources it can access. This technology helps organizations reduce security risks and meet compliance requirements.
The Orca Platform offers an advanced CIEM solution that discovers and catalogs all identities in your cloud environment, as well as provides a complete analysis of the capabilities and permissions associated with each identity across your cloud estate.
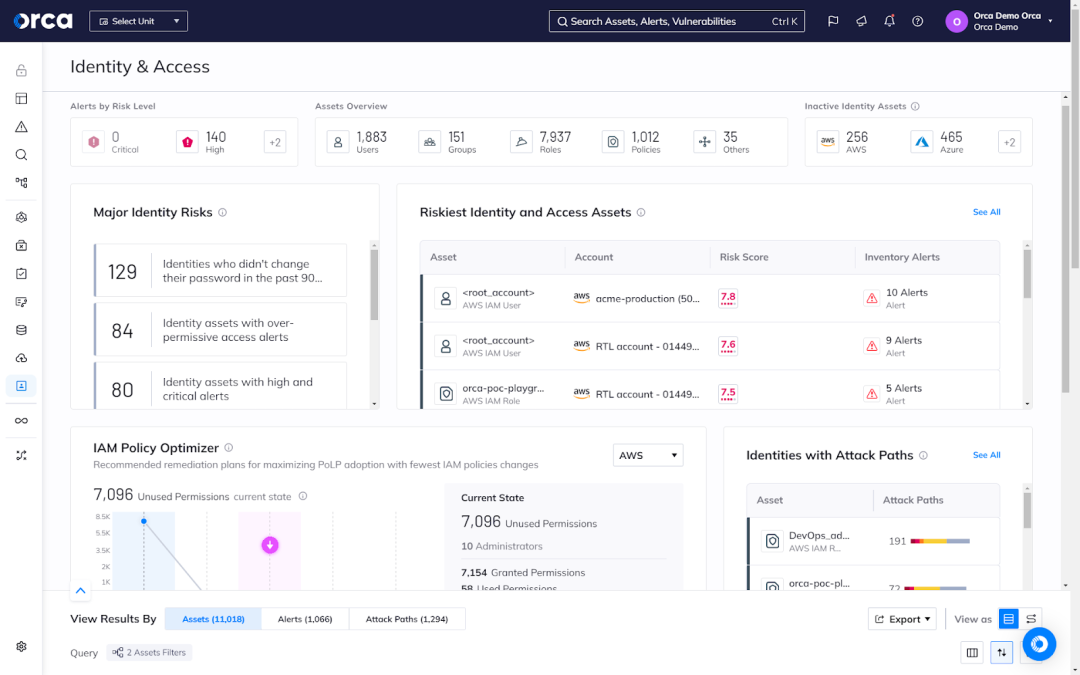
Encrypt data
Encrypting your data is a vital step in safeguarding sensitive information in a serverless architecture. By encrypting data both in transit and at rest, you ensure that it remains protected from unauthorized access. Most cloud providers offer built-in encryption services along with key management tools, making it easier to implement these safeguards. Be sure to encrypt all sensitive information, including environment variables and configuration files, and follow best practices for managing your encryption keys. This way, you keep your data secure and maintain peace of mind.
Best practices for implementing serverless security
Reduce your attack surface
When it comes to serverless security, less is often more. By adopting a minimalist approach, you can significantly reduce the attack surface and mitigate potential vulnerabilities. Keep your functions focused and lean, granting only the necessary permissions for each task. This not only strengthens security but also optimizes performance and cost-efficiency.
Serverless functions are designed for executing small, discrete pieces of code on an on-demand basis. Deviating from this principle and treating them as a means to deploy any type of application is a common pitfall. Not only does this undermine the core benefits of serverless, but it also increases the risk of misconfiguration and introducing insecure dependencies.
To enhance serverless security, strive for minimalism. Minimize the code within each function, focusing on the essential elements. This strategy not only reduces costs and improves performance but also strengthens your overall security posture.
Isolate functions
To bolster the security of your serverless applications, it’s essential to isolate functions whenever feasible. By adopting a zero-trust approach and restricting resource access, you can minimize the risks associated with function interactions.
Key strategies:
- Assume no trust (Zero-Trust approach): Treat each function as an independent entity, verifying the authenticity and integrity of data received from others.
- Limit resource access: Restrict the resources each function can access to prevent unauthorized access.
- Decouple function execution: Avoid direct function calls to mitigate risks like financial exhaustion attacks. Instead, employ an external control plane to manage function execution.
By implementing these isolation strategies, you can significantly strengthen the security of your serverless applications and mitigate potential vulnerabilities.
Leverage built-in security features
Take advantage of the security features offered by your serverless platform. Many providers offer tools for encryption, access control, and threat detection specifically designed for serverless environments. By utilizing these built-in capabilities, you can enhance your security posture without reinventing the wheel.
Tools and technologies for securing serverless functions
As serverless computing gains popularity, it’s essential to equip yourself with the right security tools to protect your functions and data. Here’s a streamlined look at the key solutions you’ll want in your serverless security toolkit.
Key technologies to consider for securing serverless functions
- Cloud Security Posture Management (CSPM): Enables organizations to leverage and maintain the proper security configurations of their cloud services. CSPM tools automate the enforcement of security policies, monitor misconfigurations, and centralize the visibility of the entire cloud control plane.
- Cloud Workload Protection Platform (CWPP): Secures cloud-based workloads across serverless functions, virtual machines, and containers. It provides continuous protection through threat detection and monitoring.
- Data Security Posture Management (DSPM): Manages the risks related to sensitive data in the cloud by providing centralized visibility, comprehensive detection, and continuous monitoring.
- Vulnerability Management: Identifies, evaluates, and facilitates the remediation of vulnerabilities. This type of solution analyzes the impact and exploitability of vulnerabilities, prioritizes them by severity, and presents multiple options for fixing them.
- Shift-Left Security: Referenced previously, Shift Left Security involves implementing code security and SCM-PM early into the SDLC to prevent vulnerabilities and other security risks from making it to production environments.
- Cloud Infrastructure Entitlement Management (CIEM): Also mentioned previously, CIEM solutions secure identities and cloud entitlements, as well as ensure least privilege permissions.
Challenges in securing serverless environments
Implementing serverless security comes with its own set of unique challenges. As you dive into this new paradigm, you’ll encounter several hurdles that require innovative solutions.
Increased attack surface
With serverless, your application is broken down into smaller, independent functions. While this offers great flexibility, it also means more entry points for potential attackers. You’re now dealing with a larger number of components, each needing its own security considerations.
Limited visibility and control
Unlike traditional setups, you don’t have direct access to the underlying infrastructure in serverless environments. This can make it tricky to monitor and control security aspects that you were previously able to manage directly.
Ephemeral nature of functions
Serverless functions are short-lived and stateless. They spin up quickly, execute, and then disappear. This transient nature makes it challenging to apply traditional security measures or conduct thorough security audits.
Shared responsibility model confusion
The line between your responsibilities and those of the cloud provider can sometimes blur in serverless setups. Understanding and managing this shared responsibility model is crucial but can be complex, especially for teams new to serverless architectures.
By recognizing these challenges, you’re better equipped to tackle serverless security head-on. Remember, while these hurdles exist, they’re not insurmountable. With the right approach and tools, you can build robust, secure serverless applications.
How a CNAPP can enhance serverless security
In today’s rapidly changing cloud security landscape, a Cloud Native Application Protection Platform (CNAPP) can be your secret weapon for strengthening serverless environments. Let’s explore how these powerful tools can elevate your serverless security.
- Comprehensive visibility: A CNAPP provides a complete view of your entire serverless ecosystem. With real-time insights into your functions, data flows, and potential vulnerabilities, you gain a holistic perspective that is crucial for identifying security gaps that might otherwise go unnoticed.
- Automated risk assessment and prioritization: CNAPPs automatically analyze your cloud assets and detect any security risks. The most advanced CNAPPs offer detection for all types of risks and effectively prioritize them by dynamically assessing multiple factors. This automation not only saves you time but also ensures you stay ahead of emerging threats.
- Simplified compliance: Navigating the maze of ever-changing regulations can be overwhelming. A CNAPP simplifies compliance by automatically mapping detected security risks in your serverless infrastructure against various standards. The most sophisticated CNAPPs provide this automation for all major compliance regulations and industry standards and offer features for simplifying reporting.
Like any security solution, not all CNAPPs provide equal value. Those developed natively offer optimal protection and performance, compared to others developed by integrating multiple point solutions. By integrating a CNAPP into your security strategy, you can significantly enhance the protection of your serverless environments, allowing you to focus on innovation while keeping your applications secure.
About the Orca Cloud Security Platform
As a true agentless-first CNAPP, the Orca Cloud Security Platform identifies, prioritizes, and remediates security risks and compliance issues across multi-cloud environments offered by AWS, Azure, Google Cloud, Kubernetes, Alibaba Cloud, and Oracle Cloud.
The Orca Platform provides comprehensive serverless security by natively integrating advanced solutions that include CSPM, CWPP, CIEM, DSPM, API Security, AI Security Posture Management (AI-SPM), Multi-Cloud Compliance, Vulnerability Management, Shift Left Security, and more. Leveraging its patented SideScanning™ technology, Orca provides full visibility and security across your entire cloud estate for every type of cloud risk.
Orca captures and integrates data insights into its Unified Data Model, which it uses to contextualize risks and uncover hidden, interrelated issues that present dangerous attack paths. As a result, Orca can effectively prioritize risks, reduce alert fatigue, and ensure your teams can focus on the most critical and important tasks.
To see how the Orca Platform can enhance your cloud security, schedule a personalized demo with one of our experts. You can begin leveraging the Orca Platform as soon as you complete a quick onboarding session (~30 minutes).
Conclusion
Serverless computing affords your organization undeniable benefits. Yet for the advantages that it offers in terms of speed and flexibility, it also presents significant security risks. That’s why realizing the full potential of serverless computing calls for a significant commitment to serverless security. Serverless security, along with other areas of cloud security, can help you mitigate and remediate the threats explored previously and preserve your business continuity.
FAQs
Why do you need serverless security?
While serverless infrastructures shift many traditional security concerns to the provider, they also pose unique security risks. For example, functions could be exposed to the public internet, increasing your attack surface. Furthermore, the ephemeral nature of serverless makes monitoring and logging more difficult. Implementing strong serverless security, therefore, protects your data, prevents illegal access, and ensures compliance with regulations.
What’s the difference between serverless and PaaS?
Both serverless and Platform-as-a-Service (PaaS) abstract away infrastructure management, although they work differently. Serverless is more granular, allowing you to run code in short-lived, stateless functions that scale automatically. PaaS, on the other hand, often involves distributing fully functional applications that run continually. Serverless billing is based on actual compute time, whereas PaaS often charges for allocated resources regardless of usage.
What are the challenges of serverless computing?
Serverless computing comes with several challenges:
- Cold starts: Functions may experience latency when initializing after periods of inactivity.
- Limited execution time: Most providers cap function runtime, complicating long-running tasks.
- Complex debugging and monitoring: The distributed nature of serverless can make troubleshooting difficult.
- Security concerns: New attack vectors and the shared responsibility model require careful consideration.
Does serverless security need a unique approach?
Yes, serverless security requires a different approach from standard cloud security due to its unique architecture. In serverless computing, the underlying infrastructure is abstracted, and developers focus on deploying code rather than managing servers. This shift reduces some attack surfaces, like server management, but introduces new vulnerabilities such as insecure functions, misconfigured permissions, and third-party dependencies. The ephemeral nature of serverless functions also requires more dynamic monitoring and automated security policies.
Table of contents
- What is serverless computing and how does it work?
- A brief history and timeline of serverless
- The benefits of serverless computing
- What is serverless security and why do you need it?
- What are serverless security threats?
- How can you implement serverless security?
- Best practices for implementing serverless security
- Tools and technologies for securing serverless functions
- Challenges in securing serverless environments
- How a CNAPP can enhance serverless security
- Conclusion
- FAQs






