We are thrilled to share with you that Orca Security has now officially obtained a patent for our innovative SideScanningTM technology. Orca’s SideScanning revolutionized the cloud security industry by enabling the first comprehensive cloud security platform with insight into workloads as well as configurations without requiring the installation or management of a single agent. Starting as just an idea four years ago and now seeing this come to fruition in a globally deployed cloud security platform that’s an innovation leader in the space, is even more exciting to us.
We would like to take this opportunity to thank our Orca employees and partners for their dedication and hard work, as well as our customers who placed their trust in us to be their cloud security partner. You are all central to the realization of our vision to create a modern and comprehensive cloud security platform that instead of slowing teams down, enables them to innovate in the cloud with speed and confidence. At Orca we believe in a customer first approach, and are proud to help companies of all sizes in any vertical–from startups to large enterprises–improve their cloud security postures.
Looking back over the past year, Orca has experienced tremendous growth. Not only have we doubled our number of employees and more than tripled the number of Orca customers, we have also added four major capabilities to our platform to further deliver on our promise to provide the most comprehensive cloud security platform with the widest and deepest cloud risk visibility, including Attack Path Analysis, Shift Left, Cloud Detection & Response, and API Security. Our latest addition to further expand our coverage is support for Alibaba Cloud, which is going to be an important offering for our Asia-Pacific customers and partners.
What life was like before Orca Security
To grasp how Orca has dramatically simplified and improved cloud security, let’s take a look at what the cloud security industry was like before Orca…
Agents deployed on cloud workloads: When the cloud started to gain popularity, security vendors simply used their existing technologies and applied them to the cloud. As the saying goes: ‘If all you have is a hammer, everything looks like a nail’. To gain insight into cloud workloads, including risks such as vulnerabilities and malware, organizations needed to install an agent on every asset in the cloud environment. Once cloud adoption started to grow, it quickly became clear that this approach (also called cloud workload protection platforms) did not scale and created serious blind spots due to partial deployment.
Siloed API-based Cloud Security Posture Management: The next type of solution vendors introduced was cloud security posture management (CSPMs) solutions, which did not require any agents. These tools analyzed cloud provider APIs and alerted to misconfigurations and compliance issues at the cloud control plane. While CSPMs are extremely valuable, they do not offer any insight into workloads. This meant that organizations were basically still left with the problem of having to install agents in their cloud if they wanted any protection from vulnerabilities or malware.
Many organizations ended up having to deploy multiple solutions to cover workloads and configurations. Apart from operational inefficiencies, this meant that security teams were having to sift through hundreds of alerts from multiple security tools every day, trying to figure out which ones needed priority and which ones were duplicate. All this before they could even get round to remediating.
How the modern Cloud Security Platform took shape
Seeing the challenges that organizations were facing with cloud security, we both started to think about what a modern cloud security platform would look like if we utilized the cloud infrastructure instead of the traditional network structure. The idea of SideScanning was born. Instead of relying on agents, SideScanning reads the workload’s cloud provider runtime block storage without the need to install anything in the cloud. All that is needed is to connect to a cloud account, and the Orca platform literally starts scanning within minutes of initial setup.
Apart from operational efficiencies, combining the intelligence from cloud workloads, configurations and identities in a single platform provides another important benefit: Orca has access to the wide and deep contextual intelligence needed to see the cloud environment just like an attacker does. An attacker makes use of any type of weakness they can find, no matter whether it is located in a workload, configuration or identity. Understanding how attackers can combine weaknesses to create dangerous attack paths to the company’s most critical assets allows Orca to quickly and accurately prioritize the risks that pose the greatest danger to the company.
The four Cs that the Orca Platform was built on
From the beginning, we have stayed true to the four principles that we believe an effective cloud security platform should be built on: 100% coverage of assets, comprehensive security incorporating all cloud risks, contextual intelligence to surface the most critical risks, and finally, consumable security to empower teams to take action and remediate issues.

Orca Security company timeline
- 2019, January 19: Orca Security is Officially Founded
- 2019, June 12: Orca Security Exits Stealth Mode | Link
- 2020, July 28: Orca Releases 2020 State of Public Cloud Security Risks Report | Link
- 2020, October 13: Orca Releases 2020 State of Virtual Appliances Security Report | Link
- 2021, June 9: Gartner Names Orca a Cool Vendor | Link
- 2022, January 13: Research Pod Announces AWS BreakingFormation Vulnerability | Link
- 2022, January 13: Research Pod Announces AWS SuperGlue Vulnerability | Link
- 2022, March 7: Research Pod Announces Azure AutoWarp Vulnerability | Link
- 2022, March 15: Orca Releases 2022 Alert Fatigue Report | Link
- 2022, March 31: Orca Unveils Attack Path Analysis | Link
- 2022, May 9: Research Pod Announces Azure SynLapse Vulnerability | Link
- 2022, June 29: Orca Brings Interactive Cloud Camps to Market | Link
- 2022, July 19: Orca Releases Integrated Cloud Detection and Response Capabilities | Link
- 2022, August 31: Orca Security Wins SC Media Award for Best CSPM Solution | Link
- 2022, September 1: Research Pod Releases Local Privilege Escalation in Apache Spark | Link
- 2022, September 13: 2022 State of Public Cloud Security Report Released | Link
- 2022, October 18: Orca Releases Industry First Agentless API Security Capabilities
Announcing new platform innovations
As we continue to build the industry’s most comprehensive Cloud Security Platform, our team is committed to rapid innovation and continued improvement. This past year, we have had notable releases that expand our powerful feature set – including Attack Path Analysis, API Security, Cloud Detection and Response, and more. Our team is proud to deliver the following capabilities that improve the overall usability, customization, and visibility as part of the Orca Platform.
Graph visualization to easily understand interconnected cloud assets
Security teams want to quickly and easily understand how a specific cloud asset or workload connects to other cloud resources, along with their corresponding risks. To improve this capability, Orca is now unveiling a graph visualization UI that automatically stitches interconnected assets and workloads together so security teams can best understand configuration status, risks, alerts and other vital telemetry across their environment.
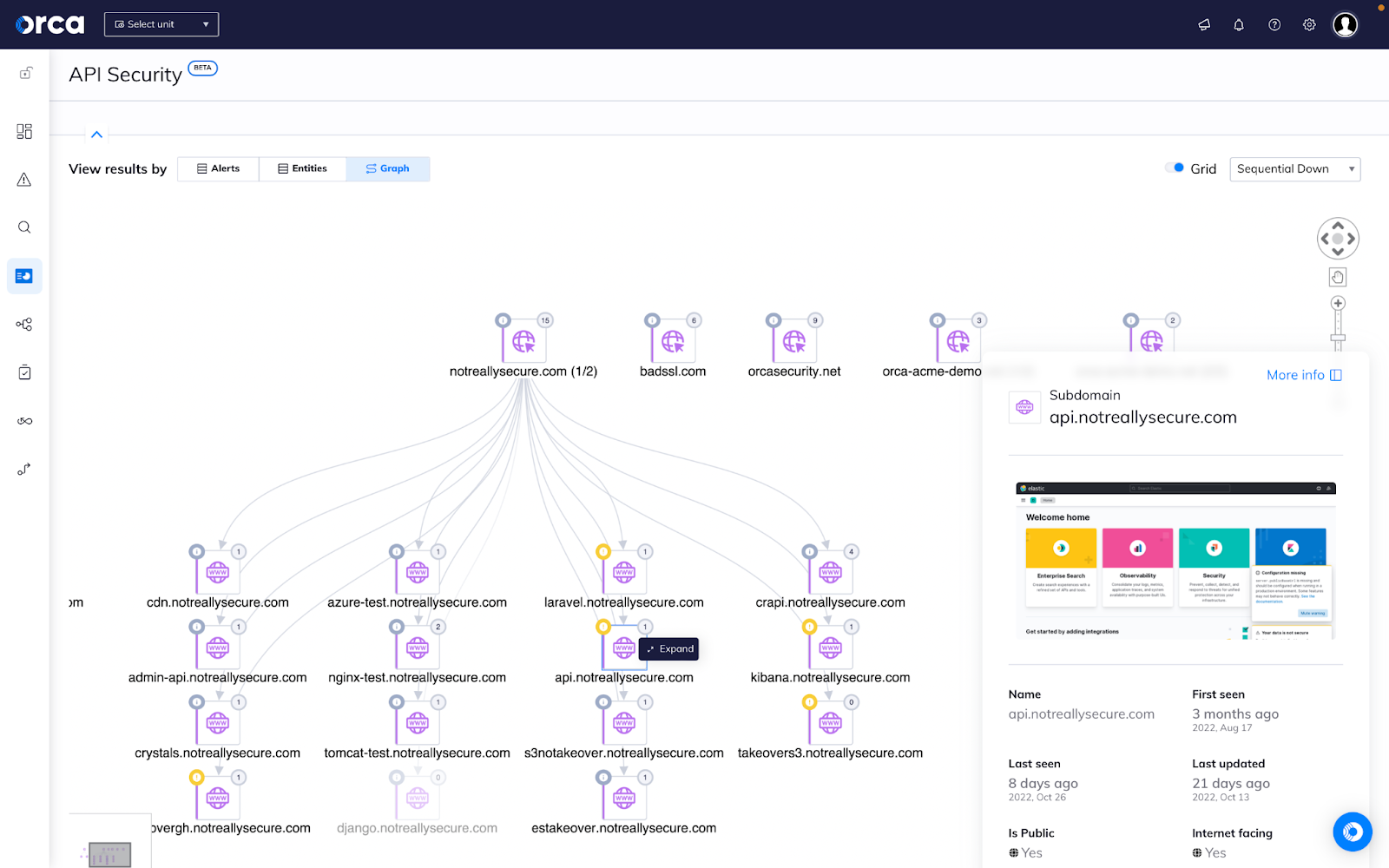
The updated graph visualization UI is now available within the Discovery Search tab.
Custom Risk Dashboard with pre-built dashboard widgets
Every organization, business unit, and team within an enterprise is unique with their own business goals, security needs, and compliance requirements. So, we decided to make the main Risk Dashboard within the Orca Platform fully customizable with 50+ pre-built widgets for creating the security, alerting, inventory, or compliance views you need to meet the needs of your organization.
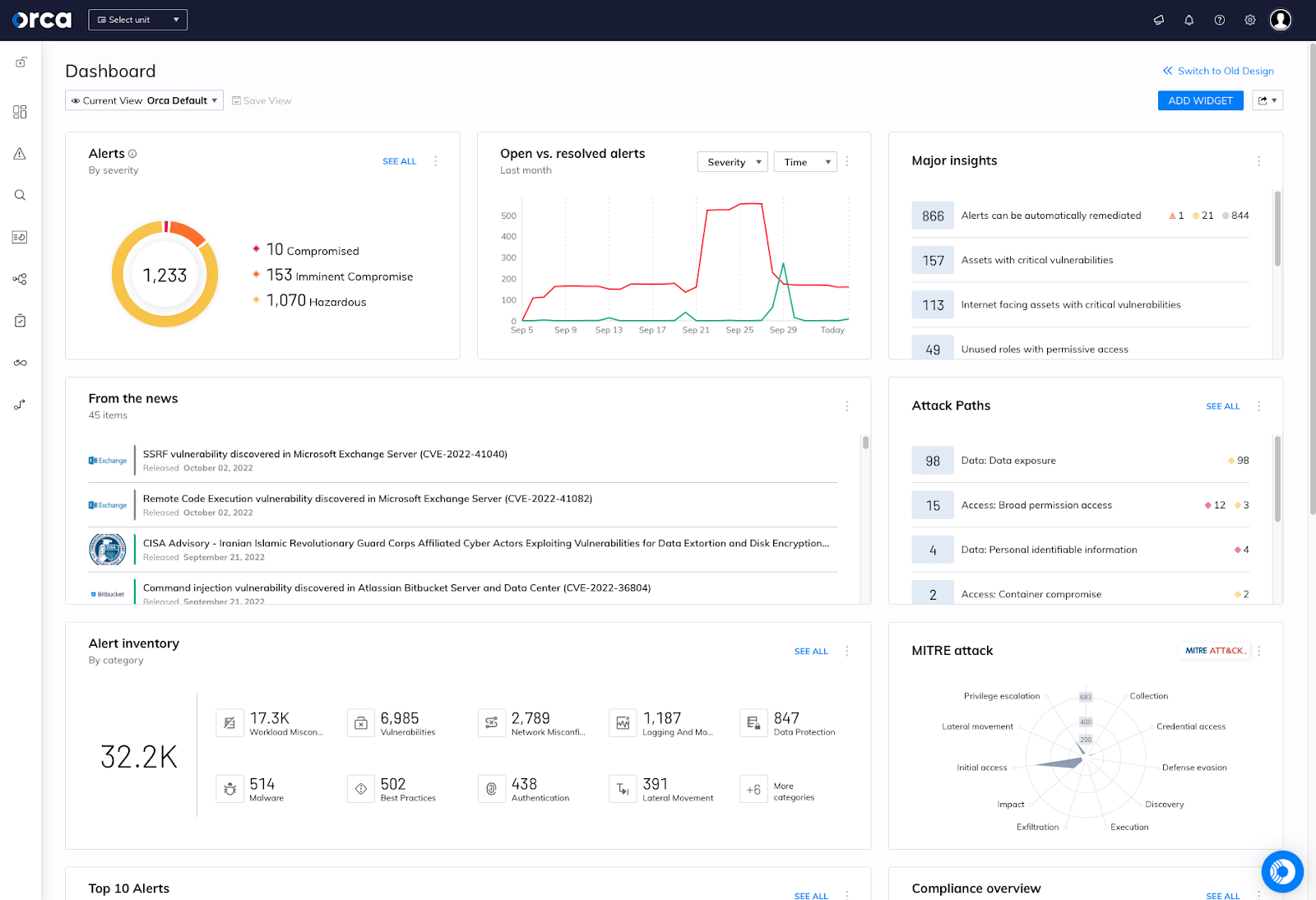
Users can leverage the new Orca Default dashboard, create their own unique Risk Dashboard view, and even share views among team members. To view the Widgets available, simply click View Widget and drag-and-drop the appropriate widgets to place them on the main dashboard.
Updated alert scoring and alert queries
In the cloud, context is a core requirement for prioritizing an environment’s greatest risks and surfacing findings to security teams. Now, the Discovery Search UI provides the ability to query alert findings, just like a user would any cloud asset, CVE, or other critical information.
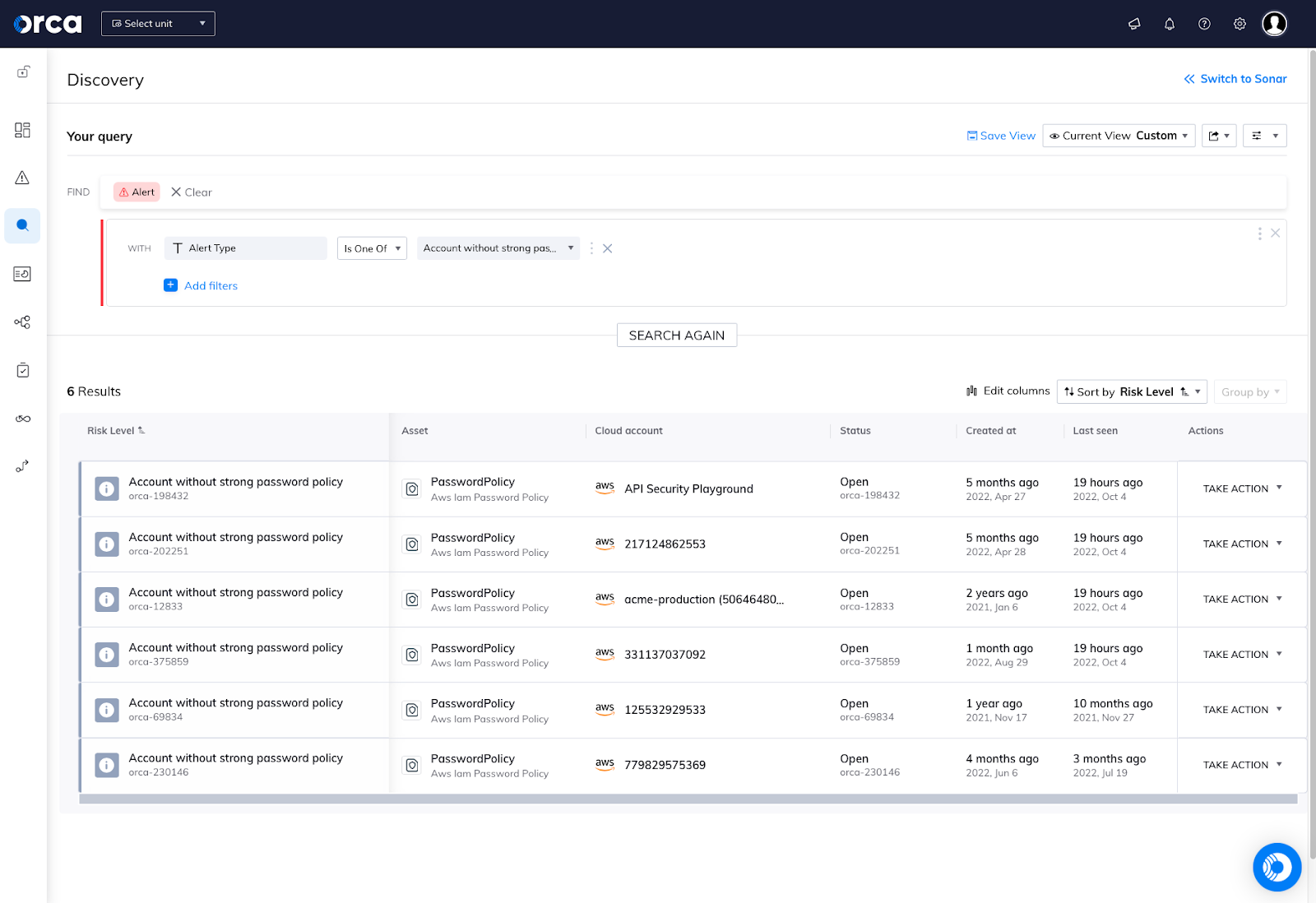
Additionally, each Alert is now scored based on Orca’s proprietary Alert Score to help teams more quickly and easily identify their most critical issues.
Support for Alibaba Cloud
As Orca continues to deliver comprehensive coverage for customers, we’re proud to officially support Alibaba Cloud as our fourth cloud service provider. With the new support, users can view security findings covering the AliCloud control plane as well as vulnerability information, compliance status, and more for virtual machines (VMs).
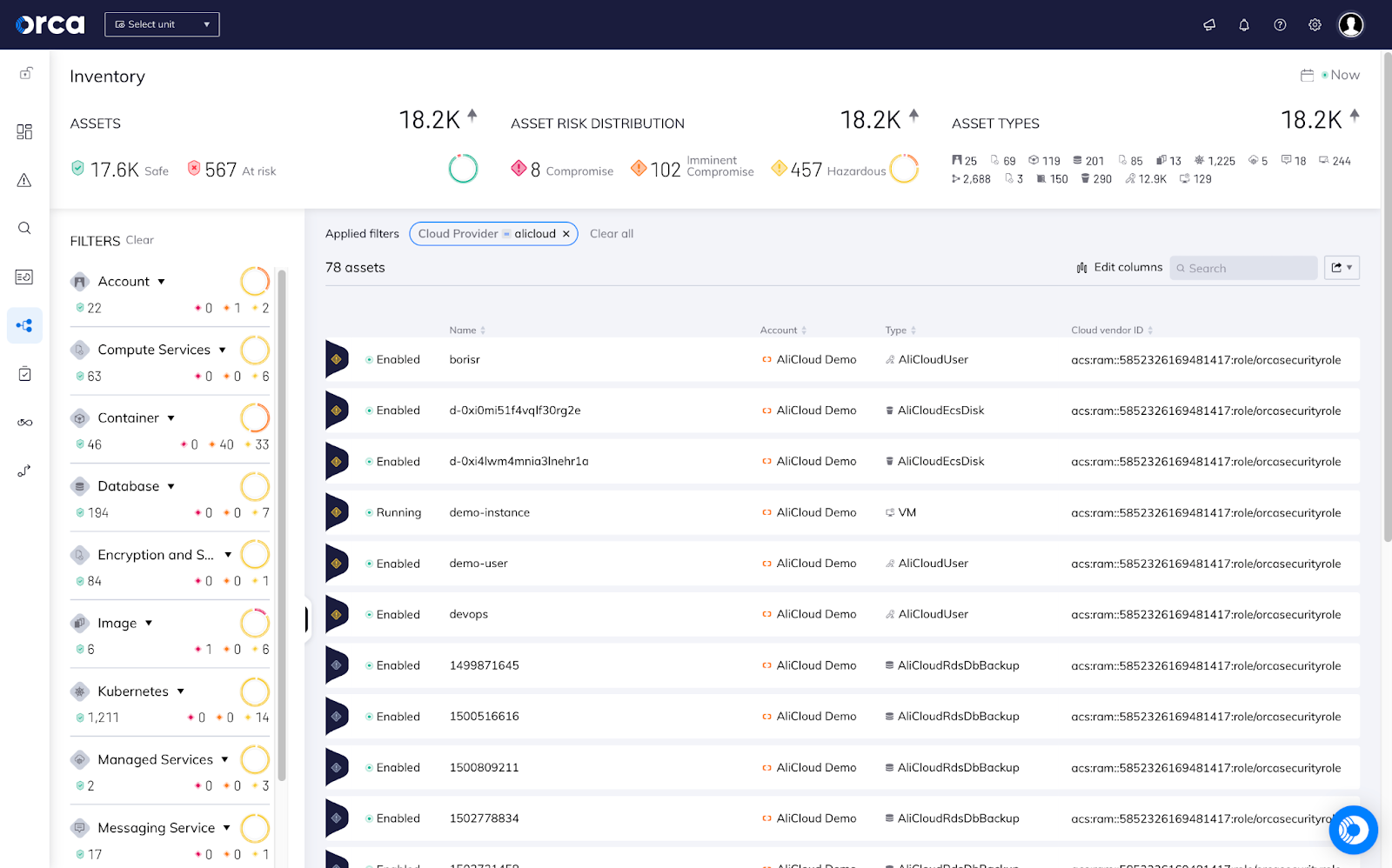
As customers expand globally to deliver best-in-class experiences for their organizations and end users, Orca is committed to supporting new clouds and cloud services. All of the data from Alibaba Cloud can now be viewed next to all of your other assets, as well as support in our main Compliance Dashboard and Discovery Search tab.






